MalwareTech Beginner Malware Reversing Challenges Strings2 Writeup
12 Feb 2019Environment
- Host OS: Kali linux 2018.4
- Guest OS: Windows 7 Home Basic
- Virtualization: Virtualbox 5.2.22
- Debugger: IDA Pro 7.0
Explanation
We have several malware reversing challenges this page on MalwareTech
This is a write-up of “Strings2”.
strings2.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original. Can you extract the flag?Solution
1. Opening with IDA
When we open the strings2.exe with IDA, we can get following lots of variables.
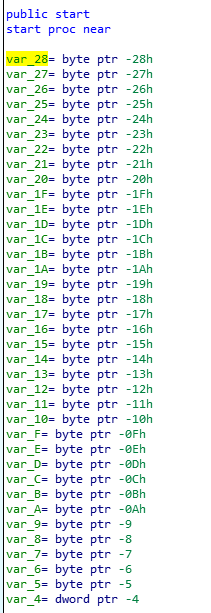 Then, bunch of mov instructions are following.
Then, bunch of mov instructions are following.
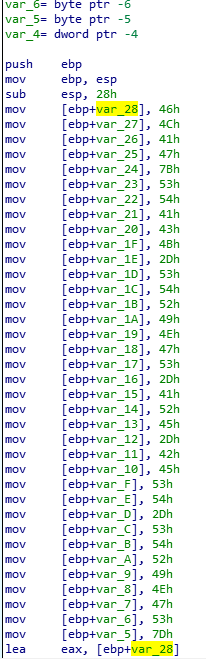 Because there is “h” trailing, we can figure out these are hex numbers.
Because there is “h” trailing, we can figure out these are hex numbers.
2. Translate hex to ascii
We can write a python script which translates there hex codes to ascii characters.
root@kali:~# cat strings2.py
#! /usr/bin/python3
import binascii
HEX = '464C41477B535441434B2D535452494E47532D4152452D424553542D535452494E47537D'
def main():
print(binascii.a2b_hex(HEX))
if __name__ == "__main__":
main()Let’s execute the python script.
We can grab the flag for this challenge.
root@kali:~# ./strings2.py
b'FLAG{STACK-STRINGS-ARE-BEST-STRINGS}'