Running OWASP ZAP on Kali Linux 2019.4
06 Jan 2020
Explanation
OWASP ZAP is a web vulnerability scanner that is one of the OWASP projects.
Environment
- OS: Kali linux 2019.4
- OWASP ZAP: v2.8.1
- Target: OWASP Juice shop v9.3.1
Solution
1. Initial setup
Since it’s in the kali official repository, we need just “apt-get”
root@kali:~# apt-get install zaproxyNext, launch the target application.
This time, I used OWASP Juice shop with Vagrant and IP “192.168.33.10” was assigned.
root@kali:~# git clone https://github.com/bkimminich/juice-shop.git
---
root@kali:~# cd juice-shop/vagrant/
root@kali:~/juice-shop/vagrant# vagrant up
---After that give a specific name for OWASP juice shop.
This time, give the following line in “/etc/hosts”.
192.168.33.10 juiceshop2. Other setup
At first, open the ZAP GUI console.
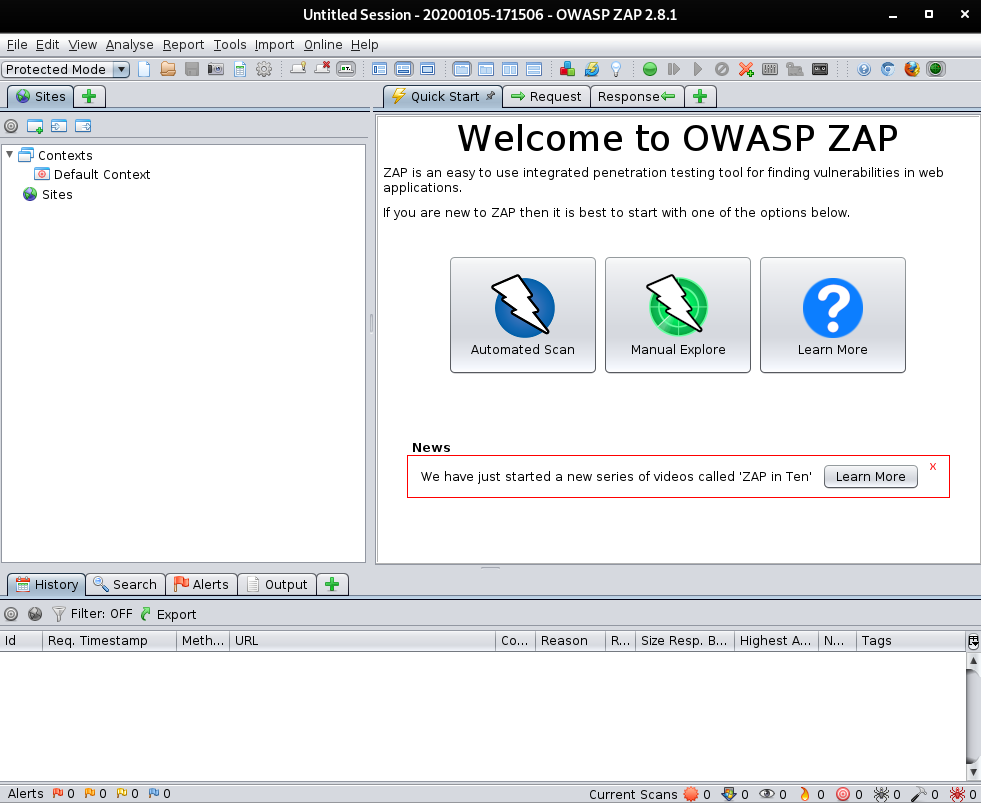
Go to “Tools” -> “Options” -> “Local Proxies”.
By default, it is configured to use “http://localhost:8080”.
We have to configure the web browser to use a proxy on port 8080.
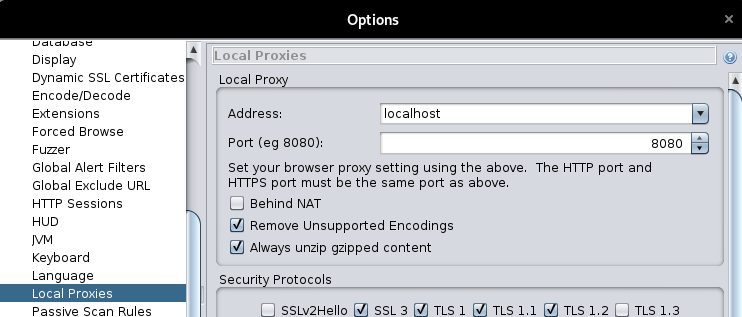
Then, change the mode to the “Protected mode” not to implement unintended attack.
If we select the “Protected mode”, we have to specify the target URL.
The web browser we use should be Firefox because it does not have any XSS protection.
However, this time, Google Chrome was used.
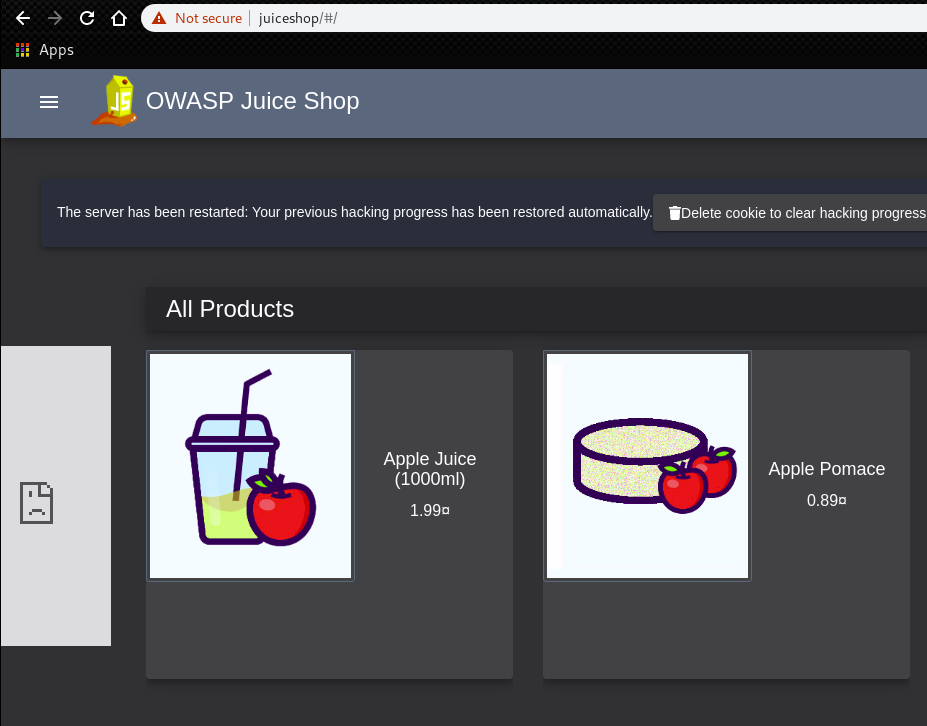
If the configuration is correct, we can find the target URL in the “Site” section.
This means now we can go to the next step.
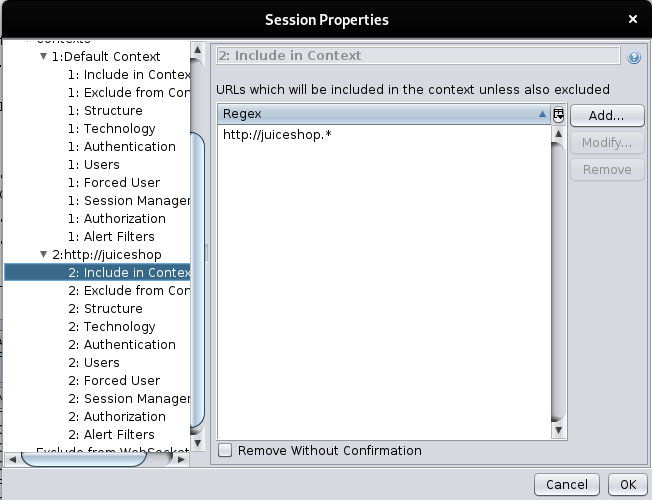
Since we’re using protected mode, we have to include the site into the “context”.
We need to right click the site, then go to “Include in Context”.
This time, we don’t have any context so click the “New Context” and we can see this window.
So click “OK”.
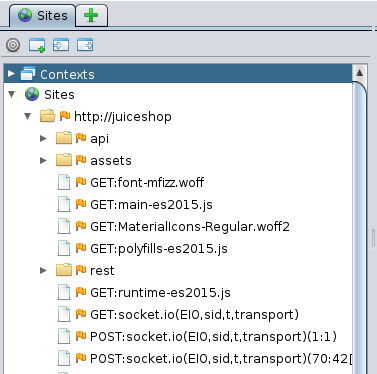
After that, we can see that some entries are added to the site.

3. Active scanning
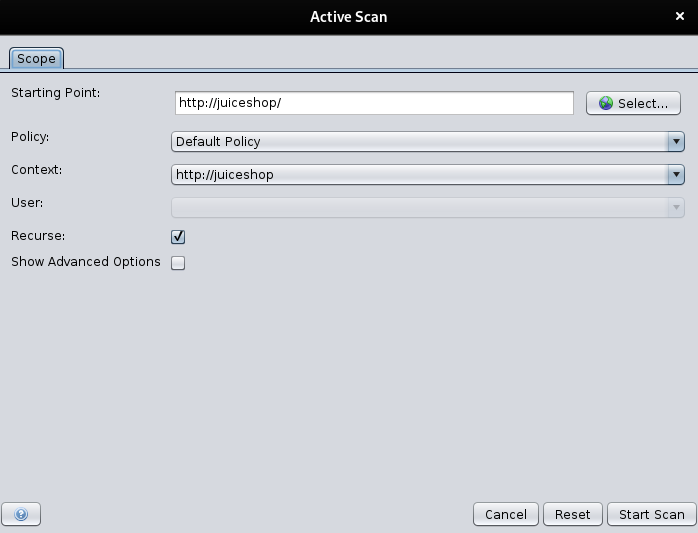
Now we have a target machine.
