MalwareTech Beginner Malware Reversing Challenges Strings3 Writeup
13 Feb 2019Environment
- Host OS: Kali linux 2018.4
- Guest OS: Windows 7 Home Basic
- Virtualization: Virtualbox 5.2.22
- Debugger: IDA Pro 7.0
- Other: Resource Hacker v5.1.7
Explanation
We have several malware reversing challenges this page on MalwareTech
This is a write-up of “Strings3”.
strings3.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original. Can you extract the flag?Solution
1. Opening with IDA and Resource Hacker
Let’s open the strings3.exe with IDA and search for the flag.
According to the strings windows, it looks like we don’t have any encrypted flag.
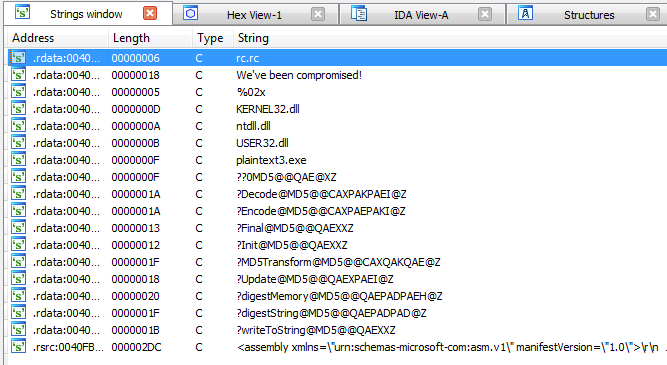 Then, what we can guess is that this executable is loading the flag from somewhere else.
Then, what we can guess is that this executable is loading the flag from somewhere else.
We can use “Resource Hacker” to figure out “Hidden” resources on IDA.
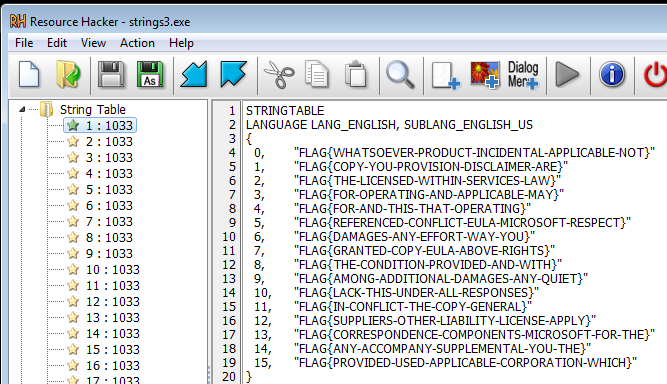 As we can see, there are too many “Possible flags” and we still have to figure out which is the correct password.
As we can see, there are too many “Possible flags” and we still have to figure out which is the correct password.
2. Identify the correct flag
To identify the correct flag, we can take advantage of these functions.
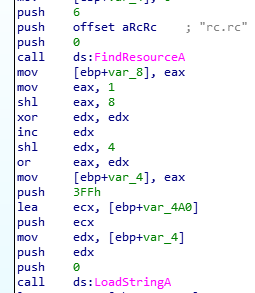 According to the official document of “LoadStringA” function, it takes 4 arguments.
According to the official document of “LoadStringA” function, it takes 4 arguments.
int LoadStringA(
HINSTANCE hInstance, // A handle to an instance of the module whose executable file contains the string resource.
UINT uID, // The identifier of the string to be loaded.
LPSTR lpBuffer, // The buffer to receive the string or a read-only pointer to the string resource itself.
int cchBufferMax // The size of the buffer, in characters.
);This means, in strings3.exe, LoadStringA is called like this
int LoadStringA(0, edx, ecx, 0x3FF)Sounds like we have to figure out what’s the value of edx.
To figure out this, we have to focus on following instructions.
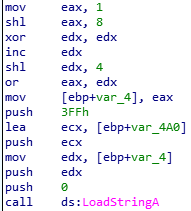 Let’s see valus of eax and edx.
Let’s see valus of eax and edx.
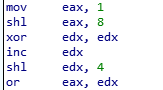 We can figure out the value of each register by python interpreter.
We can figure out the value of each register by python interpreter.
root@kali:~# python
Python 2.7.15+ (default, Feb 3 2019, 13:13:16)
[GCC 8.2.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> 1 << 8 # shl edx, 8
256
>>> 1 << 4 # shl eax, 4
16
>>> 256 | 16 # or eax, edx
272
>>> According to this, after the “or eax, edx” instruction, the value of eax is 272.
This value is stored in [ebp+var_4]. Then it is moved to edx.
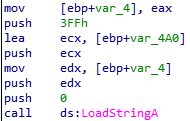 So the value of edx which is argument of LoadStringA is “272”.
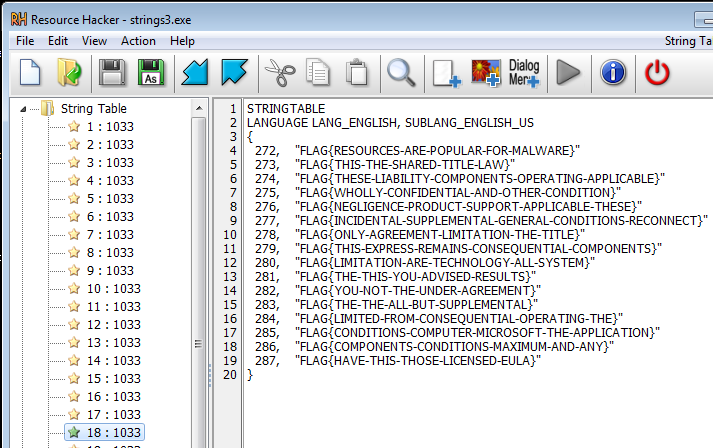
if we look at num 272 of string table, we can find the correct flag.
So the value of edx which is argument of LoadStringA is “272”.
if we look at num 272 of string table, we can find the correct flag.