MalwareTech Beginner Malware Reversing Challenges Strings1 Writeup
10 Feb 2019Environment
- Host OS: Kali linux 2018.4
- Guest OS: Windows 7 Home Basic
- Virtualization: Virtualbox 5.2.22
- Debugger: IDA Pro 7.0
Explanation
We have several malware reversing challenges this page on MalwareTech
This is a write-up of “Strings1” on that website.
strings1.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original. Can you extract the flag?Solution
1. Opening with IDA
Sounds like we have to find an un-encrypted flag from one windows executable file strings1.exe.
As written on the challenge web page, we don’t need to run the executable.
By opening with IDA, we can see the overal structure.
 To find a strings, we can go to Strings window.
To find a strings, we can go to Strings window.
(View->Open Subviews->Strings or Shift+F12).
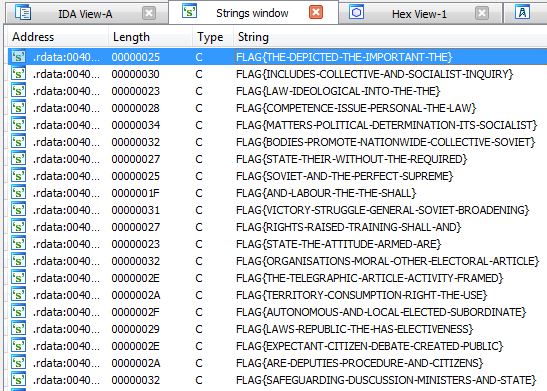 As we can see, we have too many numbers of possible flags.
As we can see, we have too many numbers of possible flags.
2. Analysing assembly code
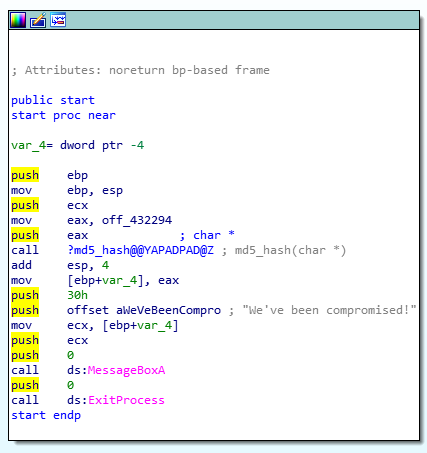
 By reading the disassembly code, we can find that after a few lines of standard instructions, we have these instructions below.
By reading the disassembly code, we can find that after a few lines of standard instructions, we have these instructions below.
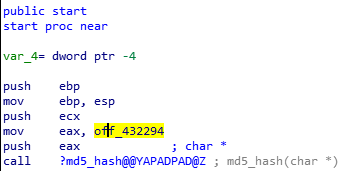
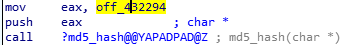 looks like it is hashing the characters in off_432294.
looks like it is hashing the characters in off_432294.
By double clicking the operand, we can see the value of the address.
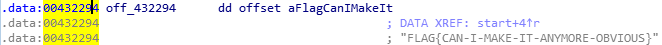 This is the flag which we have to find.
This is the flag which we have to find.