Summary / MITRE ATT&CK
04 Feb 2020
Explanation
To dig into the enterprise level information security knowledge (Meaning not a CTF or something like that !!),
summarize the security framework “MITRE ATT&CK”.
Last Update
2020/02/04
Solution
1. Who published it?
The MITRE Corporation is an American not-for-profit organization based in Bedford, Massachusetts, and McLean, Virginia.
2. When it was published?
Started 2013 and updated every quarter.
3. Why it is important?
- There used to be no common frameworks for consulting, penetration test, SOC that is for both attack side and defence side.
- The ATT&CK framework has become widespread rapidly in the security product industry since approximately 2018.
4. What is the “MITRE ATT&CK” ?
“MITRE ATT&CK” is a cybersecurity framework which stands for “Adversarial Tactics, Techniques, and Common Knowledge”.
They use matrix for the describing each attack method. The followings are the matrix they have
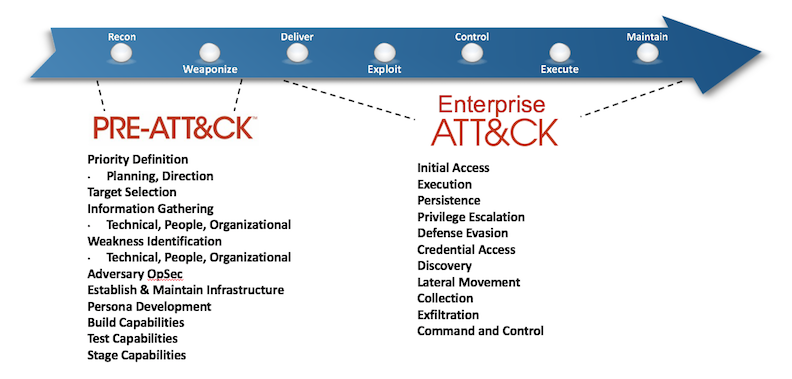
What we have to care is “Enterprise” is mostly for the post-exploitation while Pre-ATT&CK is for the recon, weaponization and delivery.
- Enterprise Matrix
- Mobile Matrix
- Pre-ATT&CK Matrix
The following model explains what “PRE-ATT&CK” and “ATT&CK” cover.
To explain a bit more, this time I use the “Enterprise Matrix”.
The following is the part of Enterprise Matrix.
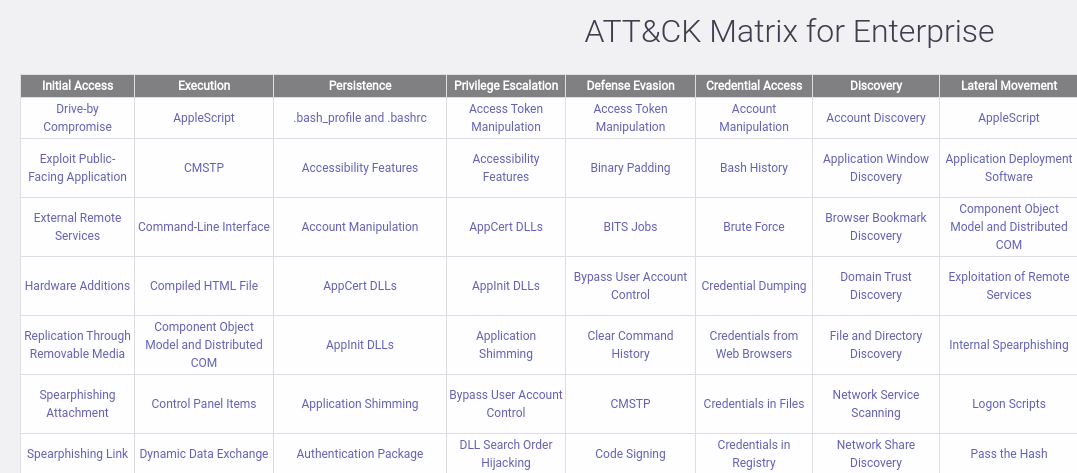
We have 3 keyword for this matrix.
- Tactics : The header of the matrix. Separated as sub categories.
- Techniques : The body of the matrix. Attack techniques / Attack vectors for the each Tactics.
- Mitigations : Mitigation for the attack methods.
Then, go to each Techniques.
This time, the example is “Execution through API”.
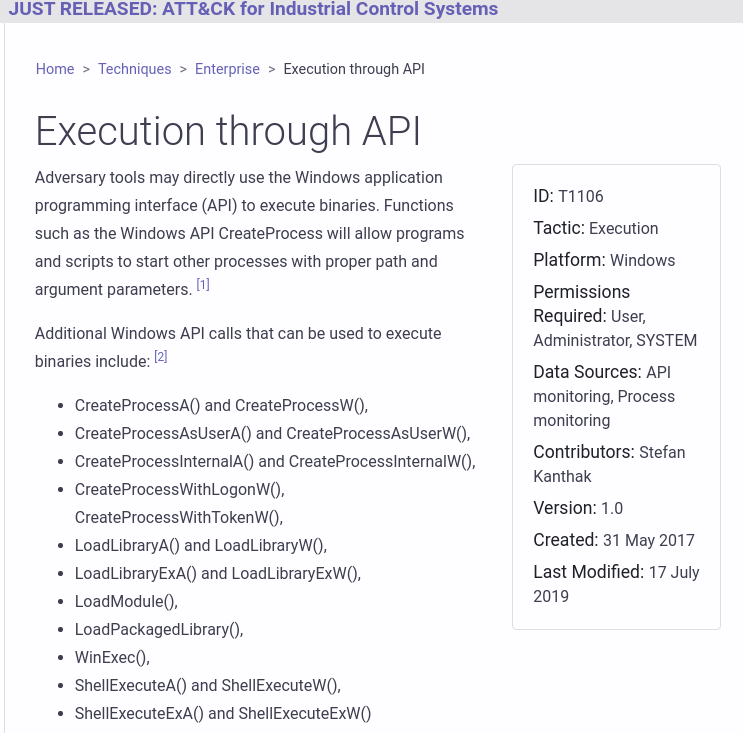
Each Techniques has the following information.
- General description
- Procedure examples : What Adversary groups / tools have leveraged this Technique.
- Mitigations : How to mitigate the risk of this Technique.
- Detection : How to detect this Technique.
- References
5. What we can do with “ATT&CK” ?
On the document “MITRE ATT&CK™: Design and Philosophy”, we have the following use case of ATT&CK.
1. Adversary Enumeration
ATT&CK can be used as a tool to create adversary emulation scenarios to test and verify defenses against common adversary techniques.
2. Red Teaming
ATT&CK can be used as a tool to create red team plans and organize operations to avoid certain defensive measures that may be in place within a network.
3. Behavioral Analytics Development
ATT&CK can be used as a tool to construct and test behavioral analytics to detect adversarial behavior within an environment.
4. Defensive Gap Assessment
ATT&CK can be used as a common behavior-focused adversary model to assess tools, monitoring, and mitigations of existing defenses within an organization’s enterprise.
5. Soc Maturity Assessment
ATT&CK can be used as one measurement to determine how effective a SOC is at detecting, analyzing, and responding to intrusions.
6. Cyber Threat Intelligence Enrichment
ATT&CK is useful for understanding and documenting adversary group profiles from a behavioral perspective that is agnostic of the tools the group may use.
6. Tools / Resources
1. Simulators of testing “ATT&CK” implementation.
-
Uber Metta
Tutorial: https://medium.com/uber-security-privacy/uber-security-metta-open-source-a8a49613b4a -
MITRE Caldera
Website: https://www.mitre.org/research/technology-transfer/open-source-software/caldera
Video tutorial:
-
Red Canary atomic Red Team
Website: https://redcanary.com/atomic-red-team/ -
Endgame Red Team Automation
Website: https://www.endgame.com/blog/technical-blog/introducing-endgame-red-team-automation
2. Documents of log expected result of testing “ATT&CK” implementation.
-
MITRE Cyber Analytics Repository
Analytics based on the MITRE ATT&CK adversary model. -
Palo Alto Unit 42 Playbook Viewer
Free playbook based on ATT&CK by Palo Alto Unit 42. -
Malware Archaeology Windows ATT&CK Logging Cheat Sheet
Document explains what happens when Windows server logs being attacked.
3. Other Tools / Documents / Videos
-
ATT&CK navigator
Navigation and annotation of the ATT&CK for each matrix.
Video tutorial:
7. FAQ
8. Conclusion
Please someone give me a correction if there is an incorrect description or lacking information!!