Try to attack by right clicking the “http://juiceshop” -> “Attack” -> “Active Scan”.
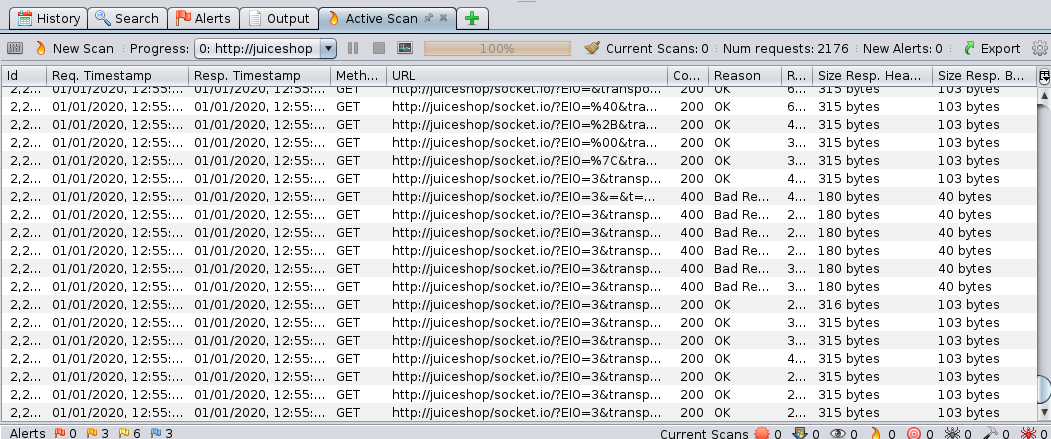
We can confirm that tons of HTTP requests were being sent on the “Active Scan” tab.
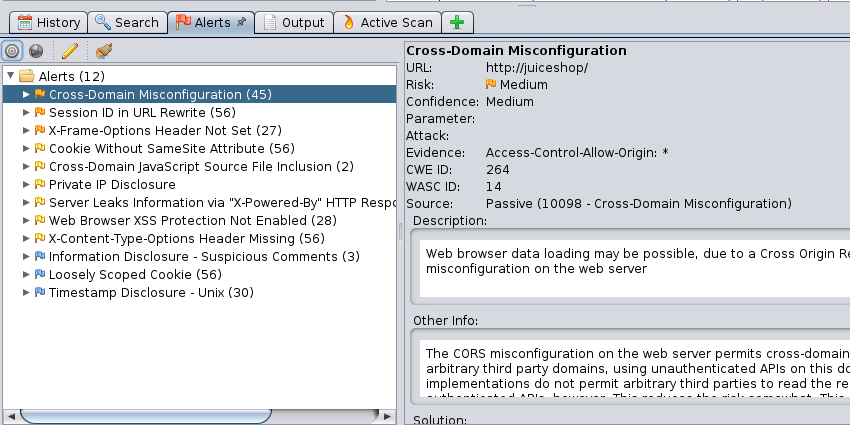
After the finishing, we can find some security alerts on the “Alerts” tab
4. Saving the session
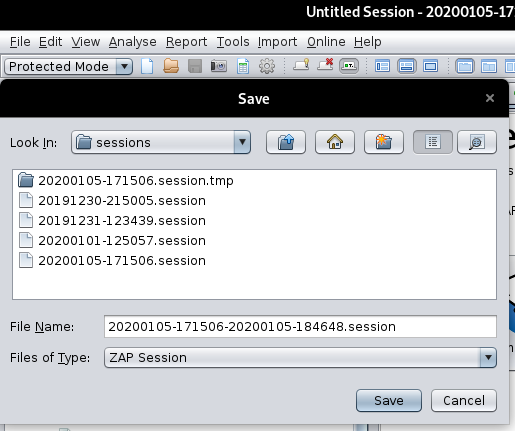
We can save the session data by going to “Snapshot Session As…”, we cam save the current session.
5. Generate a report
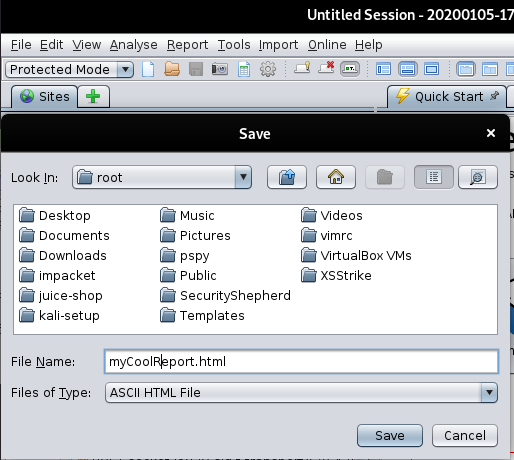
We can create a report of the each test as HTML or XML file.
Go to “Report” -> “Generate HTML Report…”.
6. Next task
This time, I could not find some vulnerabilities that OWASP juice shop has.
Next time, try to focus on each vulnerability and by customizing policies, achieve this purpose