Reversing.kr Image Prc Writeup
27 Dec 2018Environment
- Host OS: Kali linux 2018.4
- Guest OS: Windows 7 Service Pack 1
- Virtualization: Virtualbox 5.2.22
- Debugger: IDA Pro Free 5.0
- PE header viewer: PEview 0.9.9
- Hex Editor: HxD 2.0
Explanation
Reversing.kr is a website which has some of reverse engineering challenges. This is a write-up of ImagePrc on that website.
Solution
1. Running the app
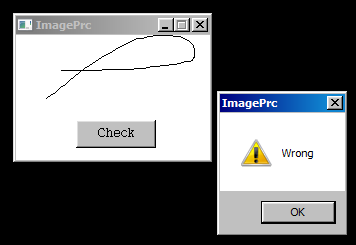
When we run the app, we have a small dialogue.
What we can do are just writing something on the bitmap and put the ‘check’ button. When we put check button, another window pops up and shows message ‘wrong’.
2. Consideration
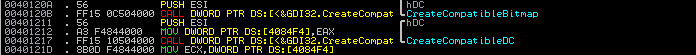
It is easy to figure out the point this application creates a bitmap. What we need is we have to look for the point “CreateCompatibleBitmap” Windows API is used.
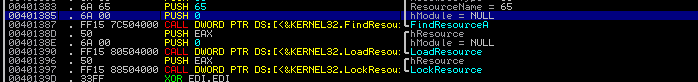
After sat a breakpoint and run the instruction one by one, we can find a place Loading 2 resources. We can easily determine this because “LoadResource” Windows API is being executed and these resource files are loaded and compared.
In the specified address, we can see many lines of “FFFF”.
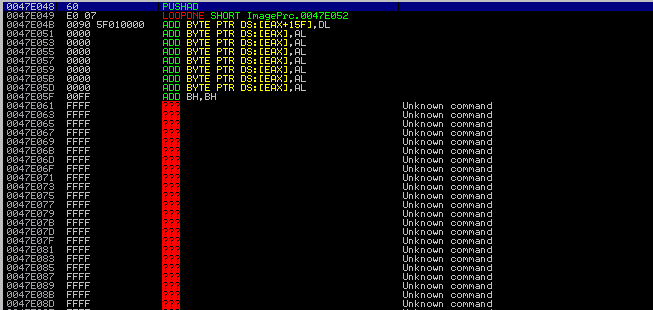 We can assume this is BMP image file included in the exe file. This is because
We can assume this is BMP image file included in the exe file. This is because
- This has to be an image file
- There are a lot of number of “FF” which means white in bmp file.
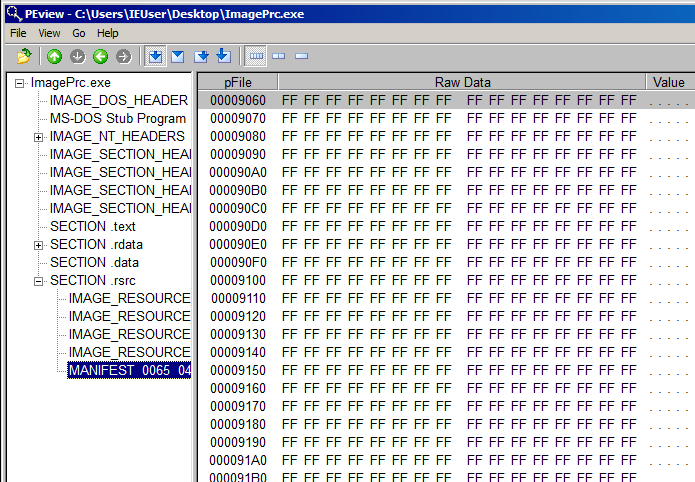
3. Analyzing PE header
To analyze this exe file, we can use PEview.exe
In section .rsrc, MANIFEST 0065 0412, there is a bmp format image file
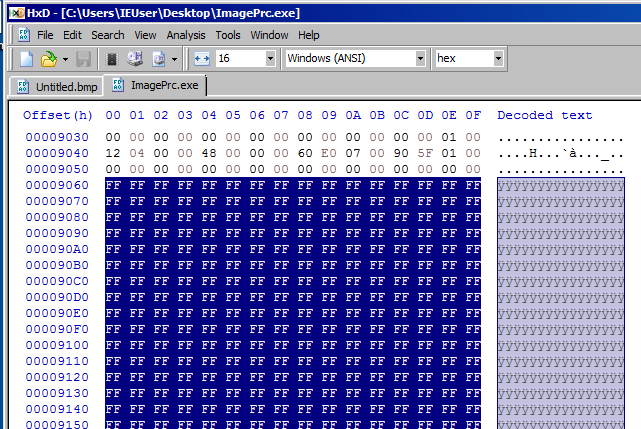
 To see this image file, we have to create a new BMP image whose size is 200x150 and open it with HxD hex editor.
In addition, we have to create a blank BMP image file which has same size.
We have to copy lines from 9060 to the bottom and replace the body of the new BMP file.
To see this image file, we have to create a new BMP image whose size is 200x150 and open it with HxD hex editor.
In addition, we have to create a blank BMP image file which has same size.
We have to copy lines from 9060 to the bottom and replace the body of the new BMP file.
 Once we open the modified image file, we can get this image below.
Once we open the modified image file, we can get this image below.
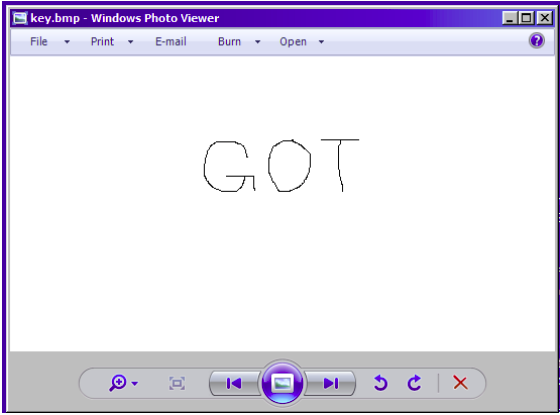 Now we know the password for this challenge is “GOT”.
Now we know the password for this challenge is “GOT”.